

2021-12-27 15:37:00
Fabian Faessler, aka LiveOverflow, runs a wonderful YouTube channel where he explains all kinds of InfoSec and other hacking related topics. I'm a huge fan of his two-part explanation of the recent Log4j vulnerability.
We've seen plenty of proofs-of-concept and rehahshes of JNDI-problems. In his video, Fabian instead delves into the matter of how we even got into this mess.
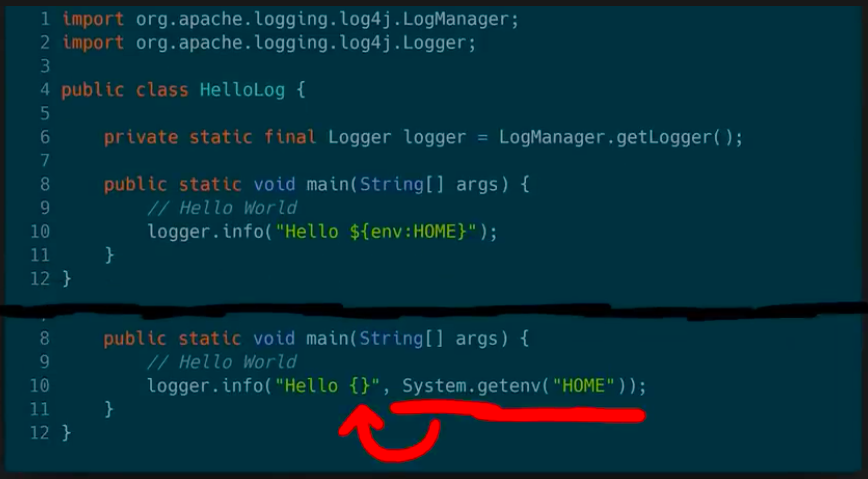
The screenshot above is from part 2. It asks developers the honest question: what would have been better, more secure? Do we want a logging solution which can resolve arbitrary variables and macros? Or should we have a plain logger, which needs to be spoon-fed what it needs to log?
In secure design, we should always choose for option B. But I guess that historically "features" and "shiny factor" won over "basic design".
If you have half an hour, I suggest you grab some coffee and go give this series a watch!
kilala.nl tags: work, security, studies,
View or add comments (curr. 0)
All content, with exception of "borrowed" blogpost images, or unless otherwise indicated, is copyright of Tess Sluijter. The character Kilala the cat-demon is copyright of Rumiko Takahashi and used here without permission.