2017-10-08 10:29:00
For the third year in a row I competed in the PvIB CTF "Pen.test event", a Jeopardy-style CTF where contestants race to solve puzzles and small hacking challenges. Last year I didn't fare very well at all, but this time aroud things went great! The crowd was nice, my table companions were cool, it was great talking to Anko again and the DJ played awesome beats. I had a blast!
Around 1.5 hours into the competition I went to stretch my legs and get a drink, enjoying the fun we were having. Looking around, sipping on my cola I noticed something odd about the scoreboard! When I'd managed to grab my phonecam I'd already been surpassed by one team, but for at least a short while I'd managed to be in #4 out of the pack of 51 contestants. In the end I finished somewhere halfway , because greater minds than mine managed to keep on scoring points :)
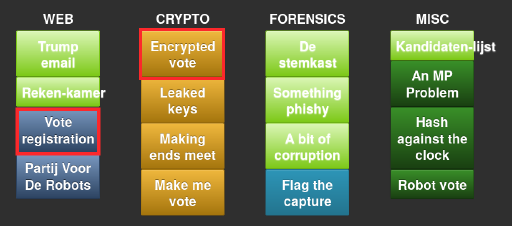
Like before, the challenges were divided into various categories (shown above) and ranked from easy to hard, resulting in different scores per item. I finished the night with 100.000 points (3x10e3, 2x10e4, 1x10e3). I was so, so close on another 10k and 30k points which is why I stuck around until the very last minute!
Web:
- I let myself be fooled by the easy Web challenge for way too long. The challenge presented you with a SquirrelMail login page and the task to login and get their email. Assuming it was a veritable SquirrelMail, I assumed no easy software vulnerabilities would be found, so I resorted to password guessing. An hour before the end of the night, Anko asked me "When we start out web pen testing, what are the things you're taught first?". Me: "Well... I reckon... You mean XSS, CSRF and SQL Injection, right?" A: "Absolutely." Me: "Sonuvabitch...". Turns out it was NOT SquirrelMail, just a quick and easy SQLi exercise made to look like it.
- This challenge sent you to an online calculator which would help the voting committee tally their votes, in this case a basic formula line which would return the outcome. Entering gibberish into the line would return a basic Python EVAL failure. Turns out that it was possible to run OS-commands through the EVAL calculation line, which let me list the remote files and to grab the required flag.
- Both this exercise and #2 were a bit slow to respond in my browser, so I turned to the Lynx text-based browser. This foregoes all CSS, which was being loaded from the Internet. This time around we were supposed to hack a voting system, to find out the vote-total for each candidate. I noticed that it was based on a JSP that got included by URL, so I downloaded it for further analysis. This code showed me that the voting process makes SOAP calls to retrieve candidates and to place a vote. I also gave me examples of the XML data needed for those soap calls. From here on out, my challenge was to find out how to get voting results instead! I haven't worked with SOAP a lot, but I know there had to be some way of querying the remote end for available procedures and commands. This is where I learned about WSDL, which gave me exactly what I needed: a description of how to request voting results. This needed a little bit more tweaking to the XML, because the candidates were identified by an MD5 hash that needed to be updated as binary data. Darn! Was this close to getting the whole challenge, but was a few minutes too late.
Learning on the go was hella fun! I got to renew my experience with CURL calls and XML data and learned new things about SOAP. Nice!
Crypto:
- I'd figured out the positional encryption scheme for this challenge pretty quickly, as it was clearly based on jumping and looping through the ASCII table, based on a character's position. Despite this, I seem to have had some stupid mistake in my method, because my decrypted text was repeatededly rejected. Again, this close to cracking it, but too little too late.
- We were provided with two enigmatic strings and an encrypted ZIP file. Had no idea how to proceed with this one just yet.
- We're provided with Python code for a home-brew crypto, as well as some sample data. Given enough time I'm sure I could have figured out the issue at hand, but in this case ${ENOUGH_TIME} would -GT 2d. So never mind ;)
Cracking crypto never was my strong point ;)
Forensics:
- We're given a .CRT certificate for a voting machine, which supposedly is fishing. Making it legible with the OpenSSL command line quickly shows the PvIB CTF flag.
- We're given a .DOCX file which was supposed to contain suspicious data. I simply used unzip to extract all the components files of the Word document and searched the various XML contents for the CTF flag.
- We're given a .PNG image that supposedly contains hidden data. One ZSteg install later I have my flag.
Fun challenges! Not too hard so far.
Misc.:
- A PDF file with some hidden data in it. Open the PDF with the viewer on my Kali box made it stand out as a fat blue box. Anko simply grepped for "-i pvib" through the strings-output of the PDF and fared just as well :)
- Oooff! I wish I'd had my wife with me! She's great at logical reasoning :) This challenge combined logic (determine whether persons A, B and C are lying or tell the truth), math (Fibonacci and Harshad numbers) and programming (because there's no plausible way of quickly solving the puzzle on paper). Seeing how I can't ever get my ideas straight with the liars/truthers, I skipped this one after about half an hour.
What a great evening! Better yet, on the way home I managed to get on the Slam! night show and I won a DAB+ radio for our home! :D Awesome-cakes!
kilala.nl tags:
ctf,
work,
View or add comments (curr. 0)



