

2009-10-25 15:59:00

Boiling it down to one sentence one can say that BoKS enables you to centraly manage user accounts and access permissions, based on Role Based Access Control (RBAC).
The following article is also available as a PDF.
BoKS Access Control is a product of the Swedish firm FoxT (Fox Technologies), intended for the centralized management of userauthentication and authorization (Role Based Identity Management and Access Control). The name is an abbreviation of the Swedish "Behörighet- och KontrollSystem", which roughly translates as "Legitimicy and Control System".
Some key features of BoKS are:
Using BoKS you decide WHEN WHO gets to access WHICH servers, WHAT they can do there and HOW.
BoKS is a standalone application and requires no modifications of the server or desktop operating systems.
BoKS groups users accounts and computer systems based on their function within the network and the company. Each user will fit one or more role descriptions and each server will be part of different logical host groups. One could say that BoKS is a technical representation of your company's organisation where everyone has a clearly defined role and purpose.
Let us discuss a very simple example, based on a BoKS server, an application server and a database server.
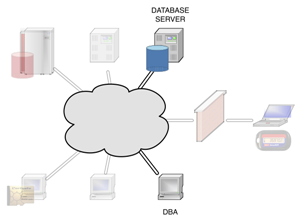
|
Your database admins will obviously need access to their own work stations. Aside from that they will be allowed to use SSH to access those servers in the network that run their Oracle database. Because BoKS is capable of filtering SSH subsystems, the DBAs will get access to the command line (normal SSH login) and to SCP file transfer. All other SSH functions (like port forwarding, X11 tunneling and such) will be turned off for their accounts. Using the BoKS Oracle plugins your DBAs accounts will also be allowed to administer the actual databases running on the server. |
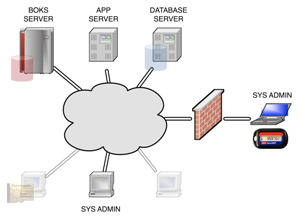
|
The sysadmins will be allowed full SSH access from their work stations to all of the servers in the network. Aside from their own user accounts they will also be allowed to login using the superuser account, but that will be limited to each server's console to limit the actual risk of abuse. Because the system administrators are expected to provide 24x7 support they will also be allowed to create a VPN connection to the network, through which they can also use SSH. However, this particular SSH will only work if they have authenticated themselves using an RSA token.
To ensure a seperation of duties the system administrators will not be allowed access to any of the applications or databases running on the servers. |
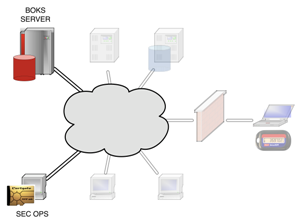
|
The actual users of BoKS, security operations, will gain SSH access to the BoKS security server. Aside from that they will also be allowed access to the BoKS web interface, provided that they've identified themselves using their PKI smart card. |
Centralized management of user accounts
No longer will you have to locally create, modify or remove user accounts on your servers. BoKS will manage everything from it's central security server(s), including SSH certificates, secondary Unix groups and personal home directories.
Centrally defined access rules
Users will only be allowed access to your computer systems based on the rules defined in the BoKS database. These rules define permissable source and destinations systems as well as the (time of) day and the communications protocols to be used.
Role based access control
Access rules can be assigned both to individual users as well as to roles. By defining these user classes you can create and apply a set of access rules for a whole team or department in one blow. This will save you time and will also lower the risk of human error.
Extensive audit logging
Every authentication request that's handled by BoKS is stored in the audit logs. At all times will you be able to see what's happened in your network. BoKS also provides the possibility of logging every keystroke performed by a superuser (root) account, allowing you greater auditing capabilities.
Real-time monitoring
The BoKS auditing logs are updated and replicated in real-time. This allows you to use your existing monitoring infrastructure to monitor for undesired activities.
Support for most common network protocols
BoKS provides authentication and authorization for the following protocols: login, su, telnet, secure telnet, rlogin, XDM, PC-NFS, rsh and rexec, FTP and SSH. The SSH protocol can be further divided into ssh_sh (shell), ssh_exec (remote command execution), ssh_scp (SCP), ssh_sftp (SFTP), ssh_x11 (X11 forwarding), ssh_rfwd (remote port forwarding) and ssh_fwd (local port forwarding).
Delegated superuser access
Using "suexec" BoKS allows your users to run a specified set of commands using the superuser (root) account. Suexec access rules can be specified on both the command and the parameter level, allowing you great flexibility.
Integration with LDAP and NIS+
If so desired BoKS can be integrated into your existing directory services like LDAP and NIS+. This enables you to connect to automated Human Resources processes involving your users.
Redundant infrastructure
By using multiple BoKS servers per physical location you will be able to provide properly load balanced services. Your BoKS infrastructure will also remain operable despite any large disasters that may occur. Disaster recovery can be a matter of minutes.
| OpenLDAP | eTrust AC | BoKS AC | |
| Centralized authentication management | Y | Y | Y |
| Centralized authorization management | Y (1) | Y | Y |
| Role based access control | N | Y | Y |
| SSH subsysteem management | N | N | Y |
| Monitoring of files and directories | N | Y | Y |
| Access control on files and directories | N | Y | N |
| Delegated superuser access | Y (2) | Y | Y |
| Real-time security monitoring | Y (3) | Y | Y |
| Extensive audit logging | N | Y | Y |
| OS remains unchanged | Y | N | Y |
| User-friendly configuration | N | Y | Y |
| Reporting tools | N | Y | Y |
| Password vault functionality | N | Y | Y (4) |
1: Only for SSH.
2: Using additional software.
3: Locally, using syslog.
4: Using the optional BoKS Password Manager module.
kilala.nl tags: boks, sysadmin,
View or add comments (curr. 11)
Posted by Thomas
Since Tom's comment sounds an awful lot like "comment spam", I've asked him to reword his message.
Posted by Thomas
Since Tom's comment sounds an awful lot like "comment spam", I've asked him to reword his message.
Posted by Max
BoKS actually came from DynaSoft from Stockholm. Back in 1998 they were bought by Security Dynamics (Now RSA and themselves part of EMC) for the smart card technology.
I used to work as pre/post sales support for DynaSoft UK back in those days. Good to know BoKS is still going.
Posted by Thomas
Hey Max,
Thanks for that additional explanation. The guys from TFS always told me that the company was called TFS before being bought by RSA, but I guess that was wrong. Thanks for your update! :)
Posted by Asif
Hi,
I'm a fairly n00b on the BoKS system, our resident expert just went through a major upgrade to 6.5.2 and the resulting design is not as efficient as I would like it to be but then what do I know at this point. So I'm going along with the new design where we have more host groups then users and servers but that is not why I'm posting here. The real reason I'm posting here is because we are in the middle of a big deployment of RSA EnVision security event management solution and I have been told "repeatedly" by the resident BoKS expert that BoKS cannot forward it's audit logs using the standard log forwarding e.g. syslog, snmp etc. Anyone here or Cailin yourself can offer me any help or just point me in the right direction? I'm very impressed with the product and the logging it provides would be invaluable for corelating data from other security systems and give us the visibility into our systems that we currently do not have. Any assistance would be greatly appreciated!
Thanks,
-Asif
Posted by Thomas
Hi Asif,
Could I please ask you to post your question in the "BoKS users group" on LinkedIn.com? I think you'll reach more people over there and I think that was your original intention.
You will find the group over here -> http://www.linkedin.com/groups?gid=1077637
Thanks! :)
Posted by Thomas
Just to think along with you Asif, your expert is right insofar that BoKS doesn't use normal syslog or SNMP to transfer their logs. However, there is nothing stopping you to install or write another app that parses the logs on the BoKS server so it gets sent to EnVision. At $CLIENT we did the same thing...
Posted by ARRUMAC
Asif,
I send BoKS logs to a third party vendor event management system on an hourly basis. I am happy to consult. Currently I am responsible for many clients, in several domains all BoKS 6.5.2.
Posted by Thomas
Oh yeah, I'm told that BoKS stands for "Behorigkeit og Kontrol System", although my spelling might be off a bit.
Posted by Afsaneh Arman
BoKS stand for "Behörighet och Kontrol System" in Swedish meaning Legitimacy and Control System.
All content, with exception of "borrowed" blogpost images, or unless otherwise indicated, is copyright of Tess Sluijter. The character Kilala the cat-demon is copyright of Rumiko Takahashi and used here without permission.
2007-10-08 23:06:00
Posted by Tom Russo (website)
We are here at FoxT to answer any questions about BoKS - Now called FoxT Server Control. My name is Tom Russo and I am an Account Executive for FoxT in Atlanta. Please feel free to email me if you have questions or comments regarding our solutions. We are also in the process of formulating and implementing a 'User Forum' for BoKS users to share best practices etc. Please feel free to contact me anytime at 404.202.0117 if I can be of any assistance using BoKS or any other FoxT solution.