

2009-11-02 17:02:00
Seriously, this was waiting to happen: Teenager "hacks" jail broken iPhones. The security hole is glaringly obvious and has been proven and verified by some of my security-expert acquaintances. And now, obviously, it's out in the open. Personally I wonder how the heck it took so long for this to happen.
The hole: jail broken iPhones often run an SSH daemon, allowing their owners access to the phone's operating system. Most of these owners unfortunately never change the default root password, thus giving anyone 100% access to their phones. I really don't understand why nobody has ever pushed this issue before.
The steps are painfully easy.
1. Do a port scan on T-Mobile's 3G IP range, looking for SSH servers.
2. Try to login as root using the default alpine password.
3. Install your root kit / malware / hostage message.
4. Ask that people send you five euros for the free "fix".
5. PROFIT!
The fix in question is also plainly, fscking obvious: change your root password (asshole)! The "hacker" in question says it's safe to just remove two files he installed and to change your password, but personally I'd do a completely clean wipe. There's no telling if anyone's left anything else as a present.
Some links:
* The topic at GoT that started it all.
* The original hostage website
EDIT:
My pessimistic prediction for this week: the mainstream press will pick up on the story, misunderstand the issue and put the blame on Apple. Many geeks will try to diffuse the situation and explain that the fault lies with people who were mucking with things they don't understand, but their pleas will fall on deaf ears.
EDIT 2:
So I was wrong in one regard: this exploit -has- both been abused and reported before. How about December 2008 and July 2008? So, the only thing all of this really proves is that people in general don't listen and they don't learn.
kilala.nl tags: apple, sysadmin,
View or add comments (curr. 5)
Posted by Thomas
For posterity, here's the fix that you could buy for five euros:
====================================
Ok plan's changed. Here's what to do, good luck and contact me if you have any questions
1. Get an SSH program like putty for windows.
2. SSH to your iPhone. (If you haven't done that before it may take a while, and after that there might come a warning about a key fingerprint. You can just accept that). Login using username "root" and password "alpine". (this is the default password)
3. There's a few commands you have to execute, best is to just copy them:
rm /System/Library/LaunchDaemons/com.apple.syslog.plist
chown mobile /private/var/mobile/Library/LockBackground.jpg
chmod 666 /private/var/mobile/Library/LockBackground.jpg
mv /private/var/mobile/Documents/LockBackground.backup.jpg /private/var/mobile/Library/LockBackground.jpg
4. That's everything to remove my stuff. Now there's one command left to make sure this won't happen again! (-; Again in putty or any ssh client type: "passwd". You'll then be asked for a new password, you can change this into anything you want. The safer the better of course (:
The reason you have to change this password is that it's default is alpine at ALL iPhones. So if anyone knows that (and all hackers do) they can access your iPhone. Now you've changed it this isn't possible anymore!
If you have any questions or something, mail me and I'll try to answer them!
PureInfinity92@mailinator.com (oh and btw the program is designed to remove itself so you should already be clear)
Posted by Thomas
It's when you modify the software in the iPhone in such a way that the phone will do things Apple never intended. It will also let you run software not available through normal methods and will also let you run copied, official software without paying for it. Some people who "jail break" their iPhones are simply looking for more "freedom" and extra functions, others are just cheap *#$%!.
All content, with exception of "borrowed" blogpost images, or unless otherwise indicated, is copyright of Tess Sluijter. The character Kilala the cat-demon is copyright of Rumiko Takahashi and used here without permission.
2009-11-02 17:14:00
Posted by Thomas
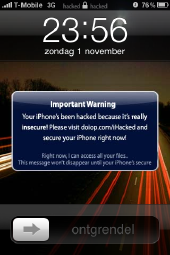
For posterity, here's the original hostage message:
====================================
Dear iPhone user,
Your iPhone is not secure. That's the reason your visiting this page, isn't it? Well you can pay me $4,95 at my paypal account PureInfinity92@mailinator.com, and I'll mail you very easy instructions on how to secure your iPhone. You can also contact me at
PureInfinity92@gmail.com
If you don't pay, it's fine by me. But remember, the way I got access to your iPhone can be used by thousands of others. And they can send text messages from your number (like I did..), use it to call (or record your calls), and actually whatever they want, even use it for their hacking activities!
I can assure you, I have no intention of harming you or whatever, but, some hackers do! It's just my advise to secure your phone (:
Have a nice day!